The road between the digital and bodily worlds blurs fully when a cyber assault leads to widespread, tangible disruption. For 1000’s of vacationers, this turned a harsh actuality when main European airports had been compelled to delay flights on account of a ransomware assault focusing on a vendor within the provide chain.
To forestall a repeat catastrophic occasion, we should break down how the seller’s vulnerability was exploited and deepen our understanding of the often-overlooked dangers lurking inside complicated know-how provide chains.
What we all know
On Saturday, September 20, 2025, a cyber assault prompted important disruptions at a number of main European airports. The European Union Company for Cybersecurity (ENISA) later confirmed {that a} ransomware assault prompted the outage, which focused the ARINC vMUSE system, a passenger processing platform by Rockwell-Collins.
ARINC error message: Supply: Cyberplace.social
With this technique unavailable, airports had been compelled to change to guide procedures. This workaround prompted main delays for passengers and led to 217 flight cancellations throughout the important thing affected hubs as workers labored to get operations shifting once more and restore the system’s performance.
A sequence of vulnerabilities
Whereas the total particulars of the intrusion are nonetheless beneath investigation, the technical reason behind the breach factors to a traditional and preventable safety failure: the exploitation of outdated, susceptible, and internet-facing methods. The vMUSE platform connects airports through a proprietary Collins community referred to as ARINC AviNet, which capabilities as a devoted VPN. The simultaneous failure throughout a number of airports strongly means that this central community was the purpose of compromise.
Here’s a listing of the highest ten airports utilizing vMUSE:
Airport
Location
London Heathrow
United Kingdom
Glasgow Airport
United Kingdom
Berlin Schönefeld
Germany
Dublin Airport
Eire
Cork Airport
Eire
Cologne Bonn Airport
Germany
Mazatlán Worldwide Airport
Mexico
Zihuatanejo Worldwide Airport
Mexico
Monterrey Worldwide Airport
Mexico
Velana Worldwide Airport
Maldives
Safety researchers analyzing the public-facing infrastructure of the ARINC community shortly recognized a number of crimson flags, portray an image of a digital atmosphere ripe for compromise. Public scans revealed that the corporate’s community was working a number of out of date software program, together with:
Microsoft’s IIS 8.5 net server, which reached its official end-of-life in 2023.A model of the Glassfish software server relationship again to 2014.An Oracle Communications Messaging Server that had not been up to date since 2015.These legacy methods include well-documented vulnerabilities which have lengthy since been addressed in newer variations.
A big cybersecurity oversight seems to be the usage of outdated community {hardware}. Half of the corporate’s Cisco ASA VPN home equipment — gadgets that act because the gatekeepers for the community — had been working previous their producer’s end-of-life date, which means they now not obtained safety updates.
A variety of recognized vulnerabilities exists for these gadgets and their software program. Coupled with the truth that they have to be internet-facing to perform, the usage of Cisco ASAs creates a high-risk atmosphere ripe for exploitation.
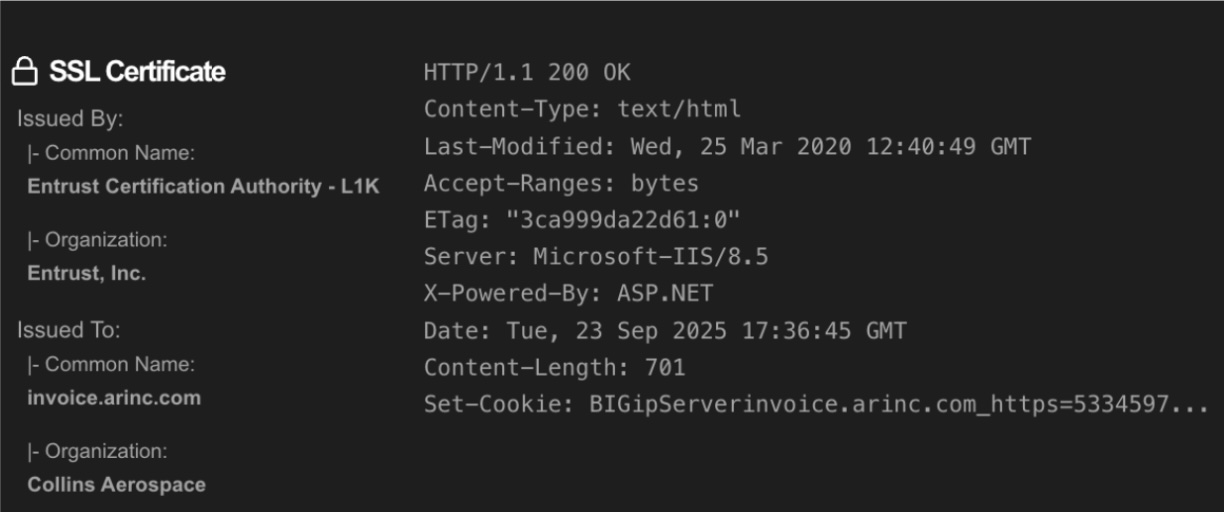 Screenshot of IIS 8.5 server registered to Collins Aerospace on the arinc.com area.
Screenshot of IIS 8.5 server registered to Collins Aerospace on the arinc.com area.
Cyberattacks with such large-scale impacts often require in depth preparation, and this occasion might have been set in movement as early as 2023. Although not confirmed by Collins Aerospace, the ransomware group BianLian claimed to have breached Collins Aerospace in 2023, stealing round 20 gigabytes of information.
If true, this occasion may have armed the attackers with the information leaks they wanted to efficiently execute this larger-scale assault.
The core lesson: A failure of supply-chain safety
Finally, the chaos that unfolded throughout Europe’s airports was not simply the results of a single firm’s safety lapse however a catastrophic failure of supply-chain safety. The incident is a textbook instance of the ripple results of an interconnected digital ecosystem, the place a vulnerability in a single vendor can set off a cascade of disruptions for numerous dependent organizations.
The reliance of a number of worldwide airports and airways on a single, compromised system creates a single level of failure that attackers may exploit with devastating impact.
Including a essential layer to this failure, the European Union Company for Cybersecurity (ENISA) revealed that the attackers’ preliminary entry level was not Collins Aerospace, however certainly one of its personal third-party suppliers.
This oversight highlights a basic weak spot in fashionable enterprise safety: most organizations are blind to the safety dangers of their vendor community.
This element transforms the occasion from a direct vendor compromise right into a multi-layered supply-chain assault, highlighting how deep and opaque these digital dependencies will be. It underscores a basic weak spot in fashionable enterprise safety: organizations are sometimes blind to the dangers inherited from their distributors’ distributors.
To forestall future incidents of this scale, organizations should undertake a extra rigorous and proactive strategy to cyber threat posture administration.
Key suggestions embrace:
Demand full transparency from distributors: Essentially the most essential lesson from this occasion is that organizations should have deep visibility into their distributors’ know-how stacks and inside safety insurance policies. It’s now not adequate to just accept a vendor’s assurances of safety. Companies should demand solutions to particular, granular questions, like: What software program and {hardware} are you utilizing? What are your patching schedules and replace insurance policies? How do you handle end-of-life tools? TProper provide chain safety assumes a vendor’s methods are seemingly assault vectors, and that begins with full consciousness of their digital footprint.Implement strong legacy system administration: Crucial methods that depend on older elements or can’t be simply up to date current a major threat. These methods have to be correctly inventoried, constantly monitored, and guarded with robust compensating controls to scale back their assault floor and isolate them from potential threats.Elevate cybersecurity to a core enterprise Operate: The extent of funding and govt oversight in cybersecurity should straight correspond to the criticality of the methods being protected. Safety can’t be handled as a easy back-office IT perform; it’s a basic enterprise threat. Rectifying this organizational mindset is the primary and most essential step in constructing true resilience.
The aviation business, and certainly all sectors counting on complicated know-how companions, should now transfer swiftly to implement these ideas to construct a extra defensible Third-Get together Danger Administration basis.
