Third-party cyber threat administration (TPCRM) has emerged as a crucial self-discipline, shifting past conventional approaches to deal with the distinctive and evolving cyber threats posed by vendor relationships.
This submit explains the core tenets of TPCRM, outlines key necessities for ultimate instruments, and suggests implementation methods for this new, vital department of cybersecurity.
Definition of TPCRM
Third-party cyber threat administration (TPCRM) is the systematic strategy of figuring out, evaluating, and mitigating cybersecurity-specific dangers related to utilizing third events, corresponding to distributors, suppliers, contractors, and companions.
TPCRM represents a major evolution from conventional third-party threat administration (TPRM). Whereas TPRM addresses a broader spectrum of threat domains, together with monetary, operational, authorized, and reputational considerations, TPCRM is a specialised subset that particularly focuses on cybersecurity and IT-related dangers posed by third-party distributors.
Sturdy TPCRM requires a multi-dimensional method that goes past questionnaires and point-in-time assessments. As third-party ecosystems increase, the exterior assault floor — comprising internet-facing property, misconfigurations, and uncovered knowledge — has turn into an more and more crucial a part of the menace panorama. Efficient TPCRM should account for this rising publicity with steady monitoring and proactive threat identification.
The broad scope and specialisation of TPCRM current distinctive challenges that conventional TPRM practices aren’t outfitted to handle, underscoring the necessity for a devoted cyber threat method. Past monitoring the exterior assault floor, efficient TPCRM contains steady due diligence, management verification, remediation monitoring, and alignment with safety frameworks. It calls for cyber-specific visibility into vendor safety postures.
TPCRM is just not merely TPRM with “cyber” appended, it is a specialised self-discipline tailor-made for the particular complexities of the trendy vendor menace panorama.Variations between TPRM and TPCRM
Organizations should acknowledge that merely relabeling current third-party threat administration (TPRM) applications is inadequate. To remodel a TPRM program right into a TCPRM program, a elementary shift in methodology and know-how adoption is required. At a excessive stage, TPCRM is differentiated by its enlargement of steady monitoring and nth-party vendor detection capabilities.
Broader scope of steady monitoring
Whereas good TPRM applications monitor usually additionally monitor different threat threat domains in addition to cyber dangers, corresponding to monetary and compliance-related dangers, TPCRM applications additional prolong this scope to incorporate different cyber threat domains, corresponding to:
Distant entry vulnerabilitiesCounterfeit productsReputational dangers (stemming from poor safety practices)Malware infectionsThird-party provide chain assaults.
As a result of TPCRM locations a better emphasis on a steady assurance mindset, this system’s steady monitoring part requires a multidimensional method past automated threat scoring.
Such a mannequin usually includes:
Vendor safety questionnaires: Mapping to relevant cyber frameworks and laws, with the choice of customization to broaden the scope of cyber threat domains being queried.Safety score: Repeatedly evaluating exterior get together safety postures with quick refresh charges, to supply real-time consciousness of evolving vendor threat.Notifications: Triggered when vendor safety postures drop under a set threshold, help proactive threat administration responses.Safety profile management checks: Automated checks of a vendor’s safety controls to make sure ongoing alignment along with your safety requirements
Collectively, these capabilities kind an adaptive steady monitoring framework, able to overlaying a variety of cyber threat domains whereas enabling proactive vendor threat identification and administration
Nth-party cyber threat detection
Moreover steady monitoring, one other defining attribute of TPCRM is its concentrate on securing your entire interconnected community of distributors, extending past fast third-party relationships to incorporate fourth events, fifth events, and so forth. This cascade of exterior events is what’s collectively often called your nth-party distributors.
This enlargement of monitoring scope is vital as a result of a vulnerability exploited in a downstream nth-party can create a ripple impact, finally impacting the first group. TPCRM goals to supply visibility into these prolonged digital provide chains, highlighting areas of concentrated threat to help superior threat mitigation efforts — underscoring the need for AI-powered options able to mapping and assessing such complicated, multi-layered relationships.
To additional make clear the distinct focus of TPCRM, the next desk summarizes a number of the key variations from conventional TPRM.
TPRM vs. TPCRM: Key differentiators
Function/Side
Conventional TPRM
Trendy TPCRM
Main Focus
Largely targeted on authorized and compliance threat related to threat domains corresponding to monetary, operational, sustainability, and so on.
Particular to cybersecurity and IT-related dangers.
Threat Scope
Primarily screens first-party distributors
Expands monitoring to Nth events (fourth, fifth, and so on.).
Evaluation Fashion
Typically will depend on point-in-time threat assessments, creating cyber threat blind spots between evaluation schedules.
Characterised by steady monitoring, real-time vendor safety posture monitoring, and dynamic scoring.
Expertise Leverage
Fundamental GRC instruments typically rely upon spreadsheets for questionnaire administration.
Leverages superior AI to streamline your entire third-party threat administration lifecycle—from threat detection to assessments, remediation, and steady monitoring.
Menace Identification
Usually reactive or primarily based on point-in-time knowledge assortment.
Proactive, predictive, pushed by steady intelligence.
Knowledge Depth
Commonplace applications depend on surface-level compliance checks and coverage opinions.
Dives deep into cyber controls, technical vulnerabilities, safety posture, and public belief pages.
Nth Occasion Visibility
Often restricted to first-party distributors (simply your distributors).
Important, with instruments for the invention and mapping of the prolonged provide chain.
Pace of Response
Usually delayed attributable to point-in-time threat monitoring strategies, relying on evaluation schedules.
Speedy, enabled by real-time alerts and automatic workflows.
Why is TPCRM important for digital belief?
Digital belief is the arrogance stakeholders and prospects have that a company will shield the info it’s entrusted to course of. With out enough digital belief, your online business will appear too high-risk to work together with.
When prospects or companions share knowledge along with your firm, they count on you to safeguard it not solely from inner errors but additionally from breaches which may come by way of your distributors. Clients will nonetheless maintain your organization chargeable for failing to guard their knowledge if a breach happens through a vendor.
For stakeholders, prospects, and regulators, a company’s state of third-party safety is more and more changing into a major driver of digital belief.
Stakeholders, prospects, and regulators are more and more changing into conscious of the position distributors play in knowledge breaches. Some research point out that as many as 73% of breach incidents have been attributable to a compromised third-party vendor. As such, a company’s state of third-party safety is more and more changing into a major driver of digital belief.
85% of shoppers need to know an organization’s knowledge and AI insurance policies earlier than shopping for its services or products.
– Supply: 2022 McKinsey survey of 1,300 enterprise leaders and three,000 shoppers globally.
A well-implemented TPCRM framework is important in reassuring stakeholders, prospects, and regulators that a company is properly protected in opposition to cyber threats. It serves as a tangible demonstration of a company’s dedication to sturdy safety practices and diligent oversight of its vendor ecosystem.
Demonstrable TPCRM practices, together with steady monitoring, thorough threat assessments, and well-documented remediation efforts, present the mandatory proof of compliance and accountable knowledge stewardship, fostering buyer confidence that their knowledge is dealt with securely all through your entire vendor lifecycle.
As such, TPCRM transcends cybersecurity. It additionally performs a pivotal position in exterior relationship administration, regulatory adherence, and the general institution of digital belief.
How TPCRM builds digital belief
A contemporary third-party cyber threat administration (TPCRM) program actively builds digital belief by integrating particular controls instantly addressing the safety considerations of stakeholders. That is achieved by way of a five-pillar framework.
TPCRM Pillar
How It Builds Digital Belief
Safety Due Diligence
Ensures each vendor is vetted in opposition to rigorous safety requirements earlier than onboarding, demonstrating an exemplary safety commonplace for brand spanking new and current vendor relationships.
Vendor Stock & Classification
Eliminates blind spots by accounting for third-party and nth-party relationships, displaying stakeholders that no vendor is neglected.
Automated Threat Scoring
Gives goal, data-driven threat metrics for transparency and consistency in evaluations, so belief choices are backed by quantifiable evaluation.
Steady Monitoring
Delivers ongoing oversight of vendor safety postures, detecting points early and sustaining cyber threat resilience confidence between formal audits.
Compliance Alignment
Exhibits that third-party threat controls meet business and regulatory requirements, reinforcing belief with regulators and prospects by way of demonstrated accountability.
1. Safety due diligence
Earlier than a vendor is deemed secure to onboard, they have to endure an intensive due diligence course of to make sure they meet your group’s acceptable cybersecurity requirements.
Frequent practices embrace:
Safety questionnaires or surveys: Distributors reply detailed questions on their safety insurance policies, infrastructure, incident historical past, compliance certifications, and so on.Proof assortment: Reviewing paperwork like SOC 2 experiences, ISO 27001 certificates, penetration take a look at outcomes, or belief pages.Threat assessments: For top-risk distributors, carry out a extra in-depth audit or evaluation of their safety program in opposition to your requirements.Threat rankings and evaluation: Evaluating the seller’s responses and proof to determine gaps (e.g., lacking encryption, weak entry controls) and decide a threat stage.
This proactive method of totally vetting third events earlier than they’re given entry to your knowledge highlights the zero-trust lens by way of which all vendor relationships are ruled in a TPCRM program. Even after a vendor is deemed secure to onboard, belief is just not assumed by default, ongoing authentication remains to be required all through the connection lifecycle.
Making use of Zero Belief rules to third-party relationships may contain:
Requiring distributors to authenticate through multi-factor authentication (MFA) earlier than accessing any inner programs.Segmenting the community to make sure every vendor’s stage of entry to programs and knowledge is the minimal required to carry out their contractual features.Monitoring vendor entry actions in actual time, flagging anomalies or unauthorized habits.Frequently reviewing all vendor connections to make sure predetermined entry limits are maintained. Guaranteeing all entry factors are instantly disabled for all offboarded distributors, ideally routinely.
Moreover, as extra distributors combine AI into their operations, due diligence should prolong to Moral AI Governance, assessing potential algorithmic bias, mannequin safety, and regulatory alignment.
2. Vendor stock and classification
After onboarding, all distributors are meticulously accounted for in a centralized repository. Every vendor within the stock must be categorised into threat tiers primarily based on the extent of threat they pose to your group, starting from crucial to low threat.
All distributors with entry to buyer knowledge must be routinely categorised as “critical.” Distributors that won’t trigger regulatory infractions ought to they turn into compromised could be assigned to a low-risk tier (e.g., a landscaping service).
Excessive-risk distributors might want to endure periodic complete threat assessments.How an up-to-date vendor stock and threat classification builds digital belief
Sustaining a single supply of reality for vendor info ensures no blind spots in your third-party assault floor. When mixed with threat classification, stakeholders have full confidence that a company is just not solely monitoring all exterior partnerships, but additionally fastidiously monitoring the influence of high-risk distributors.
3. Automated threat scoring and vendor rankings
Manually reviewing a whole bunch of distributors is a monumental job. Many fashionable TPCRM applications leverage instruments that calculate a safety score or threat rating for every vendor, utilizing a mixture of evaluation knowledge and exterior menace intelligence.
For instance, a platform would possibly analyze a vendor’s questionnaire solutions and scan for identified vulnerabilities or breaches within the vendor’s internet-facing programs, then produce a rating (e.g., 0-100 or a letter grade) indicating the seller’s cyber threat posture.
Automated scoring brings consistency and pace to threat evaluation. As an alternative of relying solely on subjective judgment, you get data-driven insights into which distributors pose the very best threat. A low rating would possibly flag insufficient safety hygiene or previous incidents, prompting fast follow-up. Conversely, a excessive rating can reassure you {that a} vendor follows good practices.
AI-driven threat analytics additional sharpen the accuracy of threat scores by figuring out refined threat indicators and detecting threat patterns at scale, finally leading to diminished time-to-remediation.
How automated threat scoring builds digital belief
Threat scores present a clear, goal metric to share with management and distributors. Through the use of quantified threat rankings, organizations can show a rigorous, quantifiable method to managing vendor safety, additional reinforcing belief with auditors and executives that third-party threat is underneath management.
4. Steady monitoring and menace detection
Cyber threat is just not static. A vendor that was safe final quarter may endure a breach tomorrow, or regularly weaken in safety posture over time. Steady monitoring is due to this fact foundational to TPCRM.
Steady monitoring is not restricted to monitoring particular person vendor safety postures, it must also embrace monitoring the whole scope of safety threat generally linked to knowledge breaches, together with knowledge dumps on the darkish internet and ransomware boards—a generally neglected assault vector class.
Steady monitoring may contain the next knowledge feeds:
Automated alerts for safety modifications: Getting notified if a vendor’s safety score drops, if their area is present in an information breach dump, or if new vulnerabilities of their programs turn into public.Menace intelligence feeds: Monitoring the darkish internet or open sources for information of assaults or leaked knowledge impacting your digital provide chain.Integration with IT programs: Utilizing zero-trust community instruments to trace vendor entry in actual time..How steady monitoring builds digital belief
Steady monitoring helps dynamic enforcement of Zero Belief. It demonstrates to stakeholders that you just’re not blindly trusting onboarded distributors to take care of alignment along with your cybersecurity requirements, you are repeatedly verifying and monitoring their safety efficiency.
5. Compliance and regulatory alignment
Trendy enterprises should align their TPCRM efforts with an ever-growing checklist of cybersecurity laws and business requirements. Compliance alignment is thus a key part of the TPCRM framework. This includes mapping your third-party threat controls and actions to necessities corresponding to:
Knowledge safety legal guidelines: Laws like GDPR, HIPAA, CCPA, PCI-DSS, and others mandate excessive safety requirements for vendor relationships involving delicate knowledge, and a few of these legal guidelines may maintain you accountable for third-party knowledge breaches.Business requirements and frameworks: Frameworks like ISO 27001, NIST Cybersecurity Framework, SOC 2 Belief Companies Standards, and others all embrace sections on third-party threat administration. To be compliant or licensed, you need to show that you just assess and monitor vendor safety.Inner insurance policies: Aligning along with your group’s threat urge for food and safety insurance policies. As an illustration, in case your coverage says all crucial distributors should have an up-to-date SOC 2 report or multi-factor authentication, your TPCRM program ought to guarantee these checks are in place.
A robust TPCRM program will incorporate compliance checks into its processes. This would possibly imply having commonplace vendor safety necessities that mirror regulatory requirements and monitoring every vendor’s compliance standing. Many TPCRM instruments help with this by monitoring vendor certifications, compliance knowledge, and mapping questionnaire responses to particular regulatory necessities.
When a regulator or auditor comes knocking, you need to have the ability to produce proof that you just’re managing third-party cyber threat according to required practices.How compliance and regulatory alignment construct digital belief
Demonstrating compliance is not nearly avoiding fines. It proves to prospects and potential companions that your group takes knowledge stewardship significantly, regardless of who’s dealing with it. Verifiable compliance is among the strongest indicators of digital belief.
Steps to implement TPCRM
Implementing an efficient third-party cyber threat administration (TPCRM) program is a structured, cyclical course of. The next steps present a sensible roadmap, serving to you identify or mature your TPCRM capabilities.
1. Determine key distributors (together with Nth events)
The foundational step in any TPCRM program is creating and sustaining a complete stock of all third-party distributors, suppliers, and companions interacting along with your group’s programs, knowledge, or crucial providers. This stock should prolong past direct (first-tier) relationships to determine crucial Nth events (fourth-parties, fifth-parties, and so on) throughout the digital provide chain, as these oblique connections can even introduce important threat.
For every recognized entity, it is essential to doc the particular providers they supply, the extent and kind of information they entry or course of, corresponding to PII, PHI, or monetary knowledge, which is especially vital for companies in a highly-regulated sector, like finance.
As soon as the stock is established, distributors must be categorized or tiered primarily based on their inherent threat stage. A standard method includes classifying distributors into tiers (e.g., Tier 1 for top criticality and excessive threat, Tier 2 for medium, Tier 3 for low).
This prioritization is often primarily based on elements such because the sensitivity of information being accessed, the potential influence on crucial enterprise features if the seller’s providers are disrupted, and the seller’s relevance to particular regulatory necessities (e.g., GDPR, HIPAA, PCI DSS).
Instance of vendor tiering on the Cybersecurity platformAutomation can prevent important time with this effort and enhance consistency throughout tiering processes, notably when onboarding many distributors.2. Conduct complete threat assessments
A multi-faceted evaluation method is really helpful for a holistic and dependable view of vendor threat, as no single methodology offers a whole image. Questionnaires are self-attested and could be subjective or outdated; safety rankings provide an exterior perspective however could not seize inner management deficiencies; and technical assessments are sometimes point-in-time evaluations.
Combining these strategies permits for knowledge triangulation, resulting in a extra sturdy and validated threat profile.
A multi-faceted threat evaluation method could embrace:
Safety Questionnaires: Distribute detailed, usually custom-made, safety questionnaires (e.g., primarily based on frameworks like SIG, CAIQ, or bespoke templates) to assemble in-depth details about the seller’s safety insurance policies, carried out controls, incident response capabilities, knowledge safety practices, and compliance certifications.Safety Rankings: Make the most of goal, data-driven safety rankings to symbolize every vendor’s safety posture with a quantifiable rating. Technical Assessments: This will contain reviewing penetration take a look at outcomes, vulnerability scan experiences, and impartial audit experiences (e.g., SOC 2 Sort II, ISO 27001 certificates) supplied by the seller. Organizations would possibly conduct their very own restricted technical assessments or on-site assessments the place acceptable and for very high-risk distributors.
Based mostly on the aggregated outcomes from these evaluation actions, assign every vendor a quantifiable cyber threat score or rating. Scoring ensures a constant method to threat prioritizing throughout remediation efforts.
Organizations ought to search for TPCRM platforms that may ingest and correlate knowledge from a number of cyber threat analysis sources, corresponding to questionnaires and threat assessments, to supply a unified view of every vendor’s evolving threat posture.
3. Set up threat mitigation measures
As soon as dangers are recognized and distributors are rated, the subsequent step is to implement acceptable threat mitigation methods and controls tailor-made to every vendor’s stage of threat.
Threat mitigation works greatest when it is collaborative. When you’re always imposing controls, revise your onboarding workflow. Distributors ought to perceive and align along with your Third-Occasion Cyber Threat Administration expectations from day one.
A TPCRM platform with built-in vendor collaboration instruments will simplify the remediation course of. Watch this video to see how Cybersecurity integrates vendor collaboration options into its workflow.
Efficient threat mitigation measures embrace:
Contractual Agreements: Embed sturdy safety clauses inside all vendor contracts. These clauses ought to clearly outline knowledge safety obligations, mandate adherence to particular safety requirements and controls, define compliance necessities (e.g., with GDPR, HIPAA), set up clear breach notification timelines and procedures, and embrace the group’s proper to audit the seller’s safety practices. Service Stage Agreements (SLAs) for safety efficiency, corresponding to incident response instances and system uptime, must also be specified.Safety Controls Implementation: Based mostly on the dangers recognized, require distributors to implement or improve particular safety controls. This might embrace mandating multi-factor authentication (MFA) for entry to your programs, knowledge encryption at relaxation and in transit, particular community segmentation, or adherence to safe coding practices.Threat Therapy Selections: For every important recognized threat, a proper threat remedy resolution must be made. Choices usually embrace:Mitigate: Apply controls to scale back the probability or influence of the danger.Switch: Shift a number of the monetary influence of the danger to a 3rd get together, usually by way of cyber insurance coverage (although this doesn’t absolve your group of its accountability for due diligence or reputational injury).Keep away from: If the danger is simply too excessive and can’t be adequately mitigated to an appropriate stage, the group could determine to terminate the connection with the seller or not interact with them within the first place.Settle for: For low-level dangers that fall throughout the group’s outlined threat urge for food, a proper resolution to simply accept the danger could also be made, usually requiring sign-off from acceptable administration.Remediation Plans: When vulnerabilities or management gaps are recognized, work collaboratively with distributors to develop clear remediation plans. These plans ought to embrace particular actions, timelines, and obligations. Observe the progress of those remediation efforts and confirm that vulnerabilities are successfully closed.
Threat mitigation measures must be built-in into your third-party threat evaluation workflow. Watch this video to learn the way Cybersecurity incorporates this part in a single vendor threat evaluation lifecycle.
Get a free trial of Cybersecurity >
4. Combine steady monitoring
TPCRM can’t be efficient if it depends solely on point-in-time assessments. The dynamic nature of cyber threats and the evolving safety postures of distributors necessitate the mixing of steady monitoring instruments and processes. This includes monitoring vendor safety efficiency, compliance standing, and rising threats in real-time.
Key points of steady monitoring embrace:
Scope of Monitoring: Repeatedly monitor modifications in vendor safety rankings, new publicly disclosed vulnerabilities affecting the seller or their know-how stack, experiences of information breaches involving the seller, drifts of their compliance standing, and different related threat indicators. This offers correct, up-to-date threat knowledge, which is essential for monitoring vendor knowledge safety and community safety to stop breaches.Automated Alerts: Configure monitoring programs to generate automated alerts for important unfavourable modifications in a vendor’s threat profile or upon detection of a safety incident associated to the seller. .Proactive Protection: Steady monitoring transforms TPCRM from a reactive, rear-view mirror perspective to a forward-looking, proactive protection, permitting well timed intervention earlier than a possible threat materializes into an precise incident. Organizations failing to implement sturdy steady monitoring are basically accepting intervals of blindness to potential threats, considerably rising their threat publicity.5. Assessment and evolve usually
A TPCRM program is just not static. It have to be an evolving part of the group’s total threat administration technique. This requires common assessment and adaptation to stay efficient in opposition to the always altering menace panorama, evolving enterprise aims, and new regulatory necessities.
An evolving TPCRM program is a studying program, repeatedly refining its defenses primarily based on previous experiences, present intelligence, and future projections.
Key actions for program assessment and evolution embrace:
Knowledge-Pushed Evaluation: Make the most of the info and metrics generated by TPCRM actions to objectively assess program effectiveness, determine areas for enchancment, and show worth to stakeholders. Vital metrics embrace the variety of recognized versus mitigated dangers, the price of managing third-party dangers, imply time to detect (MTTD) and imply time to remediate (MTTR) vendor vulnerabilities, tendencies in vendor safety rankings, compliance adherence charges, and imply time to onboard (MTTO) new distributors.Take into account Worth at Threat (VaR): When prioritizing evaluation efforts and allocating mitigation assets, take into account the “value at risk.” This includes evaluating the potential monetary influence of enterprise disruptions, knowledge loss, or different materials penalties stemming from a vendor-related incident. Concentrate on distributors that pose the best potential financial and operational loss to the group; they need to all be grouped in your most important tier.Strategic Prioritization of Assessments: Make use of full portfolio visibility and complete threat intelligence to strategically prioritize distributors requiring complete threat assessments. That is more practical than assessing all distributors equally or counting on simplistic standards like contract dimension or annual spend, because it ensures environment friendly useful resource allocation.Maturity Fashions: Leverage established TPRM maturity fashions to benchmark present program capabilities, determine gaps, and develop a roadmap for progressive enhancements towards a extra proactive and resilient state.Formal Assessment Course of: Set up a proper, periodic course of for reviewing the TPCRM program. This assessment ought to incorporate classes discovered from previous incidents or close to misses, new menace intelligence, modifications within the regulatory panorama, and shifts within the group’s enterprise technique or third-party threat urge for food.Greatest practices for TPCRM
Attaining constant vendor threat discount and fostering digital belief requires adherence to confirmed Third-Occasion Cyber Threat Administration (TPCRM) greatest practices. The next practices will make it easier to set up a scalable, repeatable, and efficient TPCRM program.
1. Centralize your vendor administration and standardize processes
A cornerstone of efficient TPCRM is centralized vendor administration. This includes sustaining a unified, up-to-date stock and threat profile for each third-party relationship.
Accompanying this must be standardized processes for your entire vendor lifecycle, from preliminary analysis and onboarding by way of ongoing monitoring to eventual offboarding. Such standardization ensures consistency and that crucial steps should not neglected, particularly because the variety of distributors grows, making ad-hoc approaches unmanageable.
2. Undertake a risk-based tiering mannequin
Threat-based tiering is a crucial greatest observe that ensures environment friendly safety useful resource allocation to high-risk distributors. By categorizing distributors primarily based on elements corresponding to knowledge entry, service criticality, and potential monetary influence, organizations can prioritize due diligence and monitoring efforts the place they may have probably the most influence.
3. Clearly outline roles and obligations
Clearly outlined roles and obligations for TPCRM actions throughout varied departments, corresponding to procurement, IT, authorized, and enterprise items, are important to stop duties from falling by way of the cracks and guarantee accountability.
4. Leverage automation
Automation must be leveraged wherever possible to deal with repetitive duties like knowledge assortment, questionnaire distribution, fundamental safety checks, and alert technology. This not solely improves effectivity and consistency but additionally frees up safety personnel for extra strategic threat evaluation and mitigation planning.
Trendy TPCRM instruments obtain an optimum steadiness between automation and person oversight, serving to you obtain scalable influence whereas sustaining full management within the driver’s seat.
5. Foster a security-aware tradition by way of ongoing safety schooling
Efficient TPCRM additionally closely depends on fostering a security-aware tradition that extends to vendor relationships. Whereas organizations usually don’t present formal safety coaching to their exterior distributors, selling ongoing communication and safety schooling is paramount.
This includes clearly speaking your group’s safety requirements, insurance policies, and expectations to all third events from the outset of the connection. Sharing related, anonymized menace intelligence that might influence the seller (and by extension, your group) can foster a collaborative safety surroundings.
Most significantly, distributors must be inspired to disrupt the pattern of poor vendor safety hygiene by investing in a sturdy Human Threat Administration program.
6. Undertake and make the most of cybersecurity frameworks
Established cybersecurity frameworks present the important blueprints for constructing a defensible and efficient TPCRM program. Frameworks just like the NIST Cybersecurity Framework (CSF), ISO 27001, and, notably for healthcare, the HITRUST CSF provide structured, complete, and extensively accepted units of controls and greatest practices.
The NIST CSF presents a high-level construction for figuring out, defending, detecting, responding to, and recovering from cyber threats, which could be successfully tailored for evaluating vendor capabilities. Particular NIST publications like SP 800-53 (safety and privateness controls) and SP 800-161 (cybersecurity provide chain threat administration) present extra granular steering.ISO 27001 is the worldwide commonplace for Data Safety Administration Techniques (ISMS). Assessing distributors in opposition to ISO 27001 controls or verifying their certification offers a robust indicator of their safety maturity. ISO 27036 particularly addresses info safety for provider relationships.The HITRUST CSF is especially useful within the healthcare sector because it harmonizes a number of requirements (together with NIST and ISO) right into a single, certifiable framework, emphasizing steady monitoring and validation of controls. Aligning TPCRM practices with these frameworks demonstrates a dedication to business greatest practices, facilitates regulatory compliance, and offers a typical language and constant standards for assessing vendor safety postures, making comparisons extra significant and threat administration extra sturdy.
Here is a useful desk summarizing how TPCRM helps alignment with key compliance and cyber framework requirements.
Key compliance frameworks & TPCRM alignment
Framework
Key Knowledge Safety/Safety Requirement Instance
How TPCRM Helps Align
GDPR (Normal Knowledge Safety Regulation)
Artwork. 28: Processors (distributors) should implement acceptable technical and organizational measures; necessary Knowledge Processing Agreements (DPAs).
Facilitates due diligence on vendor GDPR readiness, automates DPA monitoring and administration, screens vendor knowledge safety controls, and helps breach notification processes.
NIST Cybersecurity Framework (CSF)
Core Features: Determine, Defend, Detect, Reply, Get well utilized to third-party dangers.
Gives a construction for assessing vendor capabilities throughout all CSF features, allows steady monitoring for menace detection, and helps collaborative incident response planning with distributors.
PCI DSS (Cost Card Business Knowledge Safety Commonplace)
Req. 12.8: Keep a program to watch service suppliers’ PCI DSS compliance; Req. 8.3: Safe distant entry for distributors.
Assesses vendor PCI DSS compliance standing (e.g., AOC assessment), screens for vulnerabilities in vendor environments dealing with cardholder knowledge, and verifies safe entry controls for distributors.
ISO 27001 (Data Safety Administration)
Annex A controls associated to provider relationships (A.15), entry management (A.9), and incident administration (A.16).
Validates vendor ISO 27001 certification standing, maps vendor-provided proof to particular ISO controls, and screens for ongoing effectiveness of vendor ISMS.
HIPAA (Well being Insurance coverage Portability and Accountability Act)
Safety Rule: Enterprise affiliate agreements (BAAs) require safeguards for ePHI, together with administrative, bodily, and technical safeguards.
Manages BAAs with distributors, assesses vendor implementation of HIPAA-required safeguards for Protected Well being Data (PHI), and screens for breaches of PHI by distributors.
HITRUST CSF
Complete, prescriptive controls overlaying safety and privateness, requiring third-party assurance and validation.
Leverages HITRUST assessments and certifications for healthcare distributors, ensures sturdy controls for PHI safety are in place, and helps steady validation of vendor compliance.
Instruments and applied sciences for TPCRM
The complexity and scale of contemporary vendor ecosystems necessitate utilizing specialised instruments and applied sciences to handle third-party cyber threat successfully. These options provide capabilities that automate processes, present deeper insights, and allow proactive threat administration, finally contributing to the institution of digital belief.
Key capabilities present in superior TPCRM platforms embrace:
1. AI-driven scoring
Synthetic intelligence and machine studying algorithms are more and more used to investigate massive portions of information from numerous sources. This contains safety rankings, vendor questionnaire responses, menace intelligence feeds, and even publicly out there info.
The AI then generates dynamic, goal threat scores for every vendor, serving to organizations rapidly determine and prioritize their highest-risk relationships. This data-driven method strikes past subjective assessments to supply a extra constant and scalable methodology for evaluating vendor cyber dangers.
The mechanisms behind AI-driven scoring may also be utilized to scale the detection of safety management gaps to streamline vendor threat assessments, addressing the compliance aligment aims of TPCRM.
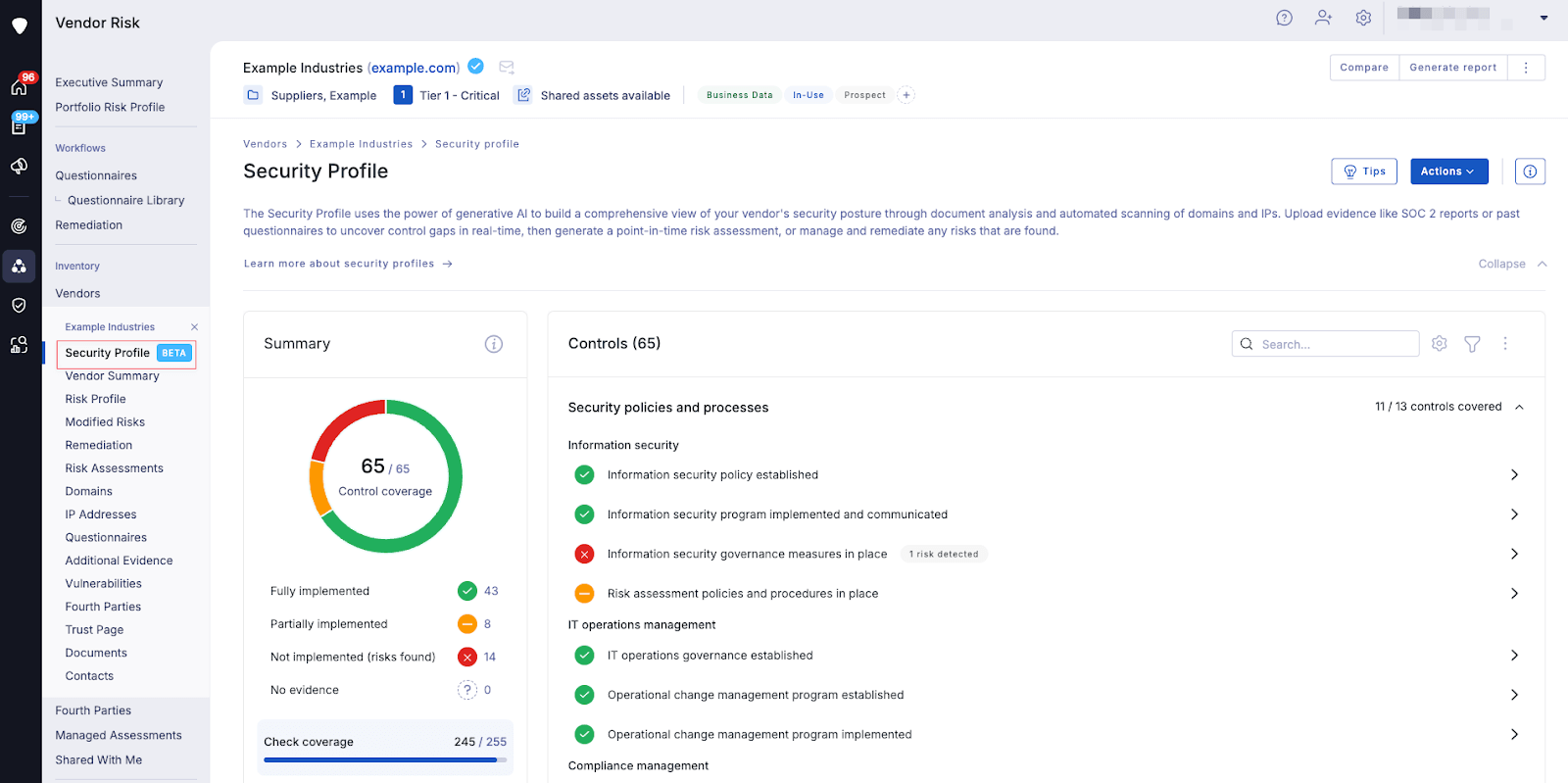 AI-driven vendor scoring and safety management hole detection on the Cybersecurity platform.2. Automated workflows
AI-driven vendor scoring and safety management hole detection on the Cybersecurity platform.2. Automated workflows
Automation is essential for streamlining the quite a few processes concerned in TPCRM. This contains automating vendor onboarding, the distribution and assortment of safety questionnaires, the preliminary evaluation of evaluation responses, the technology of threat alerts, and the monitoring of remediation efforts. Automated workflows improve effectivity, scale back guide effort, guarantee consistency, and permit safety groups to concentrate on extra strategic threat mitigation actions.
For an instance of how a TPCRM answer like Cybersecurity leverages automation in its workflows, watch this video:
Learn the way Cybersecurity transforms TPRM with AI.
3. Built-in breach notifications and menace Intelligence
Trendy TPCRM instruments usually combine exterior menace intelligence feeds to supply well timed alerts of safety incidents impacting your vendor ecosystem. Such integrations allow proactive threat mitigation, serving to you safe your public-facing property as a brand new menace spreads all through the worldwide vendor ecosystem, and never within the aftermath.
The CrowdStrike incident is a latest instance a serious safety occasion impacting the seller ecosystem that customers with entry to a menace intellignece feed have been in a position to effectively reply to.
 Newsfeed highlighting all of an organization’s distributors impacted by the CrowdStrike incident on the Cybersecurity platform.4. Unified dashboards and reporting
Newsfeed highlighting all of an organization’s distributors impacted by the CrowdStrike incident on the Cybersecurity platform.4. Unified dashboards and reporting
Centralized dashboards provide a real-time, consolidated view of the group’s total vendor threat posture. These dashboards may show particular person vendor threat scores, the standing of ongoing assessments, excellent remediation duties, compliance ranges, and the distribution of crucial distributors within the third-party community, represented in a vendor threat matrix.
This unified visibility facilitates knowledgeable decision-making for safety leaders and offers useful reporting for government administration and boards.
 Threat matrix demonstrating distribution of crucial distributors in Cybersecurity’s vendor report.FAQs about TPCRM
Threat matrix demonstrating distribution of crucial distributors in Cybersecurity’s vendor report.FAQs about TPCRM
As third-party cyber threat administration (TPCRM) turns into more and more crucial, a number of frequent questions come up. Addressing these helps make clear the scope, applicability, and core parts of a contemporary TPCRM program.
What’s the distinction between TPRM and TPCRM?
TPRM (third-party threat administration) is a broad observe that manages all forms of dangers posed by third-party relationships, together with monetary, operational, strategic, and compliance dangers.
TPCRM (third-party cyber threat administration) is a targeted subset of TPRM that offers particularly with cybersecurity dangers spanning third and nth-party distributors.
Can small companies profit from TPCRM?
Sure, completely. Small companies additionally depend on third-party software program, cloud providers, contractors, and suppliers, and any of those may introduce a cyber threat.
A small enterprise is probably going a vendor for a bigger group, and by leveraging TPCRM rules to enhance its total safety posture, a small enterprise reduces the danger of changing into an assault vector to a large-scale knowledge breach.
Is steady monitoring necessary in TPCRM?
From a best-practice perspective, steady monitoring is taken into account a cornerstone of efficient TPCRM.
Cyber dangers can evolve rapidly; a vendor that was safe at onboarding may be compromised a month later. With out steady monitoring, issues would solely be found on the subsequent scheduled threat evaluation (or after a breach occurs).
Reinforcing digital belief with a contemporary TPCRM program
A contemporary third-party cyber threat administration (TPCRM) program is vital to advancing company safety maturity in the direction of a proactive method to managing provide chain dangers by embedding threat consciousness into each stage of the seller lifecycle.
The muse of this evolution lies in automation and real-time threat intelligence, which ship the visibility and contextualization required for sooner, extra knowledgeable decision-making. With these capabilities, safety groups are higher outfitted to help digital transformation initiatives whereas sustaining operational resilience.
To future-proof this technique, organizations have to be able to addressing stakeholder considerations about evolving third-party assault threats, specifically the rising adoption of AI know-how and the delicate third-party cyberattacks that can seemingly end result from this transformation.
This might contain making use of Zero-Belief Structure to all third-party entry factors and clear moral AI pointers governing how distributors develop and deploy AI programs, specializing in equity and transparency. Seamless cross-board compliance integrations may even seemingly turn into important to help knowledge safety compliance throughout jurisdictions with out sacrificing the agile traits of TPCRM.
When these components are built-in right into a unified TPCRM method, organizations not solely scale back their publicity to evolving vendor-related cyber dangers but additionally rework their third-party safety right into a strategic enabler of innovation, development, and long-term aggressive benefit.
