In our earlier weblog put up, “Closing the Visibility Gap,” we established that visibility is step one in managing the fashionable human assault floor; nevertheless, prioritizing that knowledge is the subsequent main concern for any CISO. Prioritization of human danger knowledge is important, because it straight informs governance and efficient high-level decision-making. Merely put, prioritization is essential to driving motion.
The present playbook gives little help in that regard, leaving SOC groups with huge swimming pools of information from siloed instruments. Every separate dashboard compounds the issue with its personal set of alerts, forcing leaders to always ask:
How do I do know which groups and people pose the best danger, and the way will we allocate finite sources with precision?
On this put up, we’ll talk about the second side of mitigating human danger in your group: prioritization to allow efficient governance. We’ll study how the normal playbook has faltered beneath the load of contemporary consumer danger, leading to alert fatigue, elevated organizational danger, and a unfavorable enterprise affect.
Lastly, we are going to discover how Person Threat addresses this concern by automated, policy-driven human danger administration.
The necessity for human danger knowledge prioritization
Whether or not you are utilizing the legacy playbook of siloed instruments or have invested in our Person Threat answer, the subsequent step in taking motion based mostly on these insights is prioritization. Past merely seeing particular person knowledge factors, you have to convert them into prioritized danger alerts.
This lets you achieve a complete understanding of your general human danger and take motion the place danger is extra concentrated. A complete view is significant as a result of not all human dangers are equal, and leaders should focus their efforts on customers at greater danger and with higher entry, making this an crucial for contemporary safety groups.
For instance, safety groups have entry to customers’ job roles, permissions, and app utilization knowledge; nevertheless, these are sometimes simply disparate knowledge factors. That is the place contextual prioritization turns into important, because it helps make connections between these alerts and drive motion.
You determine a extremely delicate group—like C-suite members—who’ve entry to important knowledge. You may then overlay which of those customers are additionally utilizing unapproved AI purposes from unmonitored distributors, and which have granted overzealous permissions to these apps.
The core precept is obvious: when singular knowledge factors are translated into prioritized danger alerts, it offers safety leaders with the context and perception wanted to safe their workforce, fine-tune their motion plans, and allocate restricted sources to handle the dangers most crucial to enterprise operations.
Examples of the prioritization insights that drive clear, actionable methods embody:
Coverage violation standing:
Perception: Cross-reference aggregated knowledge in opposition to present safety insurance policies to determine particular violations and non-compliant consumer behaviors.Drives Motion: Pinpoint particular person customers or groups that require rapid remediation or coverage intervention.
Utility approval standing:
Perception: Evaluate utilization knowledge in opposition to the established software safety baseline.Drives motion: Affirm whether or not newly found purposes are sanctioned or permitted to be used, triggering acceptable vetting or blocking actions as wanted.
Rising risk evaluation:
Perception: Monitor the most recent rise in Shadow IT, and extra particularly, Shadow AI (unapproved AI purposes) as detailed in our 2025 Shadow AI report.Drives motion: Quantify the dimensions and severity of those new, unmanaged dangers getting into the group’s perimeter to justify coverage adjustments or know-how funding.
Learn the complete 2025 Shadow AI report right here >
Stakeholder reporting & funding:
Perception: Glean insights to quantify the human danger ranges throughout the group.Drives motion: Manually builds reviews for administration, permitting them to pinpoint obligatory interventions and justify program funding.
Remediation planning and execution:
Perception: Synthesize all prioritized violations, purposes, and risk knowledge throughout the group.Drives motion: Construction and execute clear, prioritized remediation plans that guarantee sources are centered on the highest-risk customers and vulnerabilities, minimizing operational disruption.
Sadly, that is the place the normal playbook falls quick. Safety groups should manually compile all the information factors to align with these prioritization elements to start driving remedial motion. Successfully, safety groups are relegated to appearing as knowledge analysts, investigating alerts and looking for suggestions—losing worthwhile sources that needs to be centered on stopping particular and time-sensitive threats. And this handbook burden does come at a excessive price.
The excessive price of handbook prioritization: Ineffective governance
Prioritizing human danger knowledge manually is a difficult course of, and it typically turns into unattainable when dealing with lots of of danger alerts. This handbook course of poses important organizational issues, starting from operational friction to widespread alert fatigue amongst safety groups, which leaves the door open for important alerts to be missed.
Pictured: The tedious means of investigating and prioritizing consumer danger knowledge manually.
The dearth of a sturdy prioritization mannequin hinders strategic governance, wastes analyst sources, and contributes to unchecked growth of the assault floor, leading to pervasive, unmanaged publicity throughout the group.
Listed below are the true impacts of failing to prioritize, damaged down into the measurable prices to your safety crew and enterprise.
Enterprise affect:
Wasted sources and prices: Excessive-skill, costly safety analysts are pressured to manually export and combination danger knowledge from a number of level options to drive insights, somewhat than specializing in remediating the best affect dangers or performing high-value safety work. This equates to important operational waste.Strategic failure: Leaders can not persistently quantify human danger or successfully perceive the posture of their workforce. This makes it unattainable to display a return on safety funding (ROI) or justify strategic governance to the board.
Threat to enterprise safety:
Alert fatigue: The excessive quantity of scattered, non-prioritized alerts results in alert fatigue, thereby growing the chance that real, important threats will likely be neglected.Elevated assault floor: With out a clear, prioritized motion plan, the speedy progress of SaaS utilization and the rise of generative AI proceed unchecked, increasing the unmanaged portion of the assault floor and growing publicity to knowledge leakage and mental property loss.
Burden positioned on safety groups:
Operational friction: Groups are caught in a relentless state of reactive firefighting and limitless contextual investigations, resulting in burnout and decreased effectiveness.Ineffective governance (No clear path ahead): Leaders wrestle to persistently implement safety insurance policies, as they’re typically buried in paperwork somewhat than built-in right into a system that mechanically triggers alerts and offers real-time teaching.
Clearly, the present playbook struggles to offer visibility; even when it does, the alerts are sometimes unprioritized and require handbook evaluation. And this sluggish, laborious course of results in large organizational and safety deficits that may’t handle the rising scale of the fashionable human danger panorama.
What’s wanted is a single answer that gives visibility and prioritized, actionable knowledge, multi functional consolidated platform. Our latest addition, Person Threat, delivers each. Because the human danger administration platform inside our CRPM ecosystem, it’s designed for the fashionable assault floor, giving groups the insights and path wanted to cut back human danger extra successfully.
The Person Threat motion engine
We have established that prioritization is a elementary requirement for managing the fashionable human assault floor. That is exactly why we’ve made it a core pillar of the Person Threat platform.
Consider Person Threat as an engine that makes use of prioritization to drive motion. It repeatedly aggregates uncooked knowledge from numerous instruments and browser exercise monitoring to maintain a relentless pulse in your human danger perimeter. It then contextualizes and prioritizes all findings in accordance together with your current safety insurance policies and governance guidelines.
This contextualized and prioritized knowledge is then offered inside our Person Threat dashboard to provide a single, unified view of your human assault floor. With this unified view, leaders can rapidly take the mandatory actions based mostly on the findings, successfully automating the tedious facets of governance and driving them from uncooked knowledge to motion in seconds.
Excessive-level prioritization with the Unified Threat Rating
At a excessive degree, we remodel this uncooked, centralized knowledge into a right away motion sign: what we name the Unified Threat Rating. That is the only, quantifiable metric that cuts by the noise and offers absolute readability on consumer danger inside your workforce, per particular person or crew.
This rating instantly solutions essentially the most important operational query: “What should I fix first?”—and who poses the best risk proper now. It solely automates the stakeholder reporting and funding burden by offering administration with a single, clear metric.
The intelligence behind this rating can also be compounding: Person Threat prioritizes your Shadow IT with immediate vendor danger context. It does not simply uncover a brand new Shadow SaaS app; it immediately cross-references it together with your vendor danger program to see if that newly found app is from an permitted, monitored vendor. That is the one platform that transforms a easy discovery right into a prioritized, actionable perception that siloed instruments cannot present.
AI-driven prioritization and granular governance
Visibility and a unified rating are highly effective, however motion requires intelligence. That is the place the AI analyst prioritization function comes into play. As a substitute of treating each sign as equal, our AI takes your outlined safety insurance policies and turns them into dynamic, automated governance guidelines.
This immediately solves the handbook burden of coverage violation standing and rising risk evaluation by automating comparability and quantification.
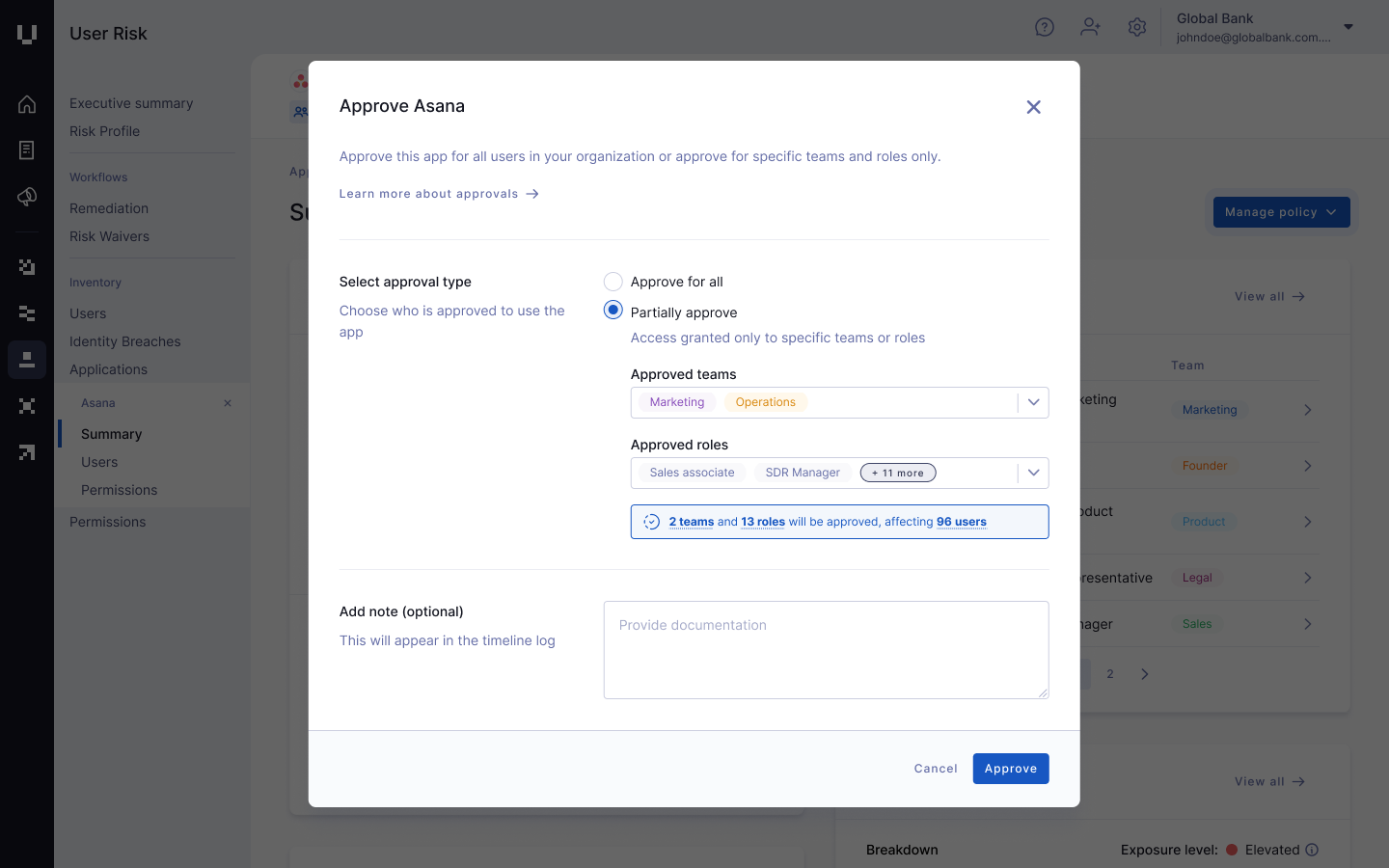 Pictured: Our Person Threat answer permitting for granular SaaS approval for each people and groups.
Pictured: Our Person Threat answer permitting for granular SaaS approval for each people and groups.
This intelligence permits granular SaaS & AI governance, permitting leaders to outline their software safety posture with precision. Leaders can create guidelines that outline which purposes or particular SaaS and AI purposes to approve, prohibit, or monitor based mostly on their danger degree, class, or the groups that use them.
To shut the loop on granular governance, the AI Analyst identifies essentially the most important human dangers based mostly on context, intent, and knowledge publicity, after which offers detailed, actionable remediation recommendation alongside each prioritized danger. This ensures your crew focuses its finite sources on the few threats that genuinely matter.
From reactive to energetic governance
The important thing shift is transferring away from the reactive posture of conventional safety (post-discovery blocking or investigation). Automated danger technology transforms your insurance policies right into a proactive danger detection system that repeatedly analyzes consumer exercise in opposition to your established guidelines, mechanically prioritizing and surfacing dangers when a coverage is violated.
Person Threat permits safety leaders to transition to an energetic, automated governance state, the place insurance policies persistently drive actions throughout the whole human assault floor. This enables safety to handle the continual and rising panorama of human danger, somewhat than always chasing particular person alerts reactively.
This steady cycle of enforcement and monitoring is the one option to handle danger and put together for the final word final step in fixing human danger: lasting habits change.
Prioritize human danger and take motion with Person Threat
Human and workforce dangers are rising because the panorama expands, and the best way we handle danger inside this house is not working. We have mentioned the frequent struggles with each visibility and efficient prioritization, and it is clear that it is time for an answer that provides each to maintain tempo with the growing scale of human danger.
We imagine the time for change is now, and Person Threat is the platform we stand behind as the answer. It offers the engine wanted to take that seen knowledge, remodel it into efficient, automated governance, and at last safe your workforce from the noise of unprioritized danger.
Take a product tour of Person Threat immediately.
