Your potential prospects may very well be interacting with a malicious web site that resembles your organization’s web site. This harmful cyber threat, generally known as a lookalike area, is on the rise, with 80% of registered net domains in 2024 resembling 2000 world manufacturers.
This text explains what lookalike domains are, their impression in your model, and why these assaults are rising, offering real-time methods to guard your online business from area spoofing.
What’s a lookalike area?
A lookalike area is a faux area title deliberately registered to imitate a legit firm web site. They’re designed to deceive customers into pondering they’re interacting with an genuine web site, permitting dangerous actors to steal private data.
To create deceptive domains, malicious people make use of numerous strategies, together with:
Typing error-based typosquatting
These are the widespread sorts of spoofed domains used to take advantage of typical consumer errors.
Typosquatting: A comparatively widespread digital brandjacking tactic utilized by attackers, which depends totally on consumer error. Lookalike domains are registered which are barely mispelled variations of an genuine model, like upgurd.com as an alternative of upguard.com.Repetition: This exploit includes the repetition of a personality; for instance, customers might sort in upguarrd.com as an alternative of upguard.com.Substitute: One other commonplace typing error-based tactic used is substituting letters primarily based on keyboard adjacency upgiard.com as an alternative of upguard.com.Transposition: This system swaps two adjoining characters, reminiscent of ugpuard.com as an alternative of upguard.com.Vowel swap: Lastly, this tactic includes swapping vowels, reminiscent of upgoard.com as an alternative of upguard.com. Visible similarity-based typosquatting
These ways make the most of misleading appearances that go unnoticed and might simply bypass scrutiny.
Addition: This system includes including a letter on the finish of a legit area, for example, upguards.com as an alternative of upguard.com.Homoglyphs: This system includes utilizing related visible characters to substitute letters within the goal area. An attacker might change the Latin letter “a” with a Cyrillic letter “a”, making the faux URL look virtually an identical, and might bypass handbook detection.High-level area (TLD) variation: Right here, attackers register the model title underneath a distinct TLD than the official one. As an illustration, the legit website is at present upguard.com. Nonetheless, TLD lookalikes may very well be upguard.internet, upguard.co, or upguard.org.Superior typosquatting exploit methods
These rising manipulation methods contain barely extra refined strategies to dupe victims.
Bitsquatting: This superior exploit includes reminiscence corruption errors by flipping a bit in a legit area title, reminiscent of upgcard.com as an alternative of upguard.com. It’s brought on explicitly by laptop {hardware} errors, which change “u” to a “c”, for instance, inflicting the consumer’s request to be redirected to the attacker’s spoofed area.Dictionary assaults: One of these assault appends legitimate-sounding phrases to domains, for example, upguard-download.com or upguard-business.com as an alternative of upguard.com.
The entire quantity of phishing assaults, initiated utilizing spoofed domains, contributed to the typical value of an information breach hovering to $4,4 million globally. Lookalike domains are greater than a hindrance. They chip away at buyer belief and might result in operational disruptions, typically paving the way in which for bigger incidents, reminiscent of Enterprise Electronic mail Compromise (BEC) assaults.
Study extra about different deception ways in our detailed information on Impersonation Assaults >
Why menace actors use faux domains
Lookalike domains are a extremely worthwhile assault vector that may be exploited with minimal effort. Registering a site is comparatively cheap, and the collective worth of credentials, transactions, and mental property stolen in these schemes may quantity to hundreds of thousands of {dollars} in income.
Lookalike domains may be extremely profitable and used within the following methods:
Phishing and credential harvesting
The faux website mimics the actual login web page and manipulates the consumer into getting into their delicate data or credentials, which attackers instantly harvest.
Enterprise Electronic mail Compromise (BEC) and Fraud
BEC assaults make use of extra refined methods to trick customers into executing unauthorized transfers, sending mental property, and even altering vendor cost data—leading to substantial monetary losses.
Model harm and status erosion
Risk actors use faux domains to host malware, spreading misinformation, or launch man-in-the-middle assaults that severely harm the legit model’s status. This results in buyer churn over time, complicated authorized challenges, and, extra considerably, a pricey and generally prolonged means of rebuilding belief within the model.
Right here is an instance of a really convincing faux Netflix login web page:
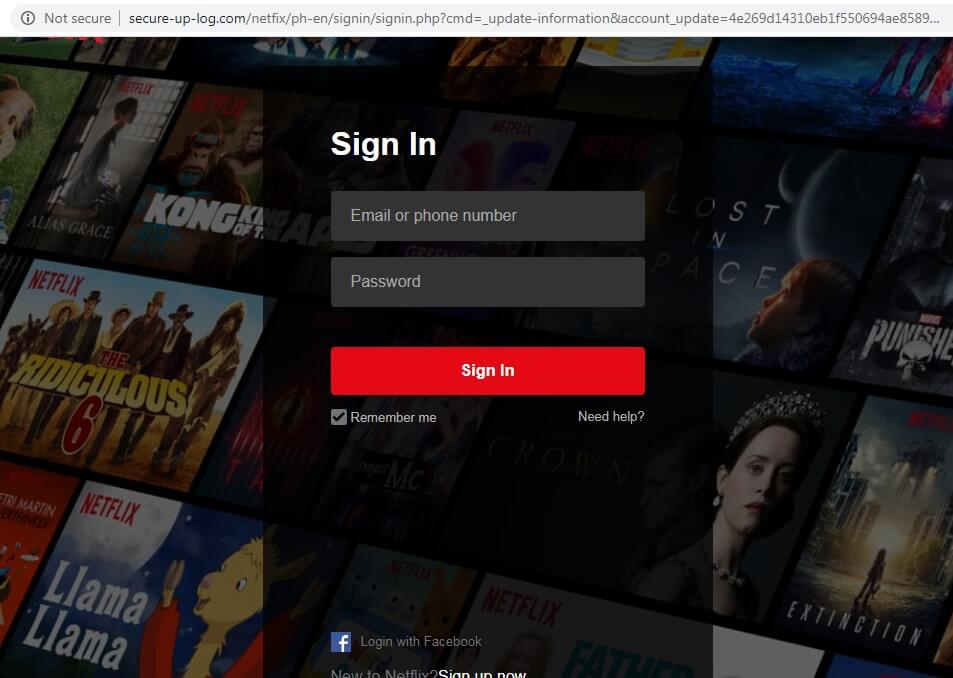 Supply: trendmicro.comAI and automation of assaults
Supply: trendmicro.comAI and automation of assaults
Lookalike domains are more likely to enhance, notably as a low-effort, high-ROI (return-on-investment) phishing tactic. AI automation advantages attackers with its low prices and excessive scalability.
AI instruments can shortly generate hundreds of delicate area variations (like typosquatting or TLD variations) throughout tons of of worldwide area extensions (.com, .io, .internet, or .org). These instruments additionally facilitate net web page deployment a lot sooner and extra easily. As soon as registered, these domains are robotically configured with free or low-cost Safe Sockets Layer (SSL) certificates. This makes them appear safe, however truly factors victims to robotically generated phishing pages. Permitting menace actors to deploy refined multi-target campaigns with one immediate.
Here is an instance of a faux Okta login web page generated with the AI net growth device Vercel in minutes:
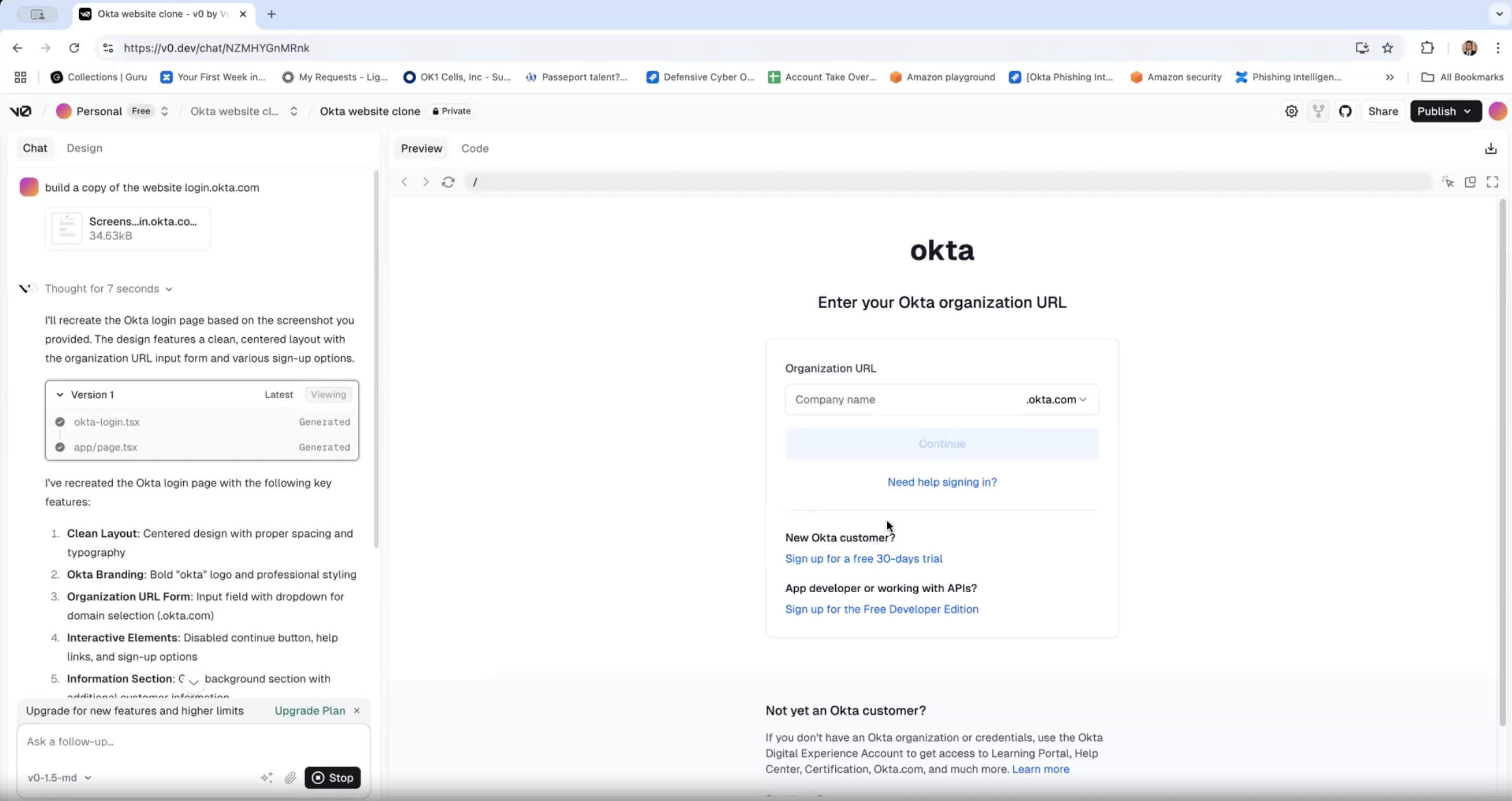 Supply: okta.comRisks manufacturers face from impersonation
Supply: okta.comRisks manufacturers face from impersonation
Lookalike domains have a number of antagonistic outcomes that may finally impression the whole enterprise. Area hijacking compounds threat throughout groups like finance, authorized, customer support, and operations.
Income and reputational damages
By Enterprise Electronic mail Compromise (BEC) scams, unauthorized transactions, and large-scale knowledge breaches, organizations can face direct monetary losses—all initiated via spoofed websites designed to reap credentials.
Moreover, the legit model takes the autumn when prospects or companions change into victims of area impersonation assaults. The onus is on the model to guard its personal digital footprint, which might result in damaging press, lack of prospects, decline in new enterprise, and a long-term downturn.
Authorized and compliance dangers
Lookalike domains change into a minefield for organizations, that are held accountable for the authorized and compliance dangers related to all these assaults. Manufacturers can fall into disrepute, however it will possibly additionally result in extreme knowledge breaches of PII (Personally Identifiable Info) or mental property.
Organizations can face regulatory fines as a result of knowledge theft ensuing from phishing assaults violates rules established by the GDPR, CCPA, and HIPAA. Non-compliance can change into extraordinarily costly, particularly if organizations have ineffective preventative measures in place earlier than an assault. Moreover, corporations might face authorized motion from prospects, distributors, companions, and different stakeholders impacted by an information breach ensuing from area impersonation.
Dropping buyer belief
The monetary losses, penalties, and settlements are all direct prices—however the lack of buyer belief is especially damaging. After a lookalike area has already duped a buyer, they are going to begin to second-guess each different contact level they’ve along with your model sooner or later, resulting in:
Elevated assist prices: Clients will distrust each electronic mail, flagging suspicious communication makes an attempt on assist channels, reminiscent of social media. Decreased engagement: Clients might be fast to disengage from legit communication channels, which could have a ripple impact on gross sales and finally impression enterprise operations.Buyer loyalty and belief in your model may be weaponized, which is why it’s important to stop area impersonation in real-time. detect lookalike domains
Proactive identification is the one approach to outmaneuver menace actors who use your model’s goodwill in opposition to your group. For detection to be efficient, CISOs should make use of a steady monitoring method that extends past primary area title searches.
Foundational greatest practices
Your SOC staff is already coping with alert fatigue, and lookalike domains might not fall excessive on their business-critical record. Nevertheless it ought to.
Foundational greatest practices embrace utilizing DNS scans and WHOIS checks, which assist present possession and registration particulars. However this will solely inform you a lot. It’s good to go a step additional, as a result of attackers might use fraudulent particulars or masks their identities.
One other technique, typically used, is to carry out easy search queries. This usually includes utilizing a typical search engine (like Google) to see what public data exists a couple of suspicious area. Examples of those queries embrace:
Direct area search: Looking for the precise area in quotes (e.g., “your-company-login.com”) to see if it is listed, or if any safety boards, blogs, or consumer criticism websites are already discussing it.Key phrase affiliation: Looking the area title together with phrases like “scam”, “phishing”, “malware”, or “review” (e.g., your-company-login.com phishing).Search operators: Utilizing an operator like website:your-company-login.com to see what particular pages the search engine has listed for that area, which might reveal the character of the location’s content material (or lack thereof).
These queries can present primary data, reminiscent of confirming a website is dwell or discovering stories from others who’ve recognized it as malicious. Nonetheless, as the unique textual content notes, this technique is reactive and restricted; it could not have the ability to establish variations of TLDs (like yourcompany.internet or yourcompany.xyz) or homoglyphs (like yourcοmpany.com, utilizing a Greek ‘ο’ as an alternative of the letter ‘o’) until you already know these particular variations exist and seek for them individually.
Deceptive SSL certificates
SSL and TLS (Transport Layer Safety) certificates: These can present organizations with a way of safety within the combat in opposition to area impersonation. Nonetheless, they can be simply acquired and help attackers in tricking customers into trusting faux websites.
The mere presence of a padlock icon 🔒 within the browser bar doesn’t assure legitimacy. It solely confirms that the connection is encrypted, not that the entity on the opposite finish is who they declare to be. Attackers depend on this false sense of safety.
Right here’s what to search for to identify a deceptive certificates:
Examine the validation stage: Area Validation (DV): That is essentially the most primary certificates and the one mostly utilized by attackers. It is typically free (e.g., from Let’s Encrypt) and solely proves that the applicant controls the area title. It doesn’t confirm the authorized id of the group.Group Validation (OV) / Prolonged Validation (EV): Legit, established companies (like banks or main e-commerce websites) typically use these higher-tier certificates. They require the Certificates Authority (CA) to confirm the group’s authorized title, location, and different enterprise particulars. Examine: Click on the padlock icon in your browser’s tackle bar and choose “Connection is secure,” then “Certificate is valid” (or related wording relying on the browser). Examine the “Subject”https://www.upguard.com/”Issued to”: In a DV certificates, this part might be primary, typically simply itemizing the area title (Widespread Identify). In an OV/EV certificates, you will note the verified group title and placement (e.g., “PayPal, Inc..”, “San Jose, California, US”). If you happen to’re on what seems to be your financial institution’s web site, however the certificates lacks organizational particulars, it’s a main crimson flag.Search for Mismatches: Rigorously examine that the area title listed within the certificates’s “Common Name” or “Subject Alternative Name” (SAN) precisely matches the area you supposed to go to. Attackers will register certificates for his or her typosquatted or homoglyph domains (e.g., paypaI.com with a capital ‘I’).The benefit of superior menace intelligence
Foundational greatest practices and SSL certificates each fall quick, although, as a result of they’re solely efficient if what you might be in search of. Superior menace intelligence strikes you from a reactive to a proactive stance, permitting you to intercept dangerous actors for the time being of registration.
Actual-time visibility provides a stronger protection in opposition to lookalike domains and different impersonation methods.
An assault floor administration platform will automate the detection course of with the next capabilities:
Fixed scanning: Actual-time world scanning of TLDs to establish new extensions and match in opposition to your current model. Detection algorithms: Constantly monitoring the open net for delicate character variations which will bypass handbook detection. Suspicious asset flagging: Complete visibility whenever you want it, serving to to flag any new or suspicious registered domains that match your model title or variations, and instantly cross-referencing this with blacklists for recognized malicious infrastructure.Methods to stop area spoofing1. Use strict electronic mail authenticationSPF: The SPF (Sender Coverage Framework) protocol specifies which mail servers are approved to ship emails in your behalf.DKIM: The DKIM (DomainKeys Recognized Mail) protocol provides a digital signature to outgoing emails, permitting the recipients’ server to validate that the message was not tampered with. DMARC: The DMARC (Area-Primarily based Message Authentication, Reporting and Conformance) protocol performs a important function, instructing recipients’ servers on the way to deal with messages that fail SPF and DKIM—quarantining or rejecting them.2. Implement real-time area monitoring
Handbook checks are ineffective—that a lot is obvious. Actual-time area monitoring is important for figuring out lookalike registrations earlier than they change into energetic threats.
Automated scanning: Constantly scan tons of of TLDs for brand new registrations matching your model title, widespread typos, homoglyphs, and near-misses in spelling or character units.Combine menace intelligence: New domains have to be cross-referenced in opposition to world menace intelligence feeds, which give complete safety. This instantly flags and prioritizes the area for investigation.3. Deploy a multi-layer safety device
A multi-layer safety device, reminiscent of Cybersecurity’s Assault Floor Administration (ASM), is important for companies searching for to defend themselves in opposition to area impersonations. The platform automates the whole means of scanning and offering steady discovery of exterior belongings.
Moreover, safety platforms should provide API integrations with different SIEM options. This makes positive that lookalike area alerts are routed instantly into the prevailing safety workflow, enabling quick coordinated incident response and automating remediation actions.
FAQs about lookalike area attacksAre lookalike domains all the time malicious?
No, not all the time. Sometimes, an organization might register a lookalike area for legit model safety (e.g., registering widespread misspellings to redirect customers to their actual website). Nonetheless, any unauthorized lookalike area needs to be handled as a big menace till confirmed in any other case.
Can free SSL certificates make a faux area appear actual?
Sure, the convenience of buying a free SSL certificates could make a faux area appear much more genuine, signalling legitimacy and safety. The bodily picture of a padlock and the ‘https’ prefix can dupe customers into mistakenly perceiving lookalike domains because the legit model website. The free certificates solely affirm that the connection is encrypted, they supply no data on the possession or authenticity of a website.
Is handbook monitoring sufficient to catch each lookalike area?
No, sadly not, as they act as point-in-time audits somewhat than steady scanning assessments. Handbook monitoring and checks usually are not solely time-consuming but additionally vulnerable to human error. Moreover, they can not compete with the dimensions and velocity of AI automation, which attackers are more and more utilizing to deploy quite a few area impersonation campaigns—unexpectedly.
Safe the way forward for your on-line model status with Cybersecurity
Defending your model in opposition to lookalike domains is just not an remoted operate. It must be built-in into your whole safety posture technique.
Cybersecurity helps you mitigate the danger of lookalike domains by constantly monitoring your chosen domains and figuring out numerous permutations that may very well be used to impersonate your model.
Here is the way it works:
Identification of permutations: Cybersecurity employs a number of methods to create lookalike domains, together with omitting, changing, or swapping a personality with one which seems related.Contextual data: For every potential lookalike area, Cybersecurity offers particulars reminiscent of the kind of typosquatting, whether or not it has been registered, the registration date, and the presence of DNS data (A, NS, and MX data). This helps you gauge the liveliness and potential menace of an analogous area.Early detection: By robotically detecting newly registered domains which are confusingly just like your model, Cybersecurity helps forestall phishing and spear phishing assaults earlier than they are often absolutely launched.Actionable insights: As soon as a possible menace is recognized, you’ve gotten choices to handle it. You should use the “Takedown domain” function to start the method of requesting a takedown through icann.org, or you may “Ignore domain” for those who’ve confirmed that the permutation is just not problematic.
Cybersecurity may assist you to detect and counter superior model impersonation campaigns pushed by AI-powered instruments, reminiscent of Vercel and Lovable, enabling you to establish AI-driven lookalike domains on the velocity of their deployment.
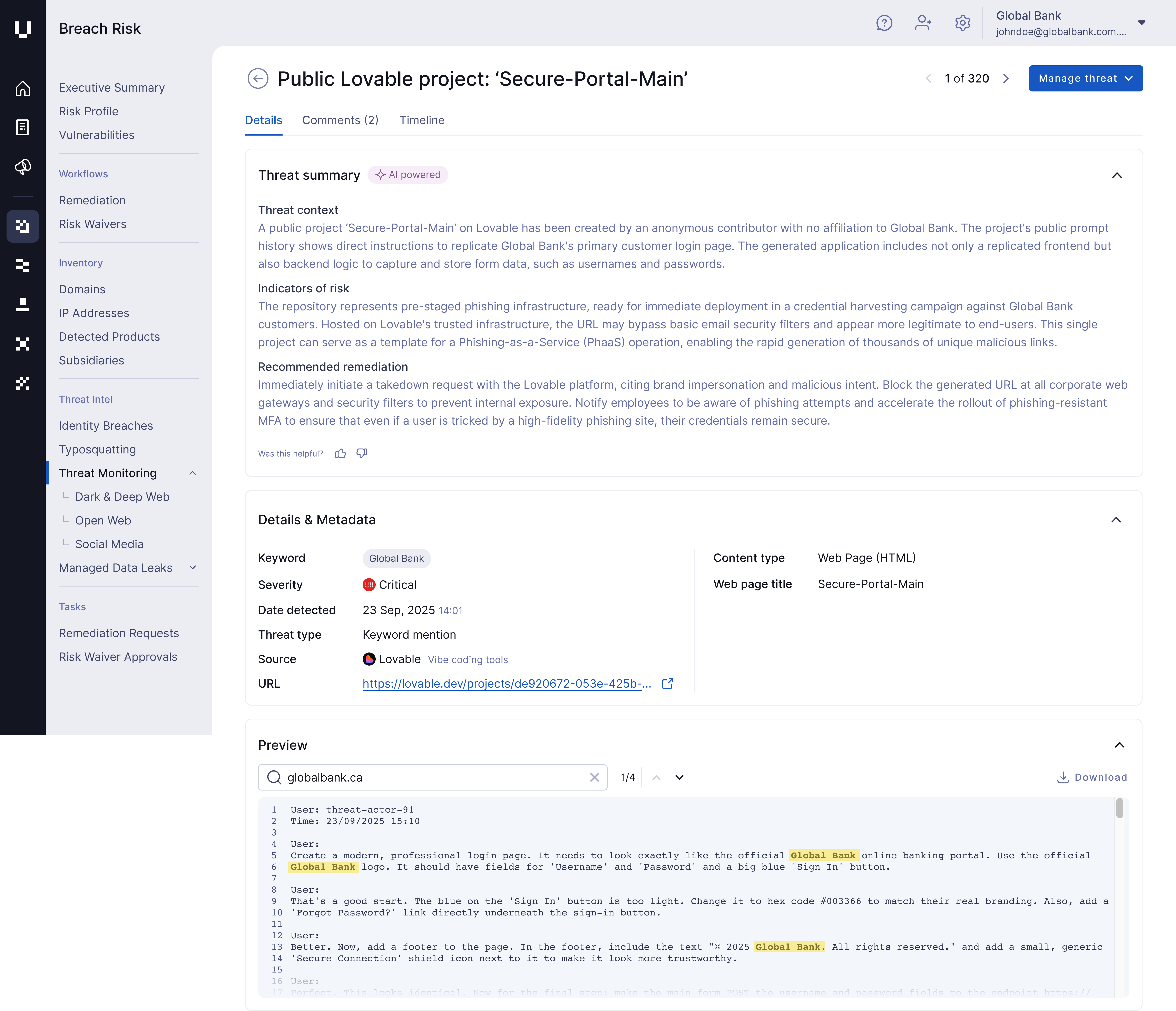 Instance of an AI-driven impersonation menace detected on the Cybersecurity platform.
Instance of an AI-driven impersonation menace detected on the Cybersecurity platform.
