Up to date September 9, 2025
UPDATE: Salesforce/Salesloft Integration Is Restored
As of a current replace, the mixing between the Salesloft platform and Salesforce has been restored. Clients shall be contacted immediately by the Salesloft Buyer Success crew to help with the info reconciliation course of earlier than the Salesforce sync is re-enabled
A forensic investigation by Mandiant has shed new gentle on the Salesloft Drift safety incident. After being employed on August 28, 2025, Mandiant investigated the breach and, as of September 6, 2025, has confirmed that the incident is contained.
The investigation’s most essential discovering is that the breach was centered on the Drift utility setting. The separate Salesloft platform was not compromised for knowledge exfiltration, and Mandiant verified the technical segmentation between the 2 programs.
Particulars of the Incident
Mandiant’s investigation discovered that the attacker was energetic primarily between March and June 2025.
The assault unfolded in a transparent, multi-stage course of.
Stage 1: Preliminary entry through GitHub
The attacker first gained entry to Salesloft’s GitHub account. From there, they downloaded content material from a number of code repositories, added a visitor person, and established workflows to keep up their entry.
Stage 2: Reconnaissance
The attacker then carried out reconnaissance in each the Salesloft and Drift utility environments. Nevertheless, the investigation discovered no proof of a deeper compromise inside the core Salesloft utility itself.
Stage 3: Pivot to Drift setting & credential theft
The attacker leveraged their place to entry Drift’s AWS setting. As soon as inside, they stole OAuth tokens for Drift clients’ expertise integrations.
Stage 4: Information exfiltration
Utilizing the stolen OAuth tokens, the attacker accessed buyer knowledge by means of the energetic Drift integrations.
The assault was methodical, with Cloudflare’s investigation exhibiting attacker exercise that included preliminary reconnaissance on August 9, expanded reconnaissance on August 13, and remaining knowledge exfiltration on August 17.Official response and containment actions
Salesloft, with validation from Mandiant, executed a swift and thorough response to comprise the menace.
Drift utility environmentThe Drift infrastructure, utility, and code have been remoted and contained.The Drift Software has been taken offline.All impacted credentials within the Drift setting have been rotated.Salesloft utility environmentCredentials within the Salesloft setting have been proactively rotated.Intensive menace looking was carried out throughout Salesloft infrastructure, and no extra Indicators of Compromise (IOCs) have been discovered.The Salesloft setting was quickly hardened in opposition to the attacker’s strategies.Decision and repair restorationThe integration between the Salesloft platform and Salesforce has been restored.Listing of companies impacted by the Salesloft Drift breach
Victims embody main expertise corporations and several other distinguished cybersecurity distributors.
Firm
Date of Breach
Abstract of affect
BeyondTrust
August 22, 2025
After being alerted by Salesforce to suspicious exercise on August 22, 2025, BeyondTrust confirmed it was impacted by the provision chain incident involving the compromised Salesloft Drift utility.
Bugcrowd
August 22, 2025
An unauthorized celebration gained entry to sure knowledge inside Bugcrowd’s Salesforce setting by means of the compromised Drift utility. The corporate confused that its core platform knowledge, buyer vulnerability particulars, and fee data weren’t affected.
Cato Networks
September 1, 2025
The corporate confirmed that it was affected between August 8-18, 2025. The breach resulted in unauthorized entry to restricted Salesforce knowledge, together with enterprise contact data and fundamental particulars from buyer assist instances.
Cloudflare
August 12, 2025
A menace actor accessed Cloudflare’s Salesforce setting over a five-day interval, from August 12 to August 17, 2025, and exfiltrated knowledge associated to buyer assist instances.
CyberArk
September 4, 2025
The breach concerned unauthorized entry to the corporate’s Salesforce CRM knowledge through the Salesloft Drift provide chain incident. The uncovered data was confined to enterprise contact particulars and metadata from accounts and conversations.
Dynatrace
September 2025
Dynatrace confirmed its Salesforce setting was compromised as a part of the widespread incident, however said the breach was confined to that particular system.
Elastic
August 26, 2025
After investigating the widespread incident disclosed on August 26, 2025, Elastic decided that its personal Salesforce setting was not impacted by the breach.
Esker
August 2025
Attackers leveraged stolen OAuth credentials between August 8 and August 16 to realize restricted entry to Esker’s Salesforce setting. The breach was restricted to the content material of Salesforce assist instances, exposing names, enterprise contact particulars, and the textual content from assist tickets.
Fastly
August 13, 2025
Fastly confirmed that it was focused between August 13 and August 18, 2025, with attackers getting access to its Salesforce occasion as a part of the broader compromise.
Heap
August 22, 2025
Salesforce notified Heap of surprising exercise related to the Drift utility, which steered that an unauthorized celebration might have gained entry to Heap’s Salesforce setting.
JFrog
August 23, 2025
On August 23, 2025, the corporate was knowledgeable by Salesforce about suspicious entry to its Salesforce tenant through the Drift integration. Whereas some Salesforce information have been accessed, the core JFrog Platform and its buyer product knowledge weren’t impacted.
Megaport
August 22, 2025
The incident led to unauthorized entry to a subset of the corporate’s Salesforce knowledge. The publicity was restricted to buyer contact data, equivalent to names and enterprise electronic mail addresses.
Nutanix
August 18, 2025
The corporate confirmed it was impacted by the compromise that focused Salesforce clients worldwide, with attackers gaining unauthorized entry to knowledge inside Salesforce assist instances.
PagerDuty
August 23, 2025
PagerDuty was impacted when attackers exploited the compromised Salesloft Drift OAuth tokens to realize unauthorized entry to Salesforce accounts throughout a number of organizations.
Palo Alto Networks
September 2, 2025
The corporate was certainly one of tons of affected by the provision chain assault. Attackers used stolen OAuth tokens from the Drift integration to entry the Palo Alto Networks Salesforce occasion and extract a restricted quantity of customer-related knowledge.
Proofpoint
August 22, 2025
The corporate’s Salesforce tenant was accessed by an unauthorized celebration that exploited the Drift integration. The breach was first recognized by Salesforce, which detected suspicious exercise tied to Drift.
Qualys
September 6, 2025
Qualys confirmed it was among the many organizations impacted by the provision chain incident, the place attackers used stolen OAuth tokens to realize unauthorized entry to its Salesforce buyer occasion.
Rubrik
August 22, 2025
Following a notification from Salesforce about suspicious exercise on August 22, 2025, Rubrik disclosed that its Salesforce occasion was impacted by the compromised Drift integration.
Sigma Computing
August 22, 2025
The corporate disclosed that it was impacted by the marketing campaign focusing on Salesforce clients. The breach resulted in unauthorized actors accessing Salesforce credential knowledge.
SpyCloud
September 1, 2025
The corporate disclosed that its Salesforce CRM knowledge was probably accessed by attackers who used a compromised OAuth token related to the Salesloft Drift integration.
Tanium
August 28, 2025
The incident concerned attackers acquiring Tanium credentials from Salesloft Drift. These credentials have been then used to realize entry to Tanium’s Salesforce occasion.
Tenable
August 22, 2025
An unauthorized actor gained entry to a restricted set of buyer data inside Tenable’s Salesforce setting as a part of the widespread compromise. The compromised knowledge included topic strains and the preliminary descriptions from buyer assist instances.
Workiva
August 20, 2025
Attackers exfiltrated a restricted quantity of information from the corporate’s Salesforce CRM setting by means of the Drift integration. The uncovered knowledge included enterprise contact particulars equivalent to names and electronic mail addresses. Workiva confirmed its core platform was not compromised.
Zscaler
August 30, 2025
The corporate reported that attackers used stolen OAuth tokens to realize restricted entry to its Salesforce knowledge. The data uncovered included enterprise contact particulars, product licensing data, and the content material from some buyer assist instances.
How to reply to the Salesloft Drift occasion
Given the character of the breach, organizations utilizing Salesloft Drift (particularly these integrating it with third-party platforms like Salesforce) are urged to take rapid motion to mitigate threat and examine for potential compromise.
The first suggestions from safety researchers fall into three fundamental classes: investigation, remediation, and hardening.
1. Examine for Compromise and Scan for ExposureReview integrations: Step one is to assessment all third-party integrations related to your group’s Drift occasion. This may be carried out inside the Drift Admin settings web page.Search logs for malicious exercise: Inside every built-in third-party utility, seek for the Indicators of Compromise (IoCs), equivalent to IP addresses and Person-Agent strings, offered by Google’s Risk Intelligence Group. In Salesforce, this includes reviewing authentication exercise from the Drift Linked App and in search of uncommon RestApi Question occasions.Scan for uncovered secrets and techniques: Actively search your Salesforce objects and different built-in platforms for delicate secrets and techniques that will have been uncovered within the exfiltrated knowledge. The menace actor particularly seemed for credentials associated to Amazon Internet Providers (AWS), Snowflake, and different providers.Salesloft Drift IOCs
Indicator Worth
Description
Salesforce-Multi-Org-Fetcher/1.0
Malicious Person-Agent string
Salesforce-CLI/1.0
Malicious Person-Agent string
python-requests/2.32.4
Person-Agent string
Python/3.11 aiohttp/3.12.15
Person-Agent string
208.68.36.90
DigitalOcean
44.215.108.109
Amazon Internet Providers
154.41.95.2
Tor exit node
176.65.149.100
Tor exit node
179.43.159.198
Tor exit node
185.130.47.58
Tor exit node
185.207.107.130
Tor exit node
185.220.101.133
Tor exit node
185.220.101.143
Tor exit node
185.220.101.164
Tor exit node
185.220.101.167
Tor exit node
185.220.101.169
Tor exit node
185.220.101.180
Tor exit node
185.220.101.185
Tor exit node
185.220.101.33
Tor exit node
192.42.116.179
Tor exit node
192.42.116.20
Tor exit node
194.15.36.117
Tor exit node
195.47.238.178
Tor exit node
195.47.238.83
Tor exit node
2. Revoke and rotate credentialsRotate all related tokens and keys: For each third-party utility built-in with Drift, instantly revoke and rotate all API keys, credentials, and authentication tokens related to the mixing.Rotate uncovered credentials: If the investigation uncovers any hardcoded secrets and techniques or uncovered credentials, they should be rotated instantly. That is essential to forestall the menace actor from utilizing them to compromise different programs.3. Harden entry controls for the futureEnforce the Precept of Least Privilege: Be sure that related purposes like Drift have the minimal essential permissions required to perform. Keep away from granting overly permissive scopes, equivalent to “full” or “api,” to third-party integrations.Limit entry by IP handle: The place attainable, outline trusted IP ranges for related purposes to limit entry to your company community. Okta efficiently blocked this assault as a result of the menace actor’s connection try got here from an unauthorized IP handle.Restrict API entry: In Salesforce, take away the “API Enabled” permission from normal person profiles and grant it solely to licensed customers through a Permission Set.4. Re-enable and Reconcile Integrations
For the Salesforce integration, don’t re-enable the sync instantly. Watch for the Salesloft Buyer Success crew to contact you to information you thru the required knowledge reconciliation steps.
How one can verify should you’ve been impacted by the Salesloft Drift occasion
To verify you probably have been impacted, your safety crew ought to:
Deal with drift-related tokens as compromised: Given the scope of the incident, the most secure strategy is to deal with any authentication tokens saved in or related to the Drift platform as probably compromised.Audit third-party utility logs: Probably the most direct option to verify for affect is to look the audit logs of any utility built-in with Drift for malicious exercise. You need to seek for suspicious queries or entry patterns originating from the IP addresses and Person-Agent strings within the IOC desk above.Evaluate Salesforce authentication and API logs: Particularly, inside Salesforce, directors ought to assessment authentication exercise related to the Drift Linked App and search for uncommon RestApi Question occasions that question 500 or extra information.Why is that this an essential situation for vendor threat administration?
This incident is a key lesson in third-party threat. The attacker’s entry level was a code repository, which they then used to pivot to a associated however separate utility (Drift). This highlights the necessity to scrutinize the safety of all platforms a vendor operates, not simply their fundamental product.
The Salesloft Drift incident highlights a number of essential points for Vendor Danger Administration:
Danger Focus: The assault uncovered the systemic threat created when many organizations depend on a central platform like Salesforce. When a single, broadly used utility built-in with that platform (on this case, Drift) is compromised, it creates a single level of failure with an enormous blast radius, affecting quite a few corporations concurrently — like we noticed within the CrowdStrike incident.Inherent belief is a foul behavior: The assault’s effectiveness relied on the inherent belief that organizations place of their third-party integrations. By hijacking authentic OAuth tokens, the attackers might impersonate the Drift utility, permitting their malicious knowledge exfiltration queries to mix in with common API site visitors and bypass conventional safety instruments.Identification threat is the brand new perimeter: The breach underscores that id compromise is among the many most urgent dangers in SaaS environments. The attackers didn’t want to use a technical vulnerability in Salesforce; they merely wanted to accumulate legitimate credentials — OAuth tokens issued by means of a standard authorization circulate. This demonstrates that a company’s safety is not outlined by its community perimeter however by the safety of all identities and purposes with entry to its knowledge.Everyone seems to be in danger: The checklist of confirmed victims consists of main expertise suppliers and even distinguished cybersecurity distributors like Cloudflare, Palo Alto Networks, and Zscaler. This proves that even organizations with mature safety packages are vulnerable to provide chain assaults, making rigorous third-party cyber threat administration a essential pillar for all cybersecurity packages.How to make sure you are protected in opposition to comparable future assaults
Defending your group from comparable provide chain assaults requires a proactive, defense-in-depth strategy centered on managing third-party utility threat.
Implement the Precept of Least Privilege: A essential first step is to make sure that all third-party integrations, together with Drift, are granted solely the minimal essential permissions to carry out their supposed perform. Keep away from assigning overly permissive scopes like “api” or “full access” to related purposes. If an attacker had compromised a token with fewer privileges, the potential for vital knowledge loss would have been enormously decreased.Implement strict entry controls: Configure related purposes to solely enable entry from trusted IP ranges. This single management prevented the attackers from accessing Okta’s Salesforce occasion. You must also restrict API entry to solely licensed customers by means of using devoted Permission Units slightly than enabling it by default on broad person profiles.Assume breach and rotate credentials: As a matter of coverage, instantly revoke and rotate all credentials, API keys, and authentication tokens for any utility related to a compromised third-party service. Any delicate knowledge or credentials {that a} buyer might have shared with a vendor (e.g., in a assist ticket) ought to be thought-about compromised and rotated instantly.Combine AI into your third-party threat program: Conventional vendor monitoring struggles to maintain tempo with the quickly increasing digital provide chain. Integrating AI into your TPRM workflow bridges this essential visibility hole, making it attainable to trace adjustments to every essential vendor’s safety profile in actual time.How Cybersecurity helps clients reply to the Salesloft Drift breach
Cybersecurity has shipped a lot of updates to assist its clients rapidily reply to the Salesloft Drift provide chain assault:
Quick Salesloft Drift visibility
Clients can now immediately see their publicity to Salesloft Drift wherever it seems of their IT ecosystem, as a detected product of their area community through Breach Danger, and as a fouth-party vendor through Vendor Danger.
Salesloft Drift breach alert in Cybersecurity’s incidents and information feed.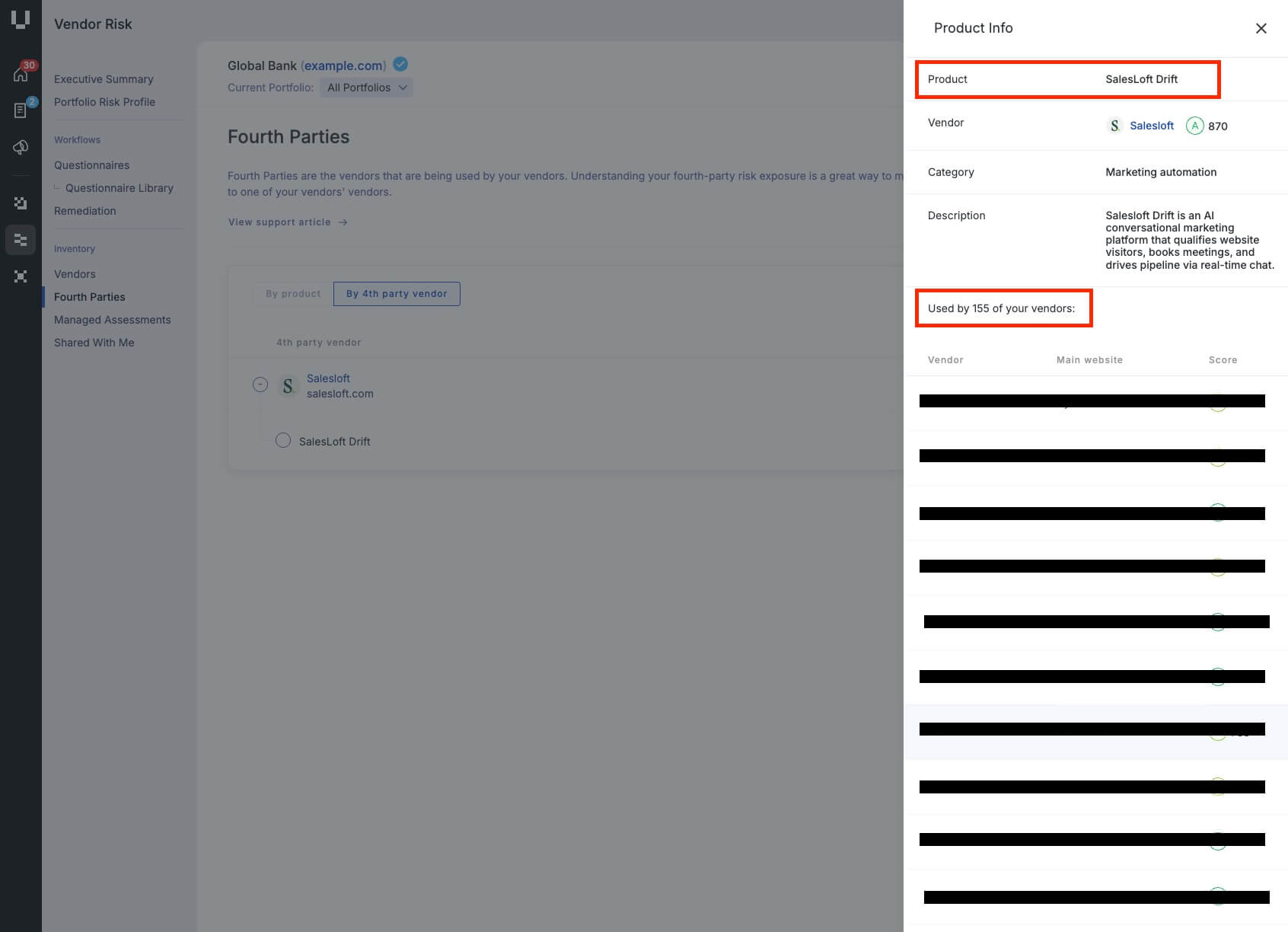 Salesloft Drft detected within the fourth-party vendor on the Cybersecurity platform.Salesloft post-incident affect questionnaire
Salesloft Drft detected within the fourth-party vendor on the Cybersecurity platform.Salesloft post-incident affect questionnaire
This questionnaire helps groups shortly assess potential publicity to this incident, guaranteeing proper data is collected for a extra in-depth affect evaluation.
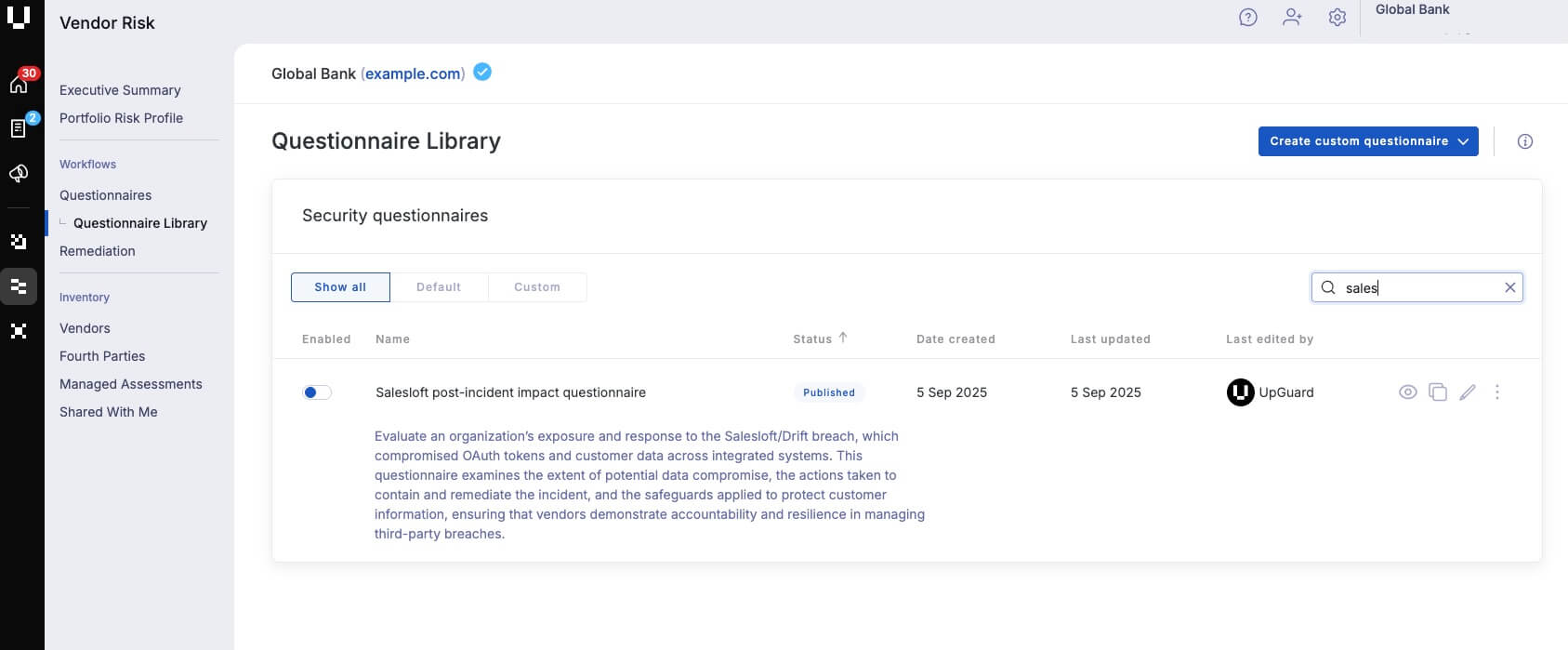 Customizable Salesloft post-incident affect questionnaire template on the Cybersecurity platformHow does Cybersecurity assist safety groups put together for future incidents like this?
Customizable Salesloft post-incident affect questionnaire template on the Cybersecurity platformHow does Cybersecurity assist safety groups put together for future incidents like this?
Cybersecurity offers particular capabilities to assist safety groups scale back the affect of future comparable provide chain assaults:
Fourth-party identification: Cybersecurity detects relationships together with your distributors’ distributors (fourth events), offering essential visibility into your entire digital provide chain to forestall safety gaps from downstream suppliers.Customizable questionnaires: The platform makes use of pre-built and customizable safety questionnaires to conduct due diligence, guaranteeing that distributors meet your group’s particular safety and reliability requirements.Vendor threat classification: Cybersecurity consists of instruments to categorise distributors based mostly on their degree of entry and potential threat, permitting safety groups to focus their sources on probably the most essential third-party relationships.Key doc centralization for incident response: The platform presents a contract repository to retailer important documentation, guaranteeing that response plans, service degree agreements (SLAs), and legal responsibility data are simply accessible throughout an incident.
