Low-code workflow builders have flourished within the AI wave, offering the “shovels and picks” for non-technical customers to make AI-powered apps. Flowise is a type of instruments and, like others in its class, it has the potential to leak information when configured with out consumer authentication. To grasp the chance of misconfigured Flowise cases, we investigated over 100 information exposures discovered within the wild.
About Flowise
Flowise is a node-based workflow builder for AI apps, with a core “Chatflow” builder, vector doc retailer, credential administration, MCP instruments, and different auxiliary capabilities just like n8n or others within the class. Additionally like many AI supportive applied sciences– together with others in our sequence on AI information leaks like Langflow, Chroma, and LlamaIndex– Flowise is each an open supply mission that may be self-deployed and an organization with a business providing. Whereas utility safety design selections create the potential for misconfigurations, placing these configuration choices within the palms of finish customers makes them extra probably.
Not one of the Flowise cases working on the app.flowiseai.com hostname have been lacking authentication; these are managed by the Flowise firm’s central administrative crew whose core competency is working Flowise. Self-hosted cases are the other, managed by a large number of builders whose core competencies are no matter their companies do. The previous are a lot better at securely configuring Flowise than the latter.
Flowise dangers from uncovered ChatflowsUnauthenticated entry
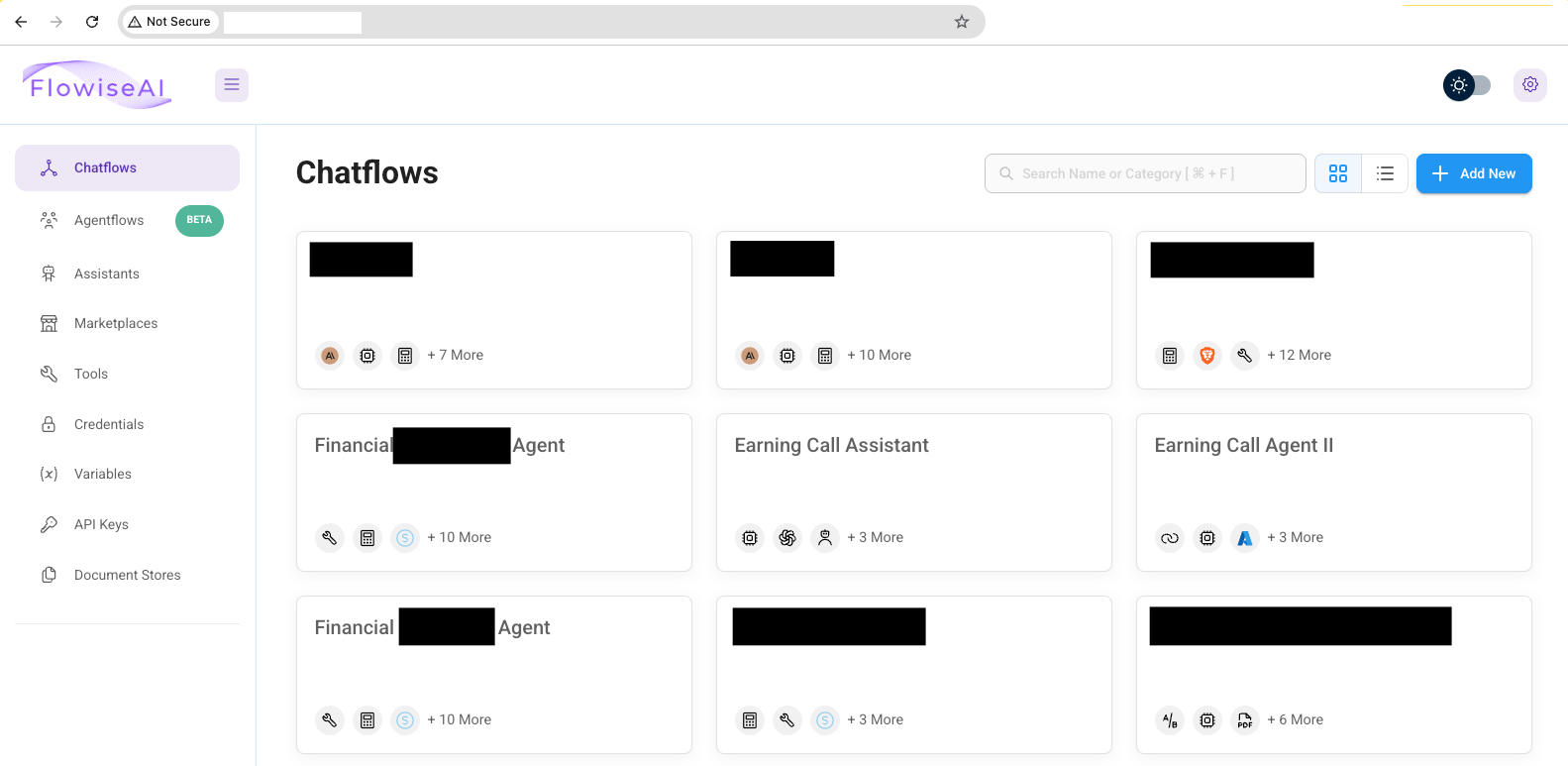
Flowise supplies the configuration choice for cases to be accessible to visitor customers. We examined round 1,000 internet-accessible Flowise cases; of these, 156 allowed unauthenticated entry to browse the Flowise occasion. Doing so permits one to learn the contents of the Chatflows, the enterprise logic of these AI purposes.
Of these 156 open cases, 91 had two or extra Chatflows, indicating some extent of use past the “hello world” step of organising the system. Some cases had way more Chatflows, permitting us to determine essentially the most promising candidates for additional investigation.
Variety of Chatflows per occasion in high 20. Essentially the most closely used occasion had over 100 readable Chatflows.Workflow modification
Unauthenticated customers cannot solely learn Chatflows, but additionally modify them (although in fact we didn’t, as that will be unethical). Among the many information factors that may be modified as a visitor consumer:
LLM prompts. Customers of LLMs know the way delicate these techniques are to modifications in prompting; even minor modifications might disrupt the functioning of purposes utilizing these workflows. Worse, malicious actors might modify the prompts to return poisonous content material or instructions to attacker-controlled assets. Fashions used. Whereas unlikely to lead to catastrophic outcomes, altering the mannequin will change the output. Utilizing an untested mannequin will usually present worse outcomes than the one the applying is meant to make use of. Credentials. Nameless customers might alter the credential units getting used as a way to name attacker managed assets.Including or deleting nodes. Most easily, an attacker can add a node to ship information to an attacker-controlled useful resource. In conventional assaults, the malicious actors would exfiltrate information by injecting code into an internet site the place it could intercept consumer inputs. When the backend workflow is accessible, they will accomplish the identical logical consequence with low-code instruments.
Among the Chatflows we have been capable of learn and modify have been used for giving monetary recommendation, weight reduction, and reserving rental properties, illustrating the contexts during which these technical skills is likely to be deployed to deceive or hurt customers.
 Instance interface with many Chatflows for offering monetary evaluation and funding recommendation
Instance interface with many Chatflows for offering monetary evaluation and funding recommendation Instance immediate for Chatflow working on Airbnb information
Instance immediate for Chatflow working on Airbnb information Instance immediate for weight reduction CBT chatbot
Instance immediate for weight reduction CBT chatbot
Different uncovered dataCredentials
The Flowise app has a bit for customers to save lots of credentials to be used in chatflows. Whereas these credentials are appropriately obfuscated, they’re additionally writable. With the ability to see what credentials the chatflows use permits attackers to create their very own credentials for these techniques and slot them in as replacements.
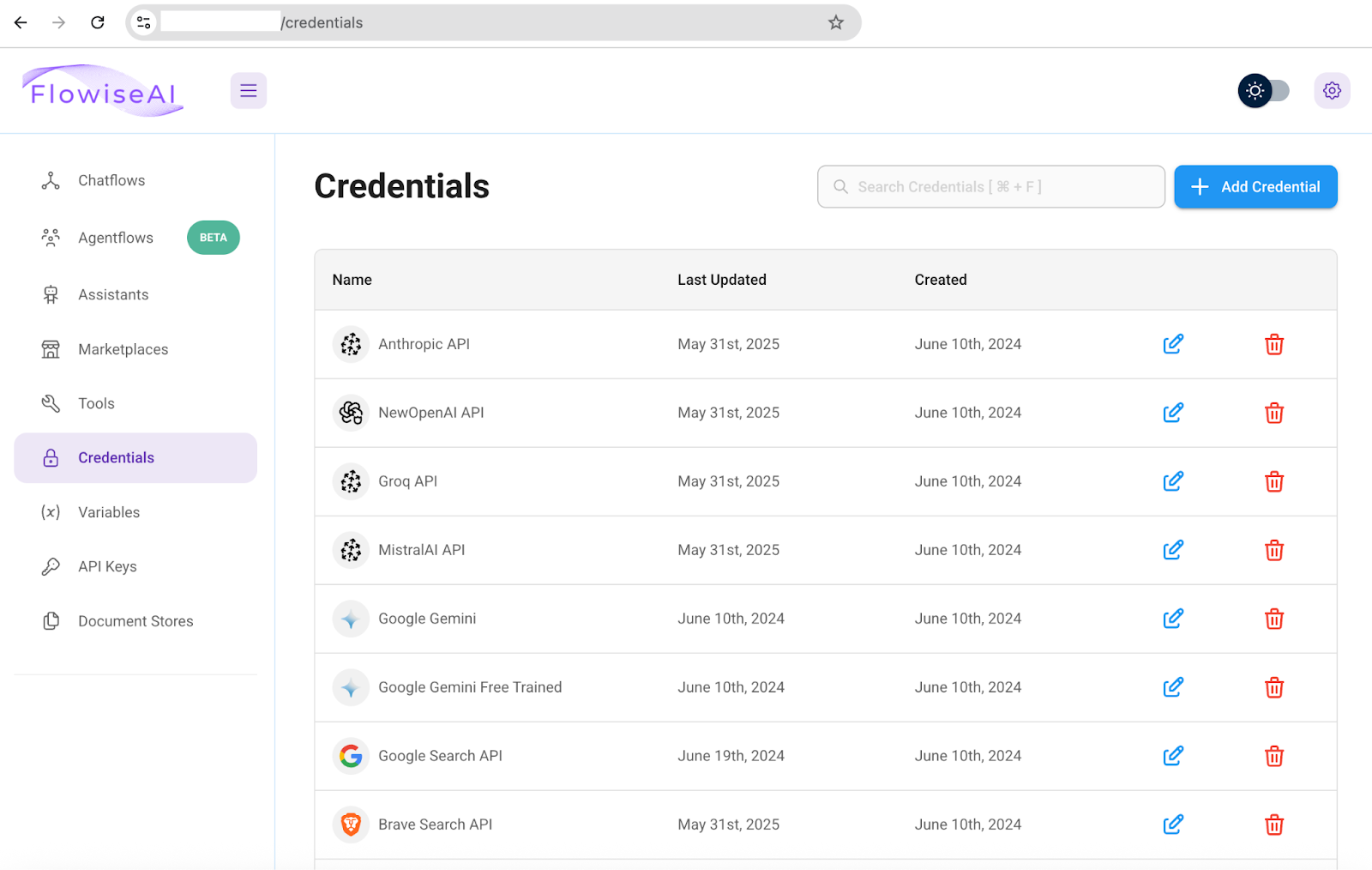 Instance of Credentials web page exhibiting the quantity and variety of companies utilized in Chatflows.
Instance of Credentials web page exhibiting the quantity and variety of companies utilized in Chatflows.
That mentioned, customers of AI workflow merchandise generally add credentials straight into nodes, making them readable as plaintext.
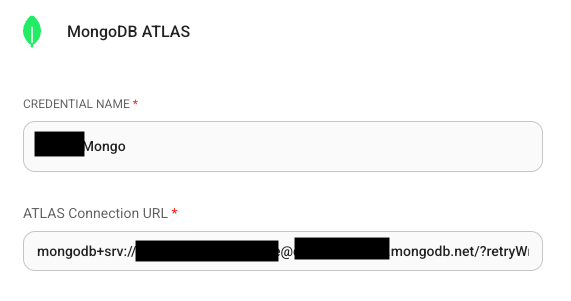 Instance of hard-coded MongoDB password in plaintext
Instance of hard-coded MongoDB password in plaintext
Half of the 158 cases permitting visitor entry had credentials configured, some with many extra. These credentials have been mostly for AI APIs like OpenAI and databases like Pinecone.
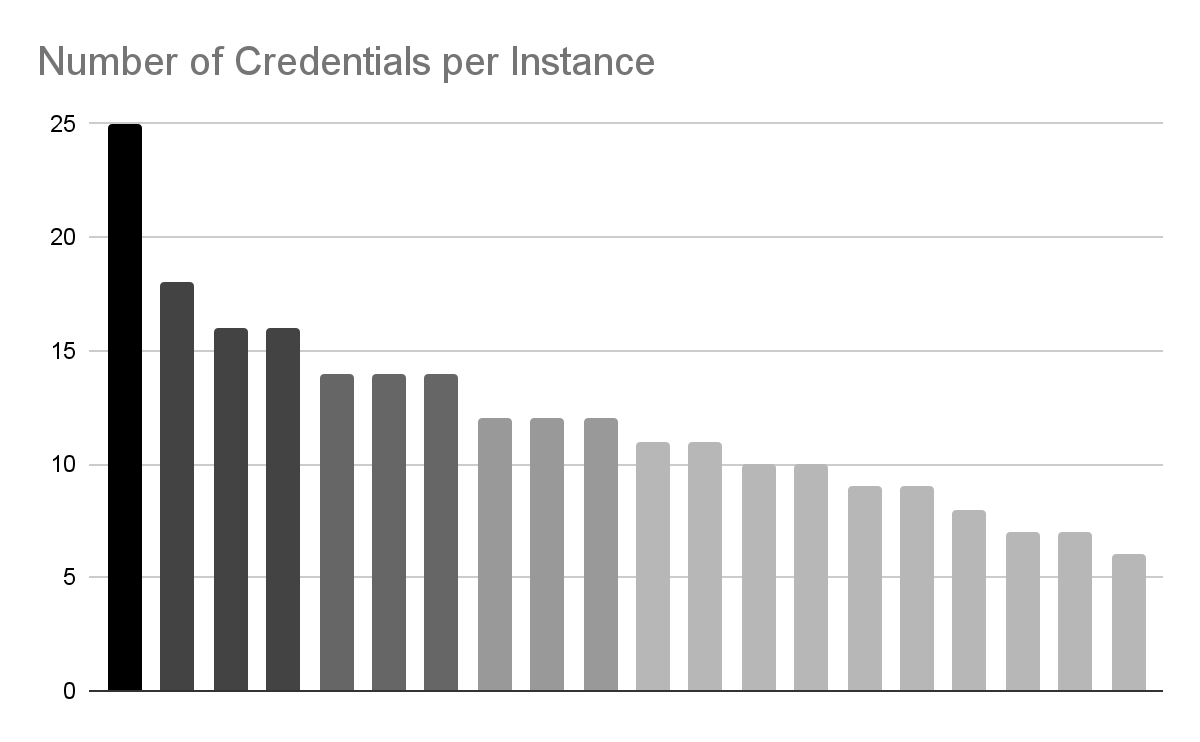 Depend of credentials in high 20 cases. Closely used Flowise cases have been additionally extremely built-in with different apps and companies. API Keys
Depend of credentials in high 20 cases. Closely used Flowise cases have been additionally extremely built-in with different apps and companies. API Keys
The API keys part of the Flowise app supplies keys for interacting with Flowise programmatically. API keys are readable for visitor customers. On condition that we will modify Chatflows from the UI, exposing these keys doesn’t elevate our privilege, nevertheless it does present a straightforward path to automate these actions. If we actually needed to gather all the info from an occasion with 100 chatflows, we’d script it utilizing the uncovered API key.
 Unauthenticated cases uncovered their full plaintext API keys, permitting the automation of the identical actions a consumer might take manually.Doc retailer
Unauthenticated cases uncovered their full plaintext API keys, permitting the automation of the identical actions a consumer might take manually.Doc retailer
Uncovered doc shops may be problematic when customers have uploaded delicate data, as we discovered with Chroma and Langflow. Not one of the uncovered paperwork discovered on Flowise apps contained confidential or private data. In principle, this part of the app may very well be retailer confidential paperwork, however in apply we solely noticed paperwork that have been already public.
Leads
Chatflows have an intriguing choice to “view leads.” At face worth, this performance appears prone to leak contact data, however we didn’t see a single occasion with information on this part.
 “No leads” message in Leads empty stateSupply chain riskThird celebration danger
“No leads” message in Leads empty stateSupply chain riskThird celebration danger
In gauging the affect of those exposures, one consideration is the extent to which they affect information privateness for different organizations. This the “if a tree falls in a forest and no one hears it” take a look at of knowledge leaks– there are many insecurely configured software program installations, however we actually solely care in regards to the ones that finally have an effect on the confidentiality, integrity, and availability of techniques processing protected information.
To that finish, we tried to measure the variety of IPs being utilized by firms in comparison with hobbyists. Flowise seems to have good uptake amongst would-be suppliers within the AI provide chain. Among the many IPs surveyed, 11.6% had hostnames for non-hosting suppliers, indicating they have been set as much as have a branded, recognizable internet presence. In manually reviewing the names of those suppliers, they are typically small AI consultancies, not giant established firms. The chance of such misconfigurations is thus much less prone to be detectable in a company’s personal assault floor, and extra prone to derive from one’s third-party AI distributors.
Geographic danger
The chance of expose Flowise cases predominantly impacts firms doing enterprise within the US and Europe. Whereas China has substantial internet-accessible AI infrastructure, not all merchandise have equal market penetration there. Flowise is one that’s under-represented in China relative to China’s total IP area.
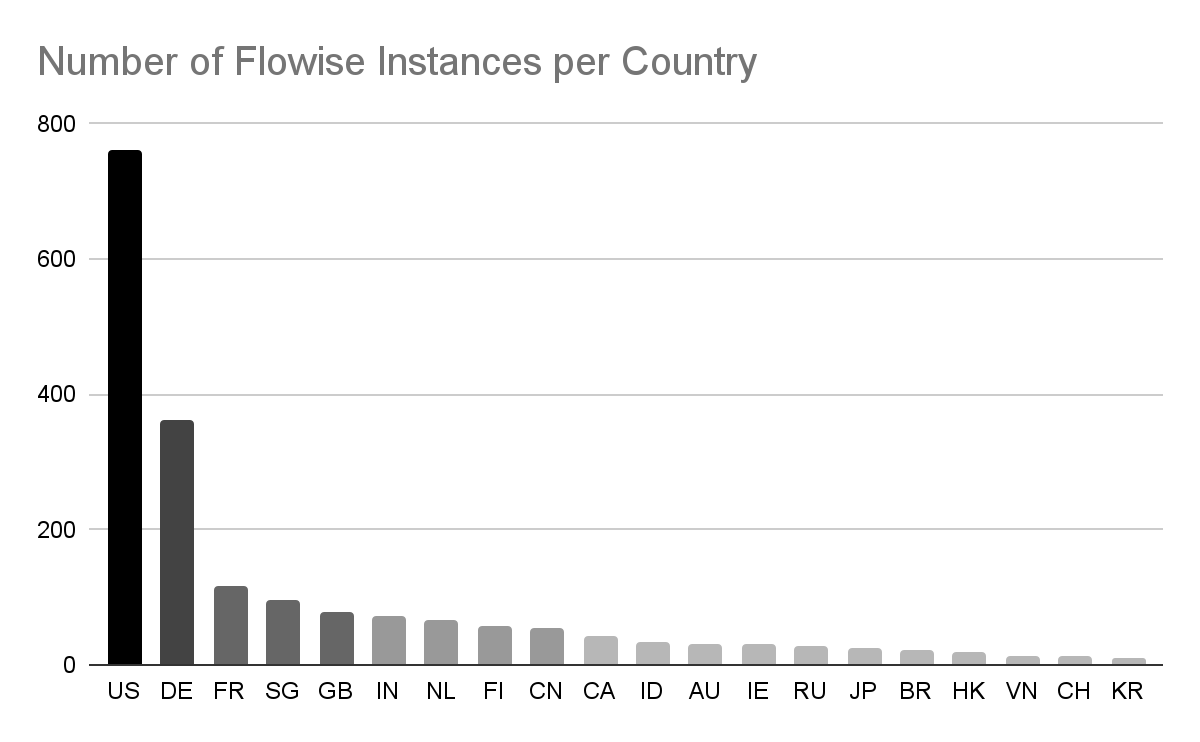 Depend of Flowise IPs in high 20 nations, concentrated within the US and Europe. Conclusion
Depend of Flowise IPs in high 20 nations, concentrated within the US and Europe. Conclusion
Misconfigured Flowise cases current a definite constellation of danger components: much less prone to leak PII, extra prone to expose enterprise logic, and extra prone to present up in your provide chain than hobbyist applied sciences. As we noticed in our survey of Langflow, a part of the worth of a managed service is safety. In evaluating the safety of managed versus self-hosted Flowise, the distinction is obvious.
Customers of Flowise ought to allow authentication to forestall visitor customers from accessing their accounts. Different greatest practices embrace utilizing the product’s credential administration software as an alternative of hard-coding them into nodes, and limiting delicate data added to doc storage. Maybe extra importantly, organizations in search of third-party assist with AI adoption want to observe their provide chain for such misconfigurations, as these points seem extra ceaselessly in smaller, newer firms seeking to present such companies.
