The quicker an identification breach is detected, the quicker a company can take steps to cut back the affect of the info breach. Quicker detection occasions and notifications to impacted employees and organizations can lead to decrease information breach restoration prices and assist save an organization’s popularity.
Id breaches are a sort of information leak wherein worker identities and credentials have been stolen or uncovered, which may probably cripple a complete group or trigger extreme monetary and reputational injury. With billions of pages on the web to scan, it’s crucial for organizations to make use of an inside identification breach detection instrument or service, comparable to Cybersecurity Breach Danger.
Cybersecurity provides an Id Breach module inside its Breach Danger product to assist organizations establish any third-party identification breaches which were uncovered on the web, what info has been uncovered, and the scope of the safety breach.
What’s an Id Breach?
An identification breach is a cybercrime assault the place a hacker or cybercriminal obtains delicate info, like personally identifiable info (PII), social safety numbers, monetary info, bank card info, login credentials, or medical and affected person information, by felony means. Risk actors could use any variety of strategies to breach identities, mostly by:
As soon as the identification has been uncovered or stolen, hackers can use the stolen reputable credentials to entry a company’s most necessary information. As soon as the hacker is within the community and techniques, it may be a lot tougher to detect as entry will appear reputable and approved.
Id Breach vs. Id Theft
Id breaches and identification theft are very related, with one main distinction — breaches are sometimes a lot wider in scope and are carried out utilizing cyber assault means. Breaches can have an effect on complete firms when worker credentials have been uncovered, and organizational techniques and belongings are put in danger. If delicate information is efficiently stolen or exfiltrated, cybercriminals can try and ransom that information again to the enterprise, promote it on the darkish internet, or expose it to the general public.
Id theft is often confined to a single particular person the place stolen private information is used to commit fraud or theft. Though the affect is often a lot smaller, identification theft injury can nonetheless be extraordinarily extreme, relying on the standing of the compromised particular person. Usually, identification thieves search to steal identities for financial causes.
How To Detect Id Breaches
Id breaches can happen by varied bodily or digital strategies so it’s necessary to acknowledge early indicators of a breach as a way to report it to the related authorities and firm executives. A few of the commonest indicators a breach has affected you’re:
Improper entry of restricted information, belongings, or systemsSuspicious community and person activitySudden spike in obtain exercise or repeated makes an attempt to entry restricted dataHacked or stolen credentials resulting in unauthorized authentication notificationsIrregular communications with different people or coworkersUnusual calls for or requests from executives or different coworkersExposed credentials surfacing on public or darkish internet forumsIdentity breach experiences from inside assault floor monitoring toolsDetecting Id Breaches with Cybersecurity Breach Danger
Having a devoted cybersecurity resolution to handle inside assault surfaces may help firms detect identification breaches a lot quicker, save numerous hours, and most significantly, forestall expensive restoration and remediation from uncovered information. Devoted options, comparable to Cybersecurity Breach Danger, assist organizations acquire higher visibility of their complete danger profile, permitting them to provoke danger mitigation and remediation processes early on.
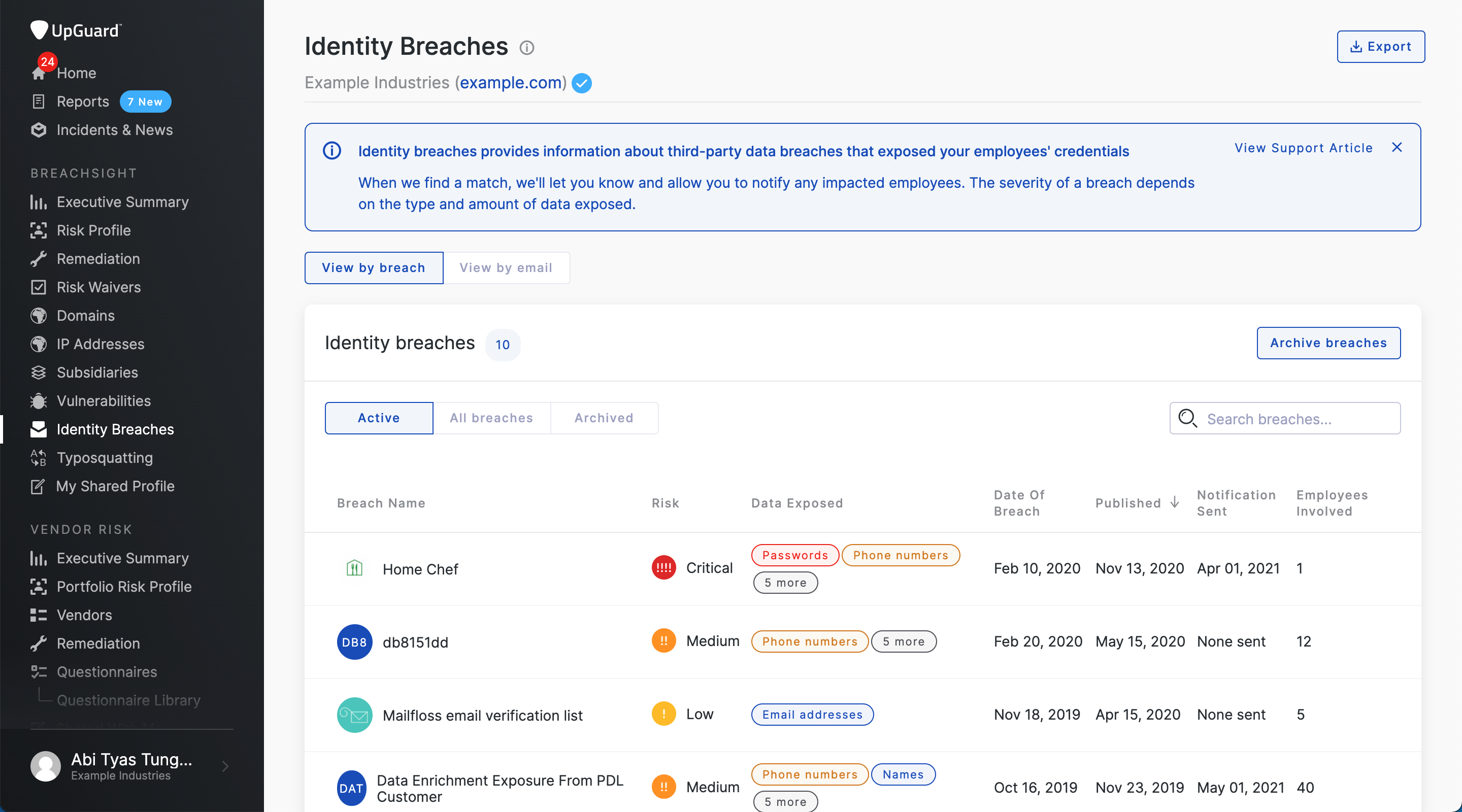
Cybersecurity Breach Danger’s Id Breach module crawls the web for third-party information breaches and identifies the place an worker’s credentials have been uncovered in real-time. All recognized matches are routinely populated throughout the module together with the next information factors:
Title of breached companyBreach detailsSeverity of breachDate of breachDate publishedTotal staff involvedTotal VIPs involvedType and quantity of information exposedNotifications sentCurrent breach standing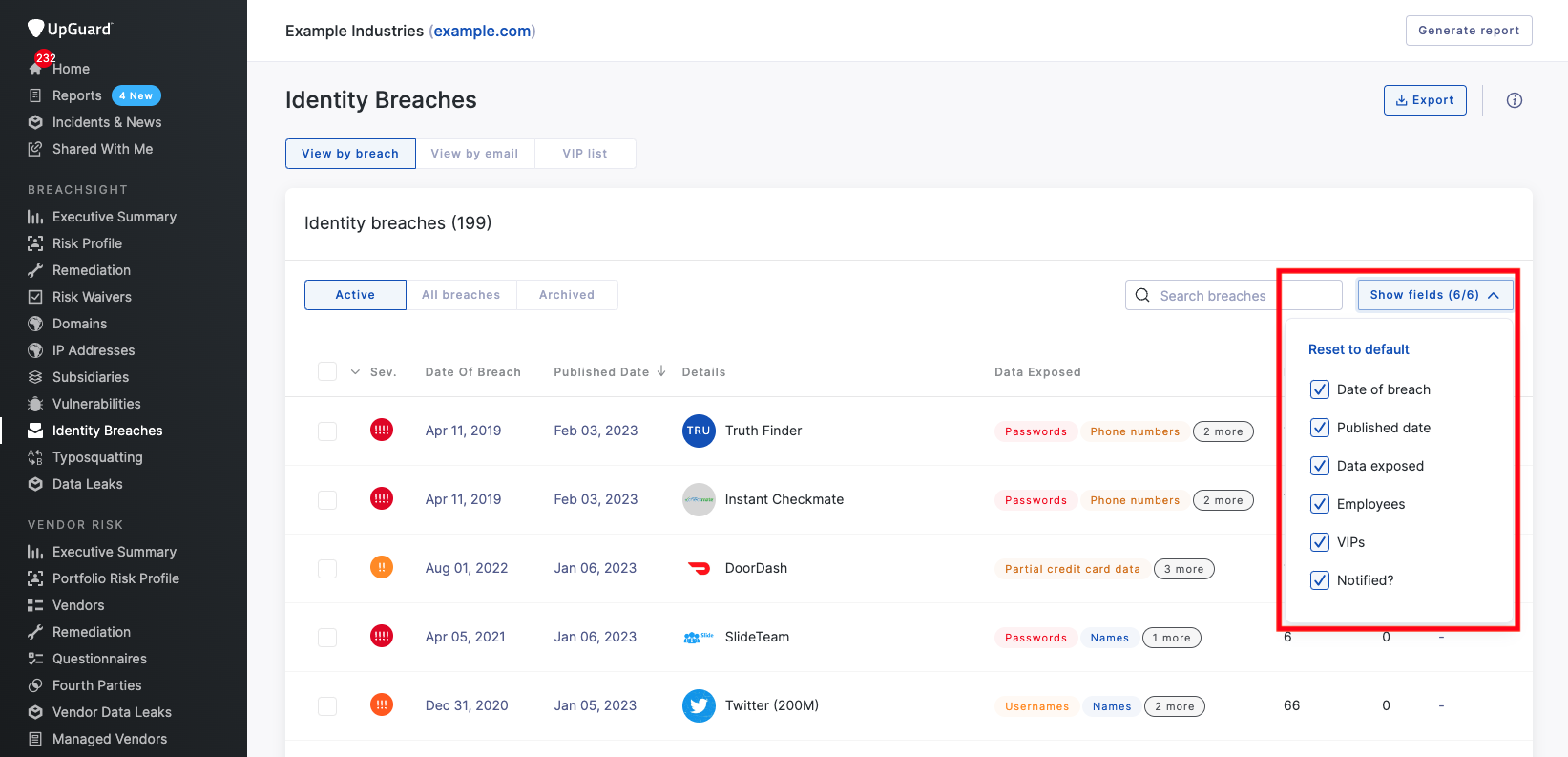 Understanding Breach Severity Classification
Understanding Breach Severity Classification
Every potential identification breach report is assessed by 4 primary danger severity ranges:
Important – Passwords, historic passwords, authentication tokens, and biometric dataHigh – Usernames, safety questions, banking PINs, personal messages, government-issued IDs, emails, bank cards, passport numbers, password hints, cryptocurrency pockets hashes, and social safety numbers.Medium – Dates of delivery, telephone numbers, bodily addresses, partial bank card information, checking account numbers, IMEI numbers, restoration e mail addresses, password strengths, bank card CVVs, deal with e book contacts, and audio recordings.Low – Low-level private information, together with e mail addresses, names, schooling, job titles, revenue, ethnicity, gender, asset possession info, tax data, insurance coverage info, internet searching historical past, system info, and extra.
Every breach is labeled with the very best severity of the info that has been uncovered — a number of cases or information sorts of Low severity and one occasion of Important severity from one breach might be categorized as a Important-level breach.
 Viewing Id Breach Knowledge
Viewing Id Breach Knowledge
Below the Id Breaches module, there are 3 ways to view the info:
View by breachView by emailVIP listView by breach
Corporations may have the choice to archive or ignore a selected breach utilizing the “Archive breaches” button in the event that they really feel that the recognized breach just isn’t a danger.

View by e mail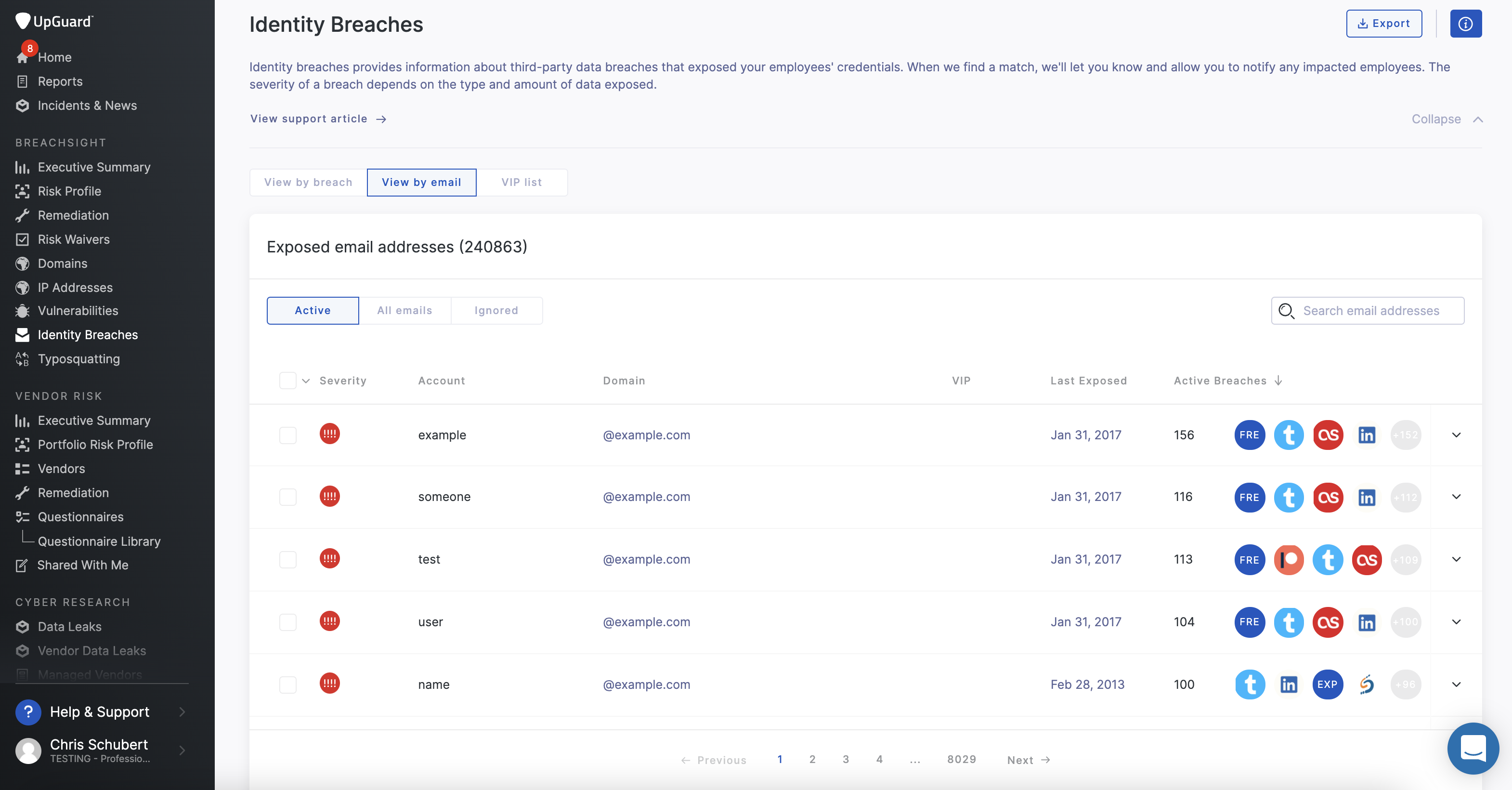
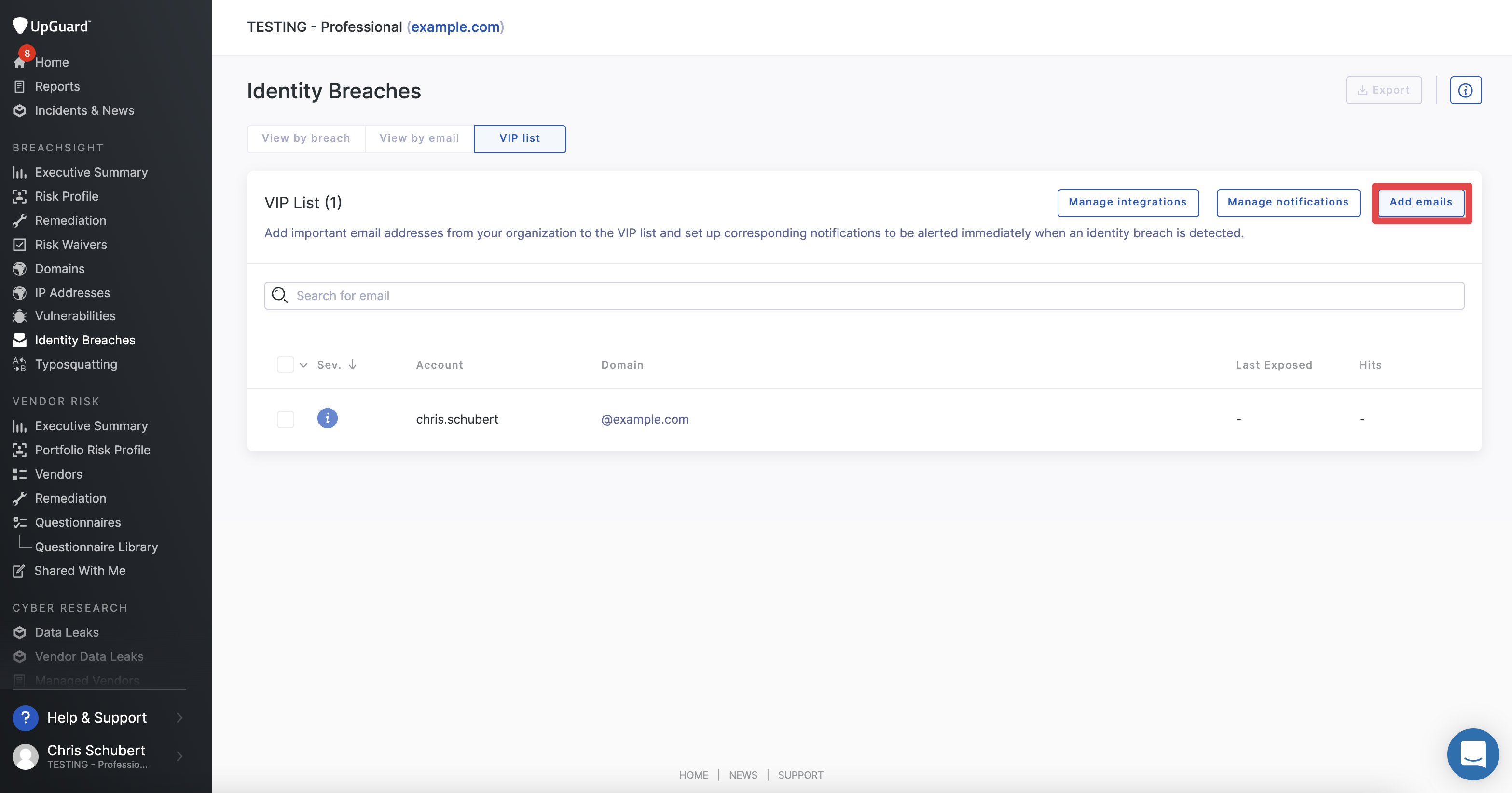
VIP Listing
Notifications will also be configured and set as much as routinely notify any VIPs if they’re concerned in a breach.
Configuring Id Breaches View
The view within the dashboard underneath Id Breaches may be configured to indicate or disguise columns utilizing the “Show Fields” button on the best hand facet. At present, customers can filter the view by six fields:
Date of breachPublished dataData exposedEmployeesVIPsNotified?
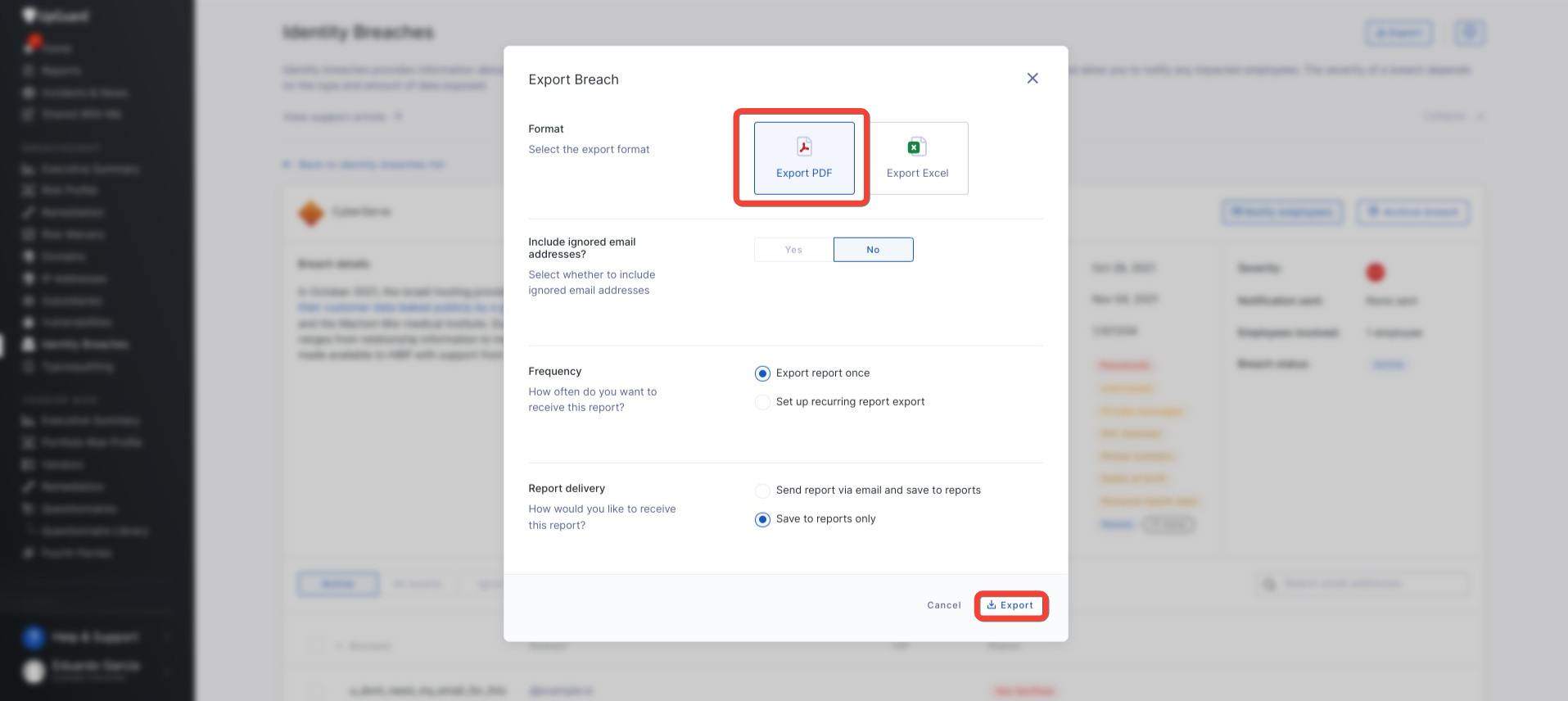
Tips on how to Export an Particular person Id Breach
Customers that need to share particular person Id Breach experiences internally can export them as a PDF doc or Excel sheet.
Prepared to avoid wasting time and streamline your belief administration course of?

