The digital panorama is increasing at an unprecedented charge, pushed by the mass migration to the cloud, the proliferation of IoT gadgets, and the fast progress of AI. Whereas this progress presents limitless alternatives, it additionally creates a frightening new actuality for cybersecurity groups.
As an organization’s digital footprint and assault floor develop, it turns into more and more weak to the rising variety of threats, significantly these originating from the open, deep, and darkish net. Menace actors in these areas have gotten more and more energetic, establishing bigger operations and creating complete prison provide chains.
The issue is that even when safety groups use devoted instruments to observe the darkish net, they’re typically overwhelmed by a flood of uncooked knowledge and alerts. This requires vital guide effort to research and remediate, forcing groups right into a reactive safety technique relatively than taking proactive steps to guard their posture.
So, how can a cybersecurity group, already inundated with day by day alerts, proactively handle the ever-growing variety of threats from illicit on-line areas? The reply lies in a single essential facet of menace detection: context.
Why Context Issues Now, Greater than Ever
As the common enterprise’s assault floor continues to develop, fashionable safety operations heart (SOC) groups are more and more centered on detecting threats from the open, deep, and darkish net. These areas are a well known blind spot for standard inside safety instruments, comparable to firewalls and endpoint detection and response (EDR) programs, which solely monitor their rapid perimeter.
Consider it this manner: securing your property with bodyguards who verify the doorways and home windows is a strong protection. However who’s checking the native pub down the road the place somebody may be discussing their plans to interrupt in subsequent week? Within the fashionable safety panorama, that “pub” is the place breaches typically start—with attackers promoting stolen credentials, planning assaults on illicit boards, or exposing delicate knowledge in public code repositories.
To complement these blind spots, menace analysts make the most of particular person instruments to scan the web for underground boards, marketplaces, and prison teams, thereby understanding their techniques, strategies, and procedures (TTPs). Whereas these scans are helpful, they lack a vital element: context.
These exterior sources generate a considerable amount of noise within the type of alerts. With out a specialised resolution that gives real-time readability, the method turns into sluggish and inefficient. Every potential menace should be triaged and investigated individually, turning important intelligence into an unmanageable sea of noise.
This lack of context is the driving issue behind two essential points confronted by SOC groups when monitoring the open, deep, and darkish net: a reactive safety technique and alert fatigue.
A reactive safety technique
A reactive safety technique means a safety group is continually enjoying catch-up, responding to threats solely after they have been recognized. It is a direct results of a scarcity of context. With out a clear understanding of an alert’s severity, analysts are compelled to react to each sign, losing time on low-priority points whereas actual threats go unnoticed.
As an alternative of proactively attempting to find dangers and strengthening defenses, the group will get caught in a cycle of triage and investigation, by no means gaining a bonus.
A very proactive safety technique makes use of context to prioritize threats, spot new traits, and predict potential assaults earlier than they occur. For instance, if an organization’s credentials are bought on the darkish net, a proactive group would use context to know the scope of the breach and take steps to stop future assaults.
With out this contextualized method, groups are left combating one fireplace at a time, creating an insecure and unsustainable operational mannequin.
Alert fatigue
Alert fatigue is a longstanding challenge throughout the cybersecurity business, and it’s particularly prevalent when groups are required to manually triage, examine, and remediate each alert from their day by day scans with out context. This time-consuming burden is a critical menace that may severely weaken an organization’s safety posture and probably result in main safety gaps.
This fatigue triggers a cascade of dangers, together with missed essential alerts, widespread group burnout, and a excessive quantity of false positives. Let’s check out some examples of the results that come up when alert fatigue is prevalent inside your cybersecurity group.
Elevated danger of information breaches: Safety analysts face an awesome variety of alerts, which makes it simple to overlook actual threats. As an illustration, the M-Developments 2025 report revealed that cybercriminals are utilizing Infostealer malware to steal delicate knowledge and promote it on on-line boards. These real threats may be simply misplaced within the fixed stream of notifications that analysts should cope with, and thus, the probabilities of a profitable breach enhance.Delayed response to essential threats: Investigating false positives, comparable to your organization title merely being talked about on a darkish net discussion board, is a major drain on a safety group’s time and sources. When analysts are overwhelmed with irrelevant alerts, their consideration is diverted from actual threats, thereby delaying the detection and prevention of an assault.Excessive worker turnover and burnout: The stress of sifting by 1000’s of alerts day by day can result in emotional and bodily exhaustion, and this stress issue is amplified when alerts are coming from various sources. A examine commissioned by Kaspersky discovered that 83% of cybersecurity practitioners expertise alert fatigue, which may result in excessive turnover charges.Wasted sources: The time safety professionals spend investigating irrelevant alerts is time not spent on extra strategic initiatives, comparable to proactive menace searching or enhancing safety structure. This results in an inefficient use of beneficial human sources and may end up in increased operational prices.
It is clear then that the difficulty of context issues extra now than ever earlier than. It is the foundation trigger behind essential safety gaps when monitoring the deep, open, and darkish net, considerably rising alert fatigue and inaccurate responses. The grim actuality is that when your group is caught on this cycle, no matter how lean your SOC group is, your small business’s general safety posture is in danger.
Fortunately, nonetheless, this daunting problem may be mitigated. That is our reply to the rising variety of contextless alerts from the open, deep, and darkish net, in addition to the essential considerations of reactive safety methods and alert fatigue: Breach Threat Menace Monitoring.
Introducing Menace Monitoring: Slicing Via the Noise To Allow Proactive Threat Administration
Cybersecurity has formally expanded our Breach Threat resolution to incorporate a brand new function known as Menace Monitoring. Our imaginative and prescient for this product was easy: to offer cybersecurity groups with a approach to minimize by the noise when monitoring the broader web and switch indicators into actionable intelligence.
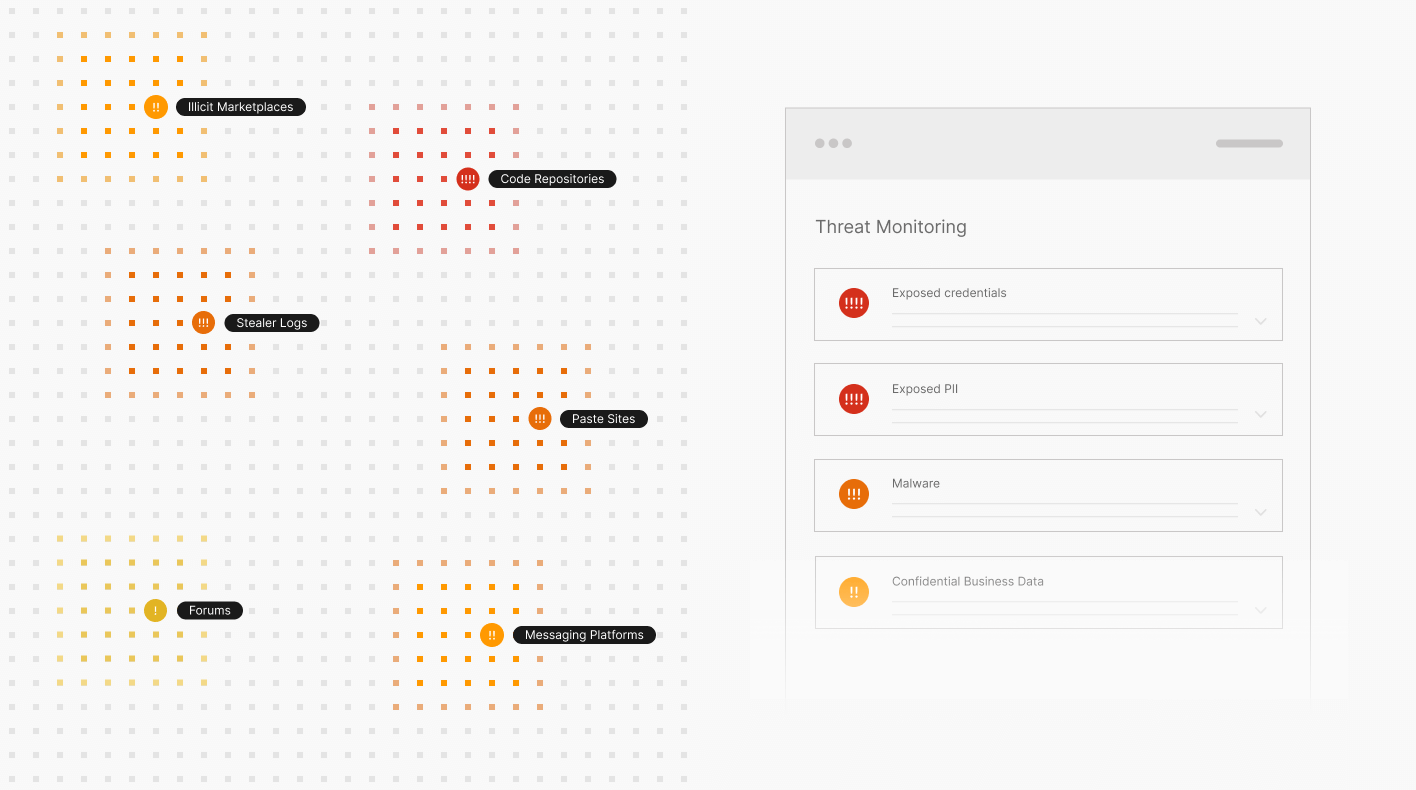
Consider Menace Monitoring as your digital menace analyst within Breach Threat. It interprets and supplies context for threats throughout your exterior assault floor, then prioritizes them by severity and supplies remediation workflows and steering. This allows your group to transition from a reactive workflow to a lean, proactive technique—addressing essential threats earlier than they change into breaches and avoiding wasted sources on low-impact alerts.
To make sure this new function actually delivers on its promise, we launched it to clients for early entry. Utilizing their suggestions, we have fine-tuned Menace Monitoring to ship on our imaginative and prescient of proactive menace detection and administration on the open, deep, and darkish net. Let’s break down the way it all works intimately.
Remodel uncooked indicators into actionable threats
Menace Monitoring is designed to empower your cybersecurity groups to maneuver from noise to readability. It achieves this by an adaptable and clever search object known as Transforms, which may be considered a superpowered “keyword search.”
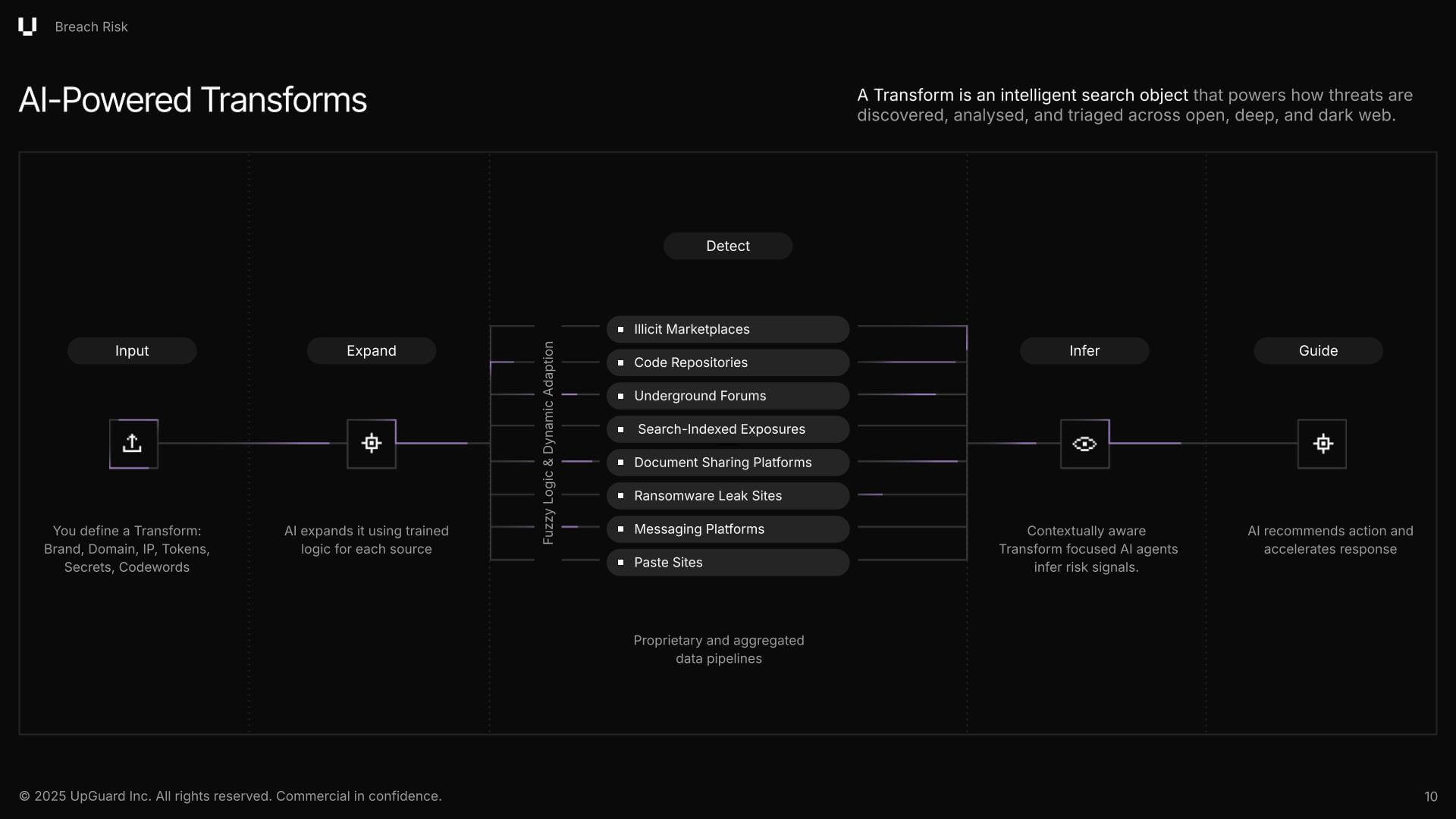
Menace Monitoring’s source-aware Transforms robotically fan out to detect exposures throughout the open, deep, and darkish net platforms. It extends its attain to platforms comparable to GitHub, Telegram, ransomware blogs, boards, and illicit marketplaces, posing a major problem for a lot of safety groups to observe.
These are usually not community logs or system alerts; they’re chaotic, decentralized platforms the place menace actors talk, commerce stolen knowledge, and plan assaults. With out specialised instruments, a safety group is actually blind to the exterior threats being deliberate towards them, however Breach Threat’s Menace Monitoring scanning finds and surfaces every match.
This final step is the place Transforms actually shine, as they’ll then interpret the context of every discovering and hyperlink it to potential enterprise dangers. So, if a flag is raised on your firm’s title being talked about in a darkish net discussion board someplace, the Remodel will interpret that context and feed it into the following core system of Menace Monitoring, which makes use of AI-powered prioritization.
Prioritize what issues with AI-powered intelligence
Now that you’ve got gotten the context surrounding your alerts because of Transforms, what’s subsequent?.
Nicely, to really achieve management, you want a approach to prioritize threats successfully with out having to manually overview all of them. And that is the place Menace Monitoring’s AI-powered prioritization function takes the reins.

Skilled by cybersecurity analysts, it analyzes every discovering and its context, offered by the Remodel, to deduce and simply talk its severity, urgency, and context. This evaluation supplies a menace severity indicator in addition to a high-level menace abstract, making it far simpler to know at a look. That is extraordinarily highly effective for cybersecurity groups managing bigger assault surfaces, as they might usually must vet every case individually, particularly in the event that they originate from sources such because the darkish net.
The AI menace abstract is nice. It’s refreshing to learn two sentences and instantly know why I ought to care a few discovering. I can have a look at a essential alert, see that it’s uncovered GitHub credentials from a pc science lab train, and transfer on inside seconds as a result of the context is true there.— Tom Grundig, Director of Info and Safety, Boston College
As an alternative of manually triaging threats, a cybersecurity specialist can merely learn a high-level menace abstract to immediately decide if a menace is pressing and requires rapid remediation. This permits for fast menace detection that leverages AI to not solely make a cybersecurity group’s job so much simpler but in addition allows them to proactively deal with threats and vulnerabilities properly prematurely.
Lastly, Menace Monitoring supplies clear, actionable remediation steering for every discovering. As soon as an alert has been contextualized and prioritized, it presents a transparent path ahead—comparable to initiating credential resets or notifying related stakeholders—permitting groups to simply plan their workflow, coordinate with different departments, and transfer from perception to remediation in a number of easy steps.
Make the shift to proactive safety
By remodeling noise into clear indicators, prioritizing what actually issues, and offering built-in remediation steering, Menace Monitoring empowers your group to maneuver past merely responding to incidents. It permits them to concentrate on significant work, strengthen their general cyber danger posture, and construct a resilient and proactive safety technique to stop threats earlier than they change into breaches.
“Security teams today are overwhelmed by fragmented alerts and lack the visibility needed to see how attackers view their organization,” mentioned Dan Bradbury, Chief Product Officer, Cybersecurity. “With Threat Monitoring in Breach Risk, our customers gain a clear, prioritized view of emerging threats, supported by AI that cuts through noise to surface real risks so teams can act faster.”
This shift from a reactive to a proactive safety posture is exactly what’s wanted in at present’s quickly evolving menace panorama throughout the open, deep, and darkish net. The increasing assault floor, the overwhelming quantity of alerts, and the fixed battle of lacking context now not should be insurmountable challenges.
For instance, as an alternative of merely being alerted to a breach after it has occurred, Menace Monitoring can proactively floor a dialog on a darkish net discussion board the place a menace actor is trying to promote credentials on your community. This permits your group to disrupt the assault, invalidate the credentials, and strengthen your defenses earlier than the menace even has an opportunity to execute.
By discovering and addressing these exterior threats at their supply, you progress from a posture of passive protection to considered one of energetic disruption.
A Essential A part of a Full Cyber Threat Answer
Menace Monitoring is a strong new functionality now accessible inside Breach Threat, but it surely’s only one piece of the puzzle. It stands as a key function inside Cybersecurity’s complete Cyber Threat Posture Administration (CRPM) platform, designed to offer a whole and unified overview of your safety panorama.
Increasing Menace Monitoring inside Breach Threat aligns with our imaginative and prescient for Cyber Threat Posture Administration. We’re serving to clients transfer from reactive alert fatigue to proactive menace detection and response whereas simplifying how they handle and report on cyber danger.– Mike Baukes, CEO, Cybersecurity.
When coupled with our different highly effective instruments, comparable to Vendor Threat and Person Threat, safety groups achieve the power to proactively safe their digital property. Breach Threat and Menace Monitoring deal with threats to your rapid exterior assault floor, whereas Vendor and Person Threat handle exterior vulnerabilities throughout your provide chain and threats inside your workforce, respectively. This highly effective mixture lets you handle safety each internally and externally from a single platform, embodying our method to holistic cyber danger posture administration.
Able to see the entire image? Request a demo or product tour at present to find how Menace Monitoring integrates with our full platform and empowers your group to maneuver past merely responding to incidents to actively stopping them.
