Vendor danger monitoring is the method of constantly figuring out, assessing, and managing safety dangers related to third-party distributors. This effort is essential to a profitable Vendor Danger Administration program because it ensures a company’s third-party danger exposures stay inside acceptable ranges all through every vendor’s lifecycle.
In a Third-Celebration Danger Administration (TPRM) program, vendor monitoring primarily focuses on two danger classes:
Cybersecurity dangers: Cyber dangers and vulnerabilities within the provide chain enhance your danger of being impacted by a knowledge breach.Regulatory compliance dangers: Misalignments with regulatory requirements as a consequence of a vendor’s info safety practices.
Relying on the chance mitigation goals set by your stakeholders, a vendor danger monitoring answer may additionally monitor the next areas of danger publicity:
Monetary dangers: Potential dangers, equivalent to safety exposures, reputational dangers, or information leaks, that might have a detrimental monetary influence on the enterprise.Enterprise continuity danger: Operational dangers and repair disruptions brought on by third-party distributors, equivalent to the ever present CrowdStrike incident.What’s steady vendor safety monitoring?
Steady vendor safety monitoring is the continuing, real-time evaluation of vendor safety postures to detect and mitigate rising dangers. Not like one-time or periodic vendor danger assessments, steady danger monitoring offers dynamic insights right into a vendor’s cybersecurity efficiency, conserving you recent on any new potential dangers.
Advantages of steady vendor safety monitoring
Steady vendor safety monitoring contains the identical advantages as one-time safety assessments. Nonetheless, ongoing monitoring permits organizations to trace a vendor’s safety posture over time—figuring out downside areas as they seem.
Advantages of steady safety monitoring embody:
Lowering the chance of third-party breaches: Establish and mitigate vulnerabilities earlier than they change into breachesMinimizing regulatory non-compliance fines: Ensures organizations stay compliant with evolving cybersecurity lawsStrengthening incident response: Streamlines detection, which ends up in faster addressing of third-party threats and prevents disruptionsBuilding vendor accountability: Encourages distributors to take care of stronger safety postures and vendor efficiency over timeWhat is the distinction between vendor danger monitoring and vendor danger assessments?
Not like conventional point-in-time assessments, which happen by way of vendor danger assessments, vendor danger monitoring entails ongoing monitoring of rising vendor dangers. This course of can be known as “continuous monitoring” in Vendor Danger Administration (VRM). When used along with point-in-time strategies, steady monitoring processes present real-time consciousness of rising dangers, even between danger evaluation schedules.
Level-in-time danger assessments mixed with steady monitoring produces real-time assault floor consciousness.
To assist safety groups effectively monitor steady monitoring information for a number of vendor relationships, danger monitoring insights are sometimes quantified as a safety score to provide a danger rating representing every vendor’s safety posture. Safety scores are calculated by contemplating a number of danger classes probably impacting vendor efficiency throughout cybersecurity and reputational influence metrics.
Relying on how essential monetary and continuity danger monitoring are to your danger administration goals, it is likely to be most cost-efficient to implement a safety score device for monitoring distributors in opposition to cyber assaults and reputational dangers brought on by poor safety management practices.
 Cybersecurity’s safety score are quantified by contemplating a number of assault vector classes.Why is vendor danger monitoring essential for Vendor Danger Administration?
Cybersecurity’s safety score are quantified by contemplating a number of assault vector classes.Why is vendor danger monitoring essential for Vendor Danger Administration?
VRM applications at the moment are depending on a vendor danger monitoring element for 3 main causes:
1. The seller ecosystem is dynamic
With digital options rising integrations between service suppliers and AI know-how being adopted en masse, a VRM program now requires a vendor monitoring element to maintain up with rising third-party vendor dangers. A extremely vendor-centric ecosystem additionally presents TPRM groups with the issue of conserving monitor of their quickly increasing assault floor. To deal with this, the scope of vendor danger monitoring has been increasing to incorporate the detection of unmaintained applied sciences.
Watch this video for an summary of how danger monitoring could possibly be used to detect know-how merchandise in your assault floor.
Get a free trial of Cybersecurity >
2. Regulatory compliance is extra contingent on efficient third-party danger administration
Third-party distributors proceed to be one of many main components contributing to a company’s information breach dangers, and in consequence, regulatory our bodies are more and more mandating steady oversight of third-party distributors. These stringent vendor danger administration course of requirements are particularly being launched in industries dealing with extremely delicate info and buyer information, equivalent to healthcare, finance, and demanding infrastructure.
The Federal Reserve System, Federal Deposit Insurance coverage Company, and the Division of the Treasury are only a few examples of businesses which have just lately bolstered their third-party danger administration requirements.
Laws usually require organizations to take care of ongoing visibility into every vendor’s danger ranges and have protocols in place for quickly responding to found dangers.
A vendor danger monitoring course of that satisfies most regulatory necessities of enhanced third-party danger administration sometimes entails safety questionnaires mapping to widespread requirements, equivalent to GDPR, HIPAA, NIST CSF, and PCI DSS.
The next video explains how a vendor danger monitoring answer will be leveraged to trace and handle compliance in a extremely regulated sector like finance.
Learn the way Cybersecurity is defending monetary providers >
To streamline the remediation strategy of found regulatory compliance dangers, a perfect vendor danger monitoring device should be able to separating high-risk distributors by way of a vendor tiering mannequin in order that important compliance dangers will be readily prioritized.
 Cybersecurity’s vendor danger matrix provides real-time monitoring of vendor safety postures throughout all criticality tiers.3. Proactive danger administration
Cybersecurity’s vendor danger matrix provides real-time monitoring of vendor safety postures throughout all criticality tiers.3. Proactive danger administration
One of the crucial vital advantages of vendor danger monitoring is its assist of real-time danger detection and, in consequence, speedy remediation responses. In line with IBM, the price of a knowledge breach is instantly proportional to the time taken to answer an incident.
An environment friendly vendor danger monitoring answer may present superior consciousness of third-party dangers earlier than they grow to be safety incidents, which may additionally scale back the numerous monetary, operational, and reputational dangers related to information breach occasions.
What’s concerned within the vendor monitoring course of?
Vendor danger monitoring is concerned throughout all the most important phases of the Vendor Danger Administration lifecycle.
1. Onboarding
Through the onboarding stage of VRM, vendor danger monitoring is leveraged to streamline due diligence workflows by expediting the sourcing of certifications, accomplished questionnaires, and different safety documentation for brand new distributors. As soon as accomplished, the seller monitoring element of due diligence identifies high-risk vendor partnerships requiring extra targeted monitoring all through their relationships.
A vendor monitoring course of may additionally determine situations of danger appetites, with superficial danger scores figuring out potential distributors who needs to be disqualified from onboarding issues.
2. Ongoing danger assessments
As soon as onboarded, the forms of dangers that should be addressed in a third-party danger therapy plan should be actively managed by way of a mixture of point-in-time assessments and steady monitoring, ideally inside a single Vendor Danger Administration answer. This important section of vendor danger monitoring ensures a company’s third-party danger publicity stays inside tolerance ranges.
Fourth-party dangers will be accounted for by way of complete danger monitoring protection. This functionality proved to be a aggressive level of differentiation for VRM platforms throughout the world Crowdstrike incident.
This video demonstrates how extending danger monitoring to the fourth-party panorama advantages VRM efforts throughout world disruptions just like the CrowdStrike occasion.
Get a free trial of Cybersecurity >
3. Automated danger scanning
Automated danger scanning constantly evaluates a vendor’s exterior safety posture by detecting vulnerabilities, misconfigurations, uncovered property, and compliance points. One of these danger scanning automation operates equally to assault floor administration instruments, scanning for cybersecurity dangers like safety gaps that assaults would possibly exploit.
Automated danger scanning contains:
Figuring out vulnerabilities equivalent to open ports, weak encryption, and expired SSL certificatesMonitoring adjustments in vendor environments that might introduce safety risksEnsuring distributors comply with greatest practices by assessing their safety hygiene over time4. Reside intelligence feeds
Reside intelligence feeds. gather dynamic cybersecurity menace information from numerous sources, together with authorities businesses, cybersecurity corporations, and world info safety networks. These feeds present up-to-date info on new vulnerabilities, lively exploits, and evolving threats. Organizations can then use this info to cross-check their vendor ecosystem for brand new vulnerabilities or exploits.
Reside intelligence feeds embody:
Informing safety groups of latest assault strategies concentrating on third-party service providersProviding early notifications about vendor-related threats earlier than they escalate into information breachesAllowing corporations to regulate safety controls primarily based on real-world threats—enabling a proactive strategy to danger mitigation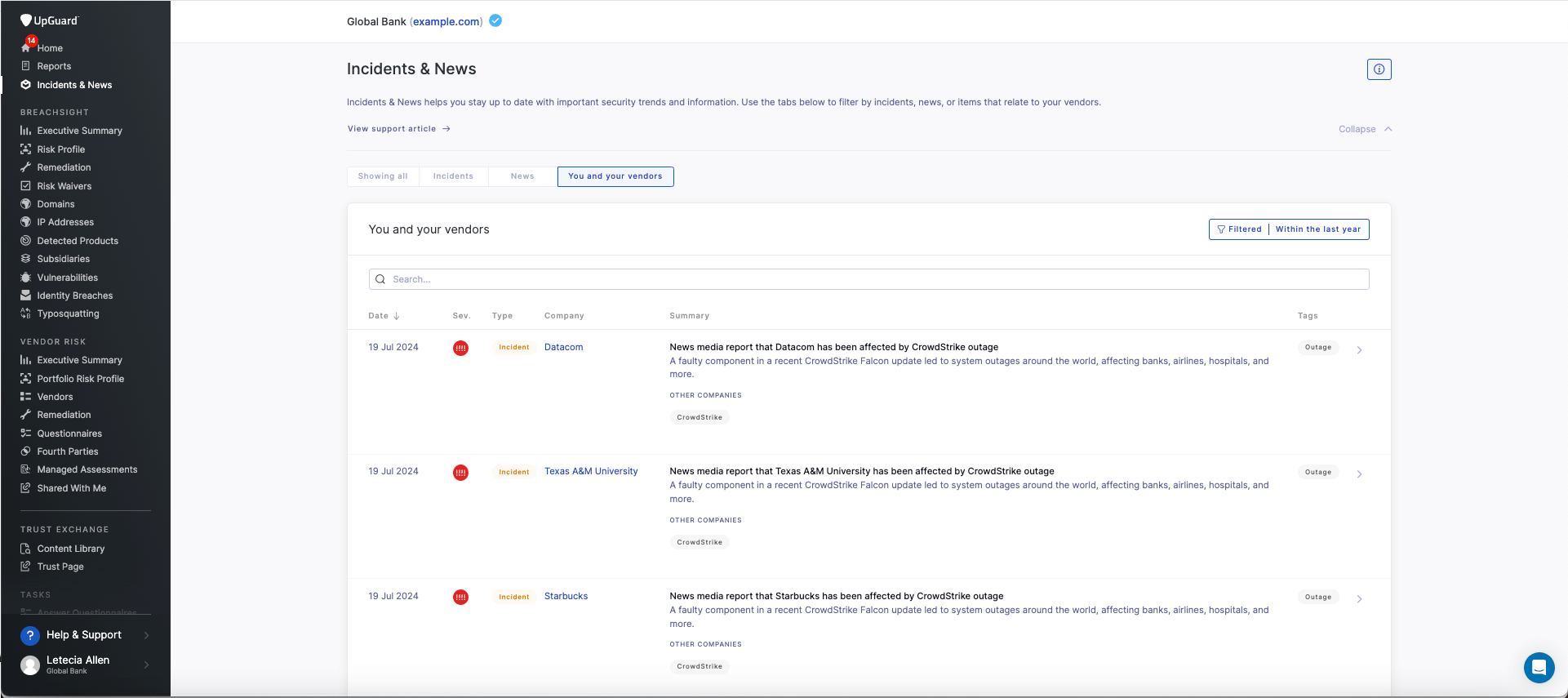 Cybersecurity’s newsfeed confirming distributors impacted by Crowdstrike incident.5. Breach detection and darkish net monitoring
Cybersecurity’s newsfeed confirming distributors impacted by Crowdstrike incident.5. Breach detection and darkish net monitoring
Breach detection and darkish net monitoring determine compromised vendor information, leaked credentials, or uncovered delicate information on illicit on-line marketplaces, hacker boards, and underground information exchanges. Typically, this performance picks up leaked information and new breaches earlier than corporations publicly disclose them—permitting your group to start remediation efforts early.
Breach detection and darkish net monitoring embody:
Detecting if a vendor has been breached earlier than they publicly disclose itIdentifying stolen credentials that could possibly be utilized in credential-stuffing attacksPreventing unauthorized entry by prompting password resets or extra safety controls6. AI-driven danger scoring
AI-driven danger scoring assigns dynamic safety scores to distributors primarily based on menace publicity, safety hygiene, and previous incidents. Machine studying fashions analyze historic and real-time information to evaluate a vendor’s potential danger at any given second. Your group can then use these danger profiles and scores to tell selections about vendor relationships, service ranges, and persevering with particular partnerships.
AI-driven danger scoring contains:
Offering a quantifiable danger metric to match distributors objectivelyAdjusting in real-time as new threats or safety adjustments are detectedPrioritizing high-risk distributors for additional evaluate or remediation efforts7. Regulatory compliance monitoring
Regulatory compliance monitoring displays vendor safety practices in opposition to established cybersecurity frameworks and laws, equivalent to GDPR, CCPA, NIST, ISO 27001, and DORA. Compliance monitoring is very important for organizations in extremely regulated industries, equivalent to monetary providers and healthcare. Monitoring regulatory necessities ensures distributors constantly meet compliance requirements and scale back authorized and monetary dangers.
Regulatory compliance monitoring contains:
Detecting non-compliant distributors earlier than they trigger regulatory penaltiesAutomating compliance audits by constantly assessing vendor adherence to safety controlsReducing the handbook effort required for compliance management8. Stakeholder reporting
With regulatory our bodies rising their emphasis on TPRM practices and world IT disruptions brought on by third-party service changing into widespread, Senior administration now expects to stay knowledgeable of the group’s evolving vendor danger publicity. Vendor danger monitoring processes ought to naturally combine into stakeholder reporting workflows, pulling vendor danger insights that really matter to stakeholders, equivalent to:
The state of the group’s safety posture.An inventory of your most important distributors with the very best potential of impacting the enterprise throughout a safety incident.Every vendor’s safety posture adjustments over time.Danger therapy plans for newly onboarded important vendorsVendor danger monitoring reporting helps stakeholders make knowledgeable strategic selections that align with the group’s evolving third-party danger publicity. Snapshot of a number of the customizable reporting templates out there on the Cybersecurity platform.9. Offboarding
Snapshot of a number of the customizable reporting templates out there on the Cybersecurity platform.9. Offboarding
Danger monitoring throughout offboarding helps compliance groups affirm all retired third-party providers have had their entry to inside delicate sources revoked, a important requirement of information privateness laws such because the GDPR. An assault floor administration device may assist this side of danger monitoring throughout offboarding by detecting areas in your digital footprint the place connections to retired third-party providers are nonetheless lively.
Watch this video for an summary of assault floor administration.
Get a free trial of Cybersecurity >
How usually ought to ongoing monitoring occur in vendor danger administration?
The frequency of ongoing vendor danger administration (VRM) monitoring depends upon a number of components, together with the character of the enterprise relationship, danger scores related to the seller, and regulatory necessities. Right here’s the way you would possibly decide the suitable monitoring intervals:
Vendor danger profile: Excessive-risk distributors—these whose failure or breach may considerably influence your group—needs to be monitored extra incessantly. Take into account steady, real-time monitoring for some facets like cybersecurity danger or month-to-month to quarterly monetary well being and repair supply opinions.Regulatory necessities: Compliance with related laws could dictate how usually you monitor your distributors. As an illustration, distributors dealing with private information could should be reviewed extra incessantly as a consequence of information safety legal guidelines.Enterprise influence: Distributors offering important providers or merchandise within the provide chain, particularly these instantly affecting your core enterprise capabilities or buyer information, require extra frequent monitoring. For instance, IT service suppliers that deal with delicate information would possibly want nearer scrutiny than a provider of workplace provides.Vendor efficiency and historical past: Safety groups ought to monitor distributors with a historical past of safety incidents or inconsistent efficiency extra incessantly till they exhibit secure enchancment. Conversely, personnel would possibly monitor distributors with an extended monitor document of compliance and powerful safety posture much less incessantly, although nonetheless recurrently.Adjustments in vendor standing: Any vital adjustments in a vendor’s enterprise—like danger criticality, mergers, acquisitions, monetary misery, or management adjustments—ought to set off extra frequent monitoring to evaluate how these adjustments have an effect on danger and compliance.4 forms of vendor dangers which are Essential to observe
A vendor danger monitoring program sometimes addresses the next forms of third-party dangers.
Info safety dangers: Third-party vulnerabilities and exposures that might enhance your danger of being impacted ought to a vendor endure a knowledge breach. Steady monitoring of third-party info safety dangers ensures distributors comply with greatest safety practices to safeguard the delicate information you entrust to them.Focus dangers: Cases the place a single vendor is chargeable for the steadiness of your important providers, making a single level of failure. Detecting focus dangers will encourage third-party service diversification and scale back the specter of important disruptions throughout a big world outage.Compliance and regulatory dangers: Cases the place a vendor fails to stick to authorized and regulatory necessities, rising your danger of struggling a expensive violation effective and authorized actions.Reputational dangers: The specter of a vendor’s actions or poor cybersecurity requirements harming your group’s public picture. A vendor danger monitoring answer accounting for third-party reputational dangers offers customers with a constantly updating incident and information feed figuring out all third-party providers probably impacted by a significant safety incident picked by the media. Cybersecurity’s newsfeed confirming distributors impacted by the Crowdstrike incidentTop vendor danger monitoring challenges in 2025
Cybersecurity’s newsfeed confirming distributors impacted by the Crowdstrike incidentTop vendor danger monitoring challenges in 2025
The next vendor danger monitoring challenges sometimes restrict the effectivity of Vendor Danger Administration applications.
1. Guide processes
Reliance on handbook processes produces a number of the most important challenges to vendor danger monitoring. Some instance handbook processes limiting the influence of vendor danger monitoring embody:
Utilizing spreadsheets to handle questionnairesManual information entry of questionnaire responsesManually responding to repetitive questionnairesTracking questionnaires and danger assessments with electronic mail follow-ups
These outdated handbook practices create delayed danger monitoring practices that both utterly overlook important vendor dangers or delay their remediation. With out upgrading handbook processes to extra trendy processes leveraging automation know-how, third-party danger oversight will solely enhance because the enterprise scales.
The next video illustrates how automation know-how may enhance the effectivity and scalability of vendor danger monitoring processes.
Signal as much as Belief Trade by Cybersecurity totally free >
2. Level-in-time assessments
Solely counting on point-in-time assessments restricted vendor danger visibility to danger evaluation schedules, offering a snapshot of your third-party danger publicity at a single time. This myopic strategy to vendor danger monitoring fails to adapt to the dynamic nature of the seller panorama, inflicting third-party dangers arising between evaluation schedules to be ignored.
3. Inadequate information
Some vendor danger administration applications undertake the poor observe of counting on vendor self-reported information obtained by way of accomplished questionnaires. With out an extra layer of verification supplied by steady monitoring processes, organizations may unknowingly be uncovered to important vendor safety dangers that may inevitably be exploited by cybercriminals.
With out impartial verification of a vendor’s safety posture by way of steady monitoring, a company operates underneath a false sense of safety.3. Unscalable VRM program
As a company’s vendor ecosystem expands, managing vendor dangers turns into extra complicated. Scaling danger monitoring efforts to account for lots of and even 1000’s of third-party distributors, every with distinctive cyber danger components and ranging ranges of criticality, may overwhelm even essentially the most well-resourced Third-Celebration Danger Administration groups.
As a result of vendor danger monitoring is a element of Vendor Danger Administration, a scalable danger monitoring technique can solely be deployed on the inspiration of a scalable VRM program, one which leverages automation know-how to streamline the entire workflows in a Vendor Danger Administration lifecycle.
Watch this video for some time-saving suggestions that may enhance the effectivity of your Vendor Danger Administration program.
Finest practices for steady monitoring in vendor danger administration
Steady monitoring is important for managing vendor dangers, guaranteeing that distributors meet contractual obligations, and complying with regulatory requirements. Under are one of the best practices for optimizing vendor danger administration by way of steady monitoring.
Automating processes
Automating as a lot of the continual monitoring course of as doable improves effectivity and minimizes human error. By utilizing a vendor danger monitoring answer and alert providers, organizations can keep a constant overview of their vendor danger profiles.
Make the most of software program to routinely monitor efficiency metrics, compliance information, and danger indicators. Automation instruments may also ship alerts when distributors exceed predefined thresholds, enabling immediate corrective actions, saving time, and guaranteeing constant information assortment and evaluation.
Tailoring monitoring efforts
It’s important to customise your monitoring efforts primarily based on the precise dangers related to every vendor and their corresponding danger stage. Distributors categorized as high-risk, notably these offering important providers, needs to be subjected to extra frequent and thorough monitoring than these posing minimal danger.
Tailoring your strategy on this method permits for the efficient allocation of sources, with a heightened concentrate on areas that might probably considerably influence your online business operations.
Common opinions and updates
It’s important to ascertain a constant schedule for reviewing your monitoring standards, processes, and instruments’ effectiveness. Periodically replace your danger assessments to mirror any adjustments within the vendor’s enterprise setting or your organization’s danger tolerance, together with implementing new instruments and strategies for efficient vendor monitoring.
This observe will be certain that your monitoring efforts stay related to the present business normal and aligned along with your group’s distinctive wants and challenges.
Collaboration and communication
Foster a tradition of robust collaboration and clear communication amongst all events concerned in vendor administration. Vendor administration encompasses the procurement division, IT, compliance groups, and enterprise models instantly interacting with distributors.
Common face-to-face conferences, video conferences, and shared digital platforms can play a pivotal function in guaranteeing everyone seems to be well-informed concerning the monitoring requirements and any points the workforce has recognized. This proactive strategy will facilitate a coordinated and environment friendly response to any challenges.
Cybersecurity helps organizations collaborate and talk with their distributors by way of our vendor collaboration streamlining providers.
Compliance and reporting
Ensure you design your steady monitoring actions to align with the precise laws and business requirements relevant to your group. Set up strong VRM reporting mechanisms that supply detailed insights and thorough documentation to substantiate compliance claims.
These measures are important for efficiently navigating regulatory audits and fortifying your group’s standing throughout contract negotiations or when renewing agreements with distributors.
Reap the benefits of always-on vendor administration with Cybersecurity
Cybersecurity’s Vendor Danger Administration software program is a TPRM platform designed to automate and streamline a company’s third-party danger administration program. Leveraging know-how to simplify the customarily complicated and time-consuming job of evaluating vendor dangers helps organizations effectively assess, monitor, and mitigate cyber dangers related to their distributors and suppliers.
Extra Vendor Danger options embody:
Customizable templates: Cybersecurity offers customizable questionnaire templates that customers can tailor to satisfy particular business requirements, regulatory necessities, and organizational danger profiles.Bulk distribution and monitoring: Vendor Danger allows the distribution of questionnaires to a number of distributors concurrently and tracks the progress of every questionnaire, sending reminders and updates as mandatory.Centralized vendor info: Cybersecurity centralizes all vendor info, together with questionnaire responses, in a single platform, making it simpler for organizations to entry, evaluate, and analyze vendor information.Automated danger scoring: Cybersecurity routinely scores distributors primarily based on their questionnaire responses and different related information, which helps organizations rapidly assess vendor danger ranges and prioritize follow-up actions.Steady monitoring: Vendor Danger displays distributors’ cybersecurity postures and alerts customers to adjustments or rising vulnerabilities. Actual-time visibility into vendor dangers helps organizations reply swiftly to potential threats earlier than they change into incidents.Compliance administration: Cybersecurity Vendor Danger helps distributors attain regulatory compliance with related laws and requirements (like GDPR, HIPAA, and SOC 2), monitoring distributors’ certification statuses and figuring out gaps or points that want addressing.Collaborative options: Vendor Danger facilitates collaboration between inside groups and distributors, enabling seamless communication and effectively resolving recognized points or dangers.Complete reporting: Cybersecurity offers detailed stories and dashboards that supply insights into the group’s general vendor danger panorama, which safety groups can use for inside danger administration functions and to exhibit compliance to stakeholders, auditors, and regulators.
