What do all CISOs (chief info safety officers) have in frequent at the moment? They’re going through a barrage of formidable challenges.
Many safety groups are reaching they’re breaking level, and it’s no shock they’re. Coping with a continuing flood of indicators, lagging response instances, and rising cracks for exploitation, is not simple. Assets are stretched skinny, and there’s no room for streamlining operations.
On this article, the newest instalment in our CRPM collection, we discover the tangible outcomes of fixing your most urgent day-to-day challenges. We take a look at the present ache factors plaguing groups worldwide and the way our unified CRPM platform works that can assist you resolve them..
CRPM vs CISO’s hardest challenges
You already know that AI-driven assaults are rising, that human threat is greater than ever, and that regulatory compliance goalposts preserve shifting. CISOs are contending with an overload of noise, an absence of readability, delayed responsiveness, verification gaps, and too many dashboards to make sense of.
You don’t want one other so as to add to your stack, however a single supply of reality. The Cybersecurity CRPM platform supplies exactly that. It’s the resolution you’ll be able to leverage to safeguard your group, eradicate menial administrative duties, and refocus on constructing a “security-first” setting.
Seeing previous the sign fog
With a median of 4,484 threats obtained each day, many CISOs discover it not possible to obviously perceive their dangers. The fluidity of the menace panorama complicates this additional.
Take the CISO of a giant FMCG (fast-moving client items) distributor. She stares at her dashboard and the prolonged autopsy report in entrance of her. Her staff makes use of a dozen disconnected instruments to watch their increasing digital ecosystem, however one thing has been clearly missed as a result of they not too long ago suffered an costly information breach.
A single pink dot flashed, a essential alert a couple of new vulnerability, and it wasn’t caught in time. She should clarify to the board how they misplaced delicate information earlier than they knew they had been beneath assault.
This all-too-familiar situation outcomes from alert fatigue and an absence of context, the place groups drown in info with no clear actionable insights. Whereas a number of instruments could seemingly cowl all of your bases, they don’t account for the areas in between that permit attackers by way of earlier than you’ll be able to deploy a patch.
Fortuitously, our CRPM platform tackles this problem head-on. Powered by compounding intelligence expertise, we may help you progress from a whole bunch of flickering lights to a transparent view of your most important dangers. Cybersecurity helps you to see the unseen and switch a continuing stream of alerts into data-driven choices.
Appearing in seconds, not days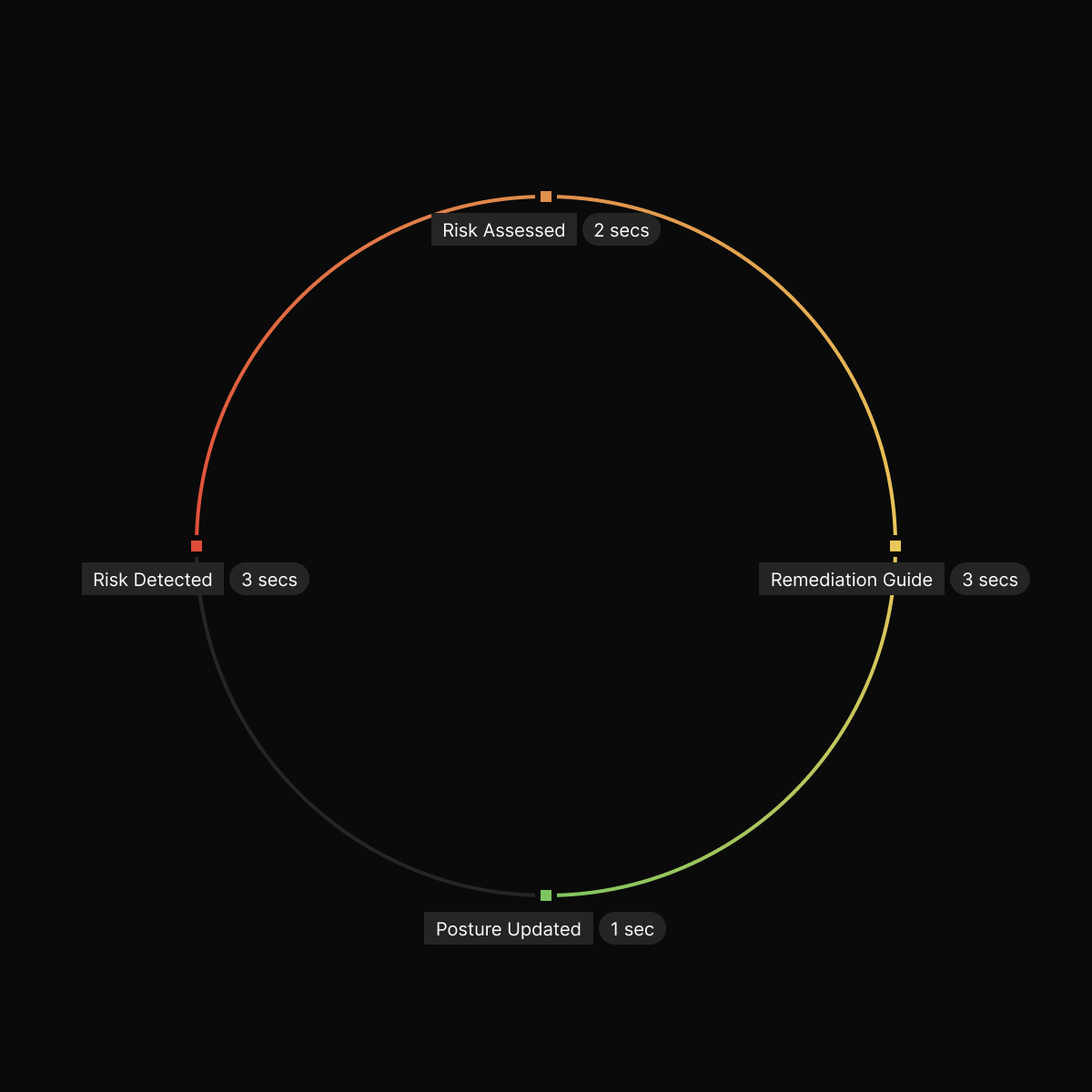
The broader the gaps between threat detection, identification, and remedy, the more durable it’s to safe your group successfully.
Let’s go to one other CISO, who heads up the IS staff at a fast-growing SaaS tech firm. The corporate is projected to hit all its monetary targets this yr, however has held again on hiring extra personnel, leaving its staff stretched skinny.
That is the primary challenge of detection latency. By the point threats are investigated, the assaults have already occurred. Lean groups battle sign fog, guide correlation between information, and attending to what looks like higher-priority points fairly than appearing on enterprise-level threats.
Our CRPM platform’s AI-powered workflows present real-time insights and a zero-grunt work strategy. The staff can robotically determine and prioritize dangers. This lets you act in seconds fairly than days, decreasing the window of alternative for menace actors to assault and minimizing potential monetary and reputational injury.
Sustaining always-on compliance
Level-in-time audits present a false sense of safety. It leaves your safety posture unverified for, on common, 168 days earlier than a breach is detected.
One other CISO is the IS staff lead at a extremely acclaimed healthcare group. He understands, greater than anybody, the delicate nature of the data they work with and the necessity to shield it from leaks.
The staff has fortunately handed their annual HIPAA audit, however he grows extra involved by the day due to how aggressive cybersecurity assaults have gotten. He is aware of their safety posture is ever-changing, and a breach may occur at any level. Their compliance reporting is already outdated when it lands on his desk.
The present “snapshots in time” strategy is in the end stale compliance, however you’ll be able to obtain steady assurance with a unified CRPM platform. At all times-on monitoring flags management lapses as they occur, ensuring you might be audit-ready each day. This shifts your group from a reactive mindset to a proactive state with a verifiable safety posture.
Connecting the dots
The common enterprise is juggling 83 completely different safety instruments. CISOs are grappling with connecting dots in the dead of night as a result of readability and context are at an all-time low on this present menace panorama.
Groups are working from a reactive place, manually sifting by way of information scattered throughout a dozen dashboards, leaving CISOs questioning if they’re even getting their cash’s value out of them. This acquainted actuality solely leads to inefficiencies and chaotic workflows.
Doing extra with much less
The overwhelming quantity of alerts itself is a big challenge. Coupled with countless duties and a fluctuating panorama, it’s no marvel that 98% of safety professionals are reportedly working past their contract hours or that the common CISO is clocking in a further 9 hours per week.
For instance, one other CISO at a big consultancy agency is going through a hiring freeze. His burnt-out staff struggles to maintain up with threats posed by quickly evolving AI-driven assaults.
They spend most of their time producing report after report, chasing down distributors from whom they can not get a straight reply, and manually triaging alerts. The CISO is aware of the staff would profit from a break in guide grunt work, however that will stop operations and be an costly misstep. He doesn’t know tips on how to enhance the state of affairs or relieve the financial strain on the group.
CISOs are keeping off the fixed strain to do extra with much less, but in addition to take action effectively. It may be onerous to determine what your subsequent transfer needs to be, particularly when all it looks like your staff does is put out fires. These reactive, repetitive, low-value safety duties drain your sources.
Our CRPM platform depends on AI workflows to alleviate this strain. Particular duties like ticket creation are sped up, vendor follow-ups are automated, and instantaneous threat assessments offer you readability in seconds.
CRPM: A brand new manner to consider your cyber threat
CISOs at the moment are going through unprecedented change with elevated threat. Every vulnerability threatens all the group. To unravel this, you want an answer to handle threat and ship quantifiable outcomes that show your posture. One which helps you see the unseen, act in seconds, repeatedly assures you, compounds intelligence, and relieves your financial pressure with a zero-grunt work strategy.
Our platform does simply that by specializing in three core rules key to your enterprise worth:
Danger discount: CRPM closes the gaps between detection and motion, enabling you to behave in seconds as an alternative of days.Compliance effectivity: CRPM automates proof gathering for posture verification, which saves your staff numerous hours. Audit defensibility: CRPM presents real-time scoring with historic information for better context, so you’ll be able to present auditors what your posture seemed like one second in the past and exactly what you probably did about it.
Our CRPM platform’s capabilities translate into direct, measurable enterprise outcomes for the common CISO—as a result of it’s a sustainable, strategic resolution to safeguard your group at the moment.
