Cyber menace monitoring is essential for efficient cybersecurity, but most organizations function with gaping blind spots. On this put up, we shed some gentle on the constraints of standard approaches that will help you obtain complete visibility of your assault floor.
Why organizations want real-time visibility
Traditionally, menace detection was primarily reactive, counting on signature-based instruments and rule-based methods to search out identified patterns of malicious exercise in community logs and information. This method was efficient when information units have been smaller and threats have been well-documented, but it surely struggled to maintain tempo as cyber menace information complexity and quantity exploded.
The introduction of machine studying (ML) and deep studying to cybersecurity packages injected new power into detection methods, enabling safety groups to determine cyber menace patterns precisely and with the pace essential to sustain with fashionable cyber assault strategies.
Right this moment, the newest evolution of cyber menace monitoring is being formed by Synthetic Intelligence, significantly Massive Language Fashions (LLMs). This newest spherical of developments is altering detection capabilities in a number of methods:
Including Context to Detection: Whereas earlier ML fashions may flag a file as malicious, they could not clarify why. LLMs, educated on various info together with unstructured menace intelligence reviews, can now present essential context behind a call, delivering a extra knowledgeable response reasonably than only a binary alert. In consequence, cyber menace remediation actions at the moment are extra focused and being deployed sooner than ever.Comprehending Complicated Knowledge: LLMs have demonstrated a shocking skill to grasp and determine malicious exercise inside information codecs that aren’t conventional prose. This consists of log information, code, JSON, and even malware hashes, considerably increasing the scope of information that may be robotically analyzed for cyber dangers.This shift from on the lookout for identified signatures to analyzing behaviors and understanding context permits safety groups to determine and even anticipate unknown threats earlier than they’ll trigger important injury.The excessive price of dwell time
In cybersecurity, time is the attacker’s most dear useful resource. The longer they continue to be undetected inside a community, the extra injury they’ll inflict. The safety {industry} has made important progress in lowering attacker dwell time during the last decade, from 16 days in 2022 to simply 10 days in 2023. However whereas this may occasionally appear to be a powerful enchancment, 10 days remains to be an eternity for cybercriminals, particularly for individuals who have bolstered their assault strategies with Al know-how.
The essential phases of a cyber assault, reminiscent of information exfiltration by way of an SQL injection or a “smash and grab” ransomware deployment, can now happen in simply minutes or hours, making even a multi-day dwell time far too lengthy to forestall important monetary injury.
The challenges of a contemporary dynamic assault floor
The widespread adoption of cloud-based structure, the permanence of distant work, and the rise of dynamic virtualized property have dissolved conventional community boundaries, making a perimeter-less actuality that introduces new and sophisticated dangers.
The assault floor now extends far past the company workplace, encompassing cloud misconfigurations, insecure residence networks, and extremely transient digital property which are tough to trace.
This expanded, dynamic assault floor creates important monitoring challenges that legacy safety instruments weren’t designed to deal with:
Visibility Gaps in IaaS/PaaS: Efficient cloud surroundings monitoring requires enabling and centrally amassing a number of log sources — reminiscent of community visitors logs, storage entry logs, and audit logs — however the high quality and availability of this information can rely closely on the group’s particular cloud subscription stage.Securing Unmanaged Gadgets: With distant and hybrid workforces, the chance shifts to particular person customers and their endpoints. Company credentials could be compromised on private or contractor gadgets used for work, particularly if these gadgets are additionally utilized in Shadow IT or Shadow SaaS practices. Securing these unmanaged “Bring Your Own Device” (BYOD) property is a serious problem, as organizations can not implement safety controls on methods they don’t personal.Monitoring Transient Digital Property: Fashionable cloud-native environments more and more use ephemeral workloads, that are transient by nature and should exist for only some minutes, for instance, an ephemeral container used for troubleshooting safe, minimal “distroless” purposes in Kubernetes. As a result of these property are so short-lived, conventional safety scanning or agent-based monitoring might miss them solely, creating blind spots the place an attacker may execute instructions or exfiltrate information with out leaving a persistent footprint.
The rising adoption of generative AI options amongst third-party distributors creates explicit monitoring challenges, particularly in Shadow IT. Watch this video to study extra.
Get a free trial of Cybersecurity >
Compliance and reputational dangers
Past the instant technical challenges, insufficient menace monitoring exposes organizations to extreme enterprise dangers, beginning with regulatory non-compliance.
A rising variety of international and industry-specific frameworks — reminiscent of GDPR, HIPAA, PCI DSS, DORA, and CIRCIA — mandate or strongly suggest the necessity for steady monitoring to guard delicate information. Nevertheless, with attackers now leveraging AI, legacy monitoring approaches can not successfully monitor for rising cyber threats, making compliance with these laws more and more tough.
Failure to sharpen monitoring capabilities with fashionable methods results in important fines and erodes model belief, a main driver of information breach prices resulting from buyer turnover and fame injury.
Important strategies to determine cyber threats
Understanding the necessity for real-time visibility is step one to enhancing cyber menace monitoring. The following step is implementing the right strategies to attain it. Transferring from idea to follow requires adopting proactive, superior strategies that align with the realities of the trendy cyber menace panorama.
You have to shift your focus from merely defending the IT perimeter to actively looking for threats that will already be working inside.
This new and improved method to cyber menace monitoring could be carried out with the next methods:
1. Undertake an “assume breach” mindset
It is time to lastly abandon the outdated “castle-and-moat” safety mannequin in favor of Zero-Belief ideas primarily based on an “assume breach” mindset.
Based on the standard “castle-and-moat” method, anybody contained in the community is trusted by default. The essential flaw on this technique is that after an attacker crosses the “moat” — whether or not by means of stolen credentials, malware, or a social engineering assault — they transition right into a reliable standing, which grants them free entry to inner purposes and delicate information.
In distinction, a contemporary Zero Belief safety framework operates on the core precept of “Never Trust, Always Verify.” This method begins with the belief {that a} breach has already occurred and that safety dangers are current each inside and out of doors the community.
No person, system, or connection is trusted by default, no matter location. As an alternative, Zero Belief requires customers to constantly confirm their id with each try and entry delicate sources.
An assume breach mindset is an ever-present philosophy, instantly carried out on the onboarding stage, the place a person’s stage of system entry is the minimal required to carry out their duties, also referred to as the Precept of Least Privilege.
An assume breach mindset may also naturally pivot your cybersecurity technique in direction of enhanced deal with mitigating insider threats, making ready the bottom for a human cyber threat administration program.
2. Monitor the darkish internet
An “assume breach” mindset requires proactive intelligence-gathering outdoors your community. A essential supply for that is the darkish internet, which hosts hundreds of illicit marketplaces and boards the place delicate company info is commonly traded or leaked following a breach.
Fashionable cyber menace monitoring entails the continual, automated scanning of those sources — together with ransomware blogs, boards, credential dumps, and encrypted messaging platforms like Telegram — to search out intelligence related to your group’s digital footprint, reminiscent of:
Leaked company or worker credentials.Uncovered delicate buyer information, just like the non-public medical information leaked within the Medibank cyber assault.Mentions of your model or executives.The sale of proprietary firm information or mental property.
The first worth of darkish internet monitoring is its perform as an early warning system of an impending breach. Many organizations battle with this facet of cyber menace monitoring. In consequence, their compromised delicate information circulates throughout darkish internet marketplaces for weeks and even months with out their information.
The destructive implications of dwell time prolong to leaks on the darkish internet. Credentials posted in an information dump could be harvested and utilized in credential stuffing assaults inside hours. By detecting this publicity in close to real-time, safety groups can take preemptive motion — reminiscent of resetting compromised passwords or notifying affected customers — earlier than the knowledge could be weaponized in an energetic assault, turning a possible disaster right into a manageable safety activity.
For useful insights on detecting breach alerts earlier than it is device late, watch this webinar.
Cybersecurity webinar: Detect information breach alerts earlier than it is too late.3. Handle human cyber dangers
Whereas exterior threats are a serious concern, the human factor stays a main consider safety incidents. Some research present human error is a trigger in as much as 95% of breaches. Fashionable menace monitoring seems to be inward to deal with this, utilizing Person and Entity Conduct Analytics (UEBA) to determine inner threats.
UEBA is a sort of safety software program that makes use of machine studying and behavioral analytics to grasp what’s “normal” inside an IT surroundings. UEBA options create a baseline image of how customers and entities (reminiscent of servers, routers, and purposes) sometimes perform by ingesting and analyzing information from a number of sources. The system then constantly screens and flags harmful deviations from this baseline in real-time, reminiscent of sudden mass information downloads, uncommon login instances, or makes an attempt to escalate privileges.
This deal with conduct makes UEBA uniquely efficient at figuring out two essential sorts of insider threats that usually bypass conventional safety instruments:
Malicious Insiders: These are approved staff or contractors trying to steal information or trigger hurt. As a result of their entry is reliable, conventional instruments might not flag their exercise. UEBA, nonetheless, can determine a person violating safety insurance policies or accessing information inconsistent with their position, even when they’ve the credentials to take action.Compromised Accounts: Happens when an exterior attacker steals a reliable person’s credentials by way of phishing or different means. The attacker’s exercise seems approved to the community, permitting them to maneuver laterally and escalate their privileges. UEBA can detect this by recognizing anomalous behaviors that deviate from the reliable person’s established baseline, reminiscent of logging in from an uncommon IP handle, accessing new methods, or downloading irregular quantities of information.UEBA aids safety groups in detecting and responding to the human vulnerabilities that trigger most safety breaches.
Finally, deploying a device like UEBA is a core part of a broader human cyber threat administration technique. By offering deep visibility into how person identities work together with purposes and information, UEBA helps safety groups detect and reply to the human vulnerabilities — malicious or unintentional — on the root of most safety breaches.
Observe: Deploying a device like UEBA is not a standalone resolution to addressing human cyber dangers. It ought to be thought of a part of a broader human cyber threat administration technique.
Watch this video to discover ways to method human cyber threat administration holistically:
Get a free trial of Cybersecurity >
4. Leverage community visitors evaluation (NTA)
Analyzing information flows and packet metadata with Community Visitors Evaluation (NTA) can reveal hidden anomalies that conventional firewalls may miss. By monitoring east-west (inner) visitors, not simply north-south (inbound/outbound), safety groups can determine malicious patterns that point out an energetic compromise.
Key patterns NTA can detect embody:
Ransomware: A sudden surge in east-west visitors exhibiting fast file entry and encryption throughout a number of servers strongly signifies a ransomware assault in progress.DDoS Assaults: NTA can spot the anomalous spikes in UDP, ICMP, or SYN packets focusing on particular providers that characterize a Distributed Denial-of-Service assault.C2 Communication: NTA is essential for detecting the refined “beacons” or “heartbeats” that malware sends to exterior command-and-control (C2) servers, a typical tactic for sustaining persistence and receiving directions.5. Automate endpoint detection and response (EDR/XDR)
Fashionable Endpoint Detection and Response (EDR) platforms go far past legacy antivirus by specializing in malicious conduct reasonably than simply identified file signatures. This behavioral method permits them to detect superior threats like fileless malware and malicious PowerShell scripts that conventional instruments typically miss. EDR options constantly report actions and occasions on endpoints like laptops and servers, offering safety groups with the visibility wanted to uncover stealthy assaults.
A key benefit of recent EDR and Prolonged Detection and Response (XDR) platforms is their use of automation to speed up response. When a menace is detected, the EDR device can robotically comprise a compromised endpoint by isolating it from the community. This swift, instantaneous motion stops an assault from spreading and considerably reduces the guide triage workload for the Safety Operations Middle (SOC) workforce, enabling sooner and extra exact remediation.
4. Incorporate AI-driven menace Intelligence
The sheer quantity of safety logs a contemporary enterprise generates makes guide evaluation unattainable. Synthetic intelligence is now an essenital support for parsing by means of these huge information repositories to determine menace patterns precisely and at scale.
Massive Language Fashions (LLMs) can comprehend and analyze all kinds of codecs past easy textual content, together with log information, code, scripts, and JSON information. With the potential of working with a broader information context and considerably sooner processing speeds, AI know-how is the important thing to considerably lowering dwell time and its related injury prices.
The findings of the 2025 Price of a Knowledge Breach report verify AI’s consequential affect in cybersecurity. World information breach prices have declined for the primary time in 5 years resulting from sooner containment pushed by AI-powered defences.
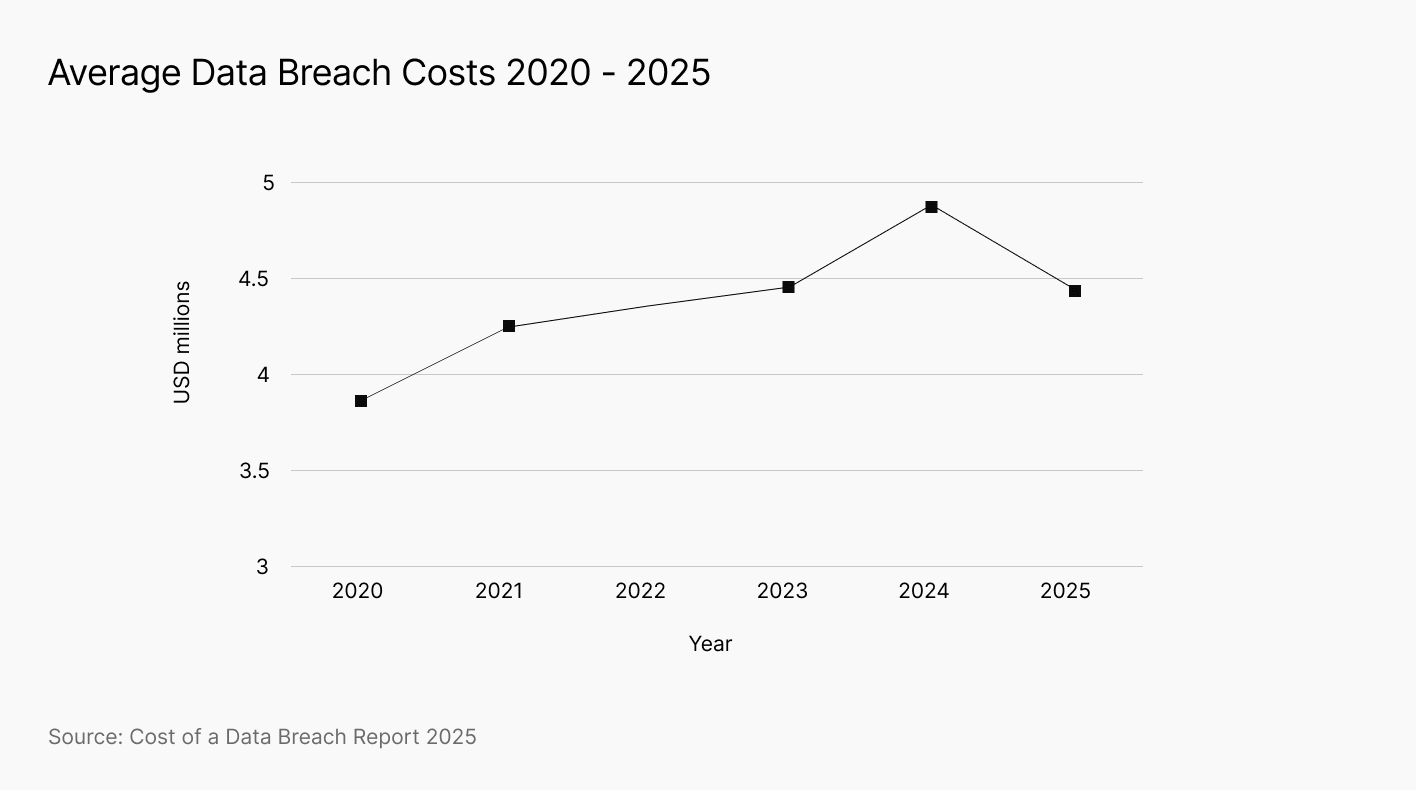 The typical price of an information breach has declines for the primary time since 2020.Important instruments for steady monitoring
The typical price of an information breach has declines for the primary time since 2020.Important instruments for steady monitoring
A contemporary cyber menace monitoring technique depends on an built-in safety stack the place key applied sciences work collectively to offer complete visibility and automate response. Understanding how these core platforms perform is step one towards constructing a resilient and environment friendly monitoring operation.
SIEM and SOAR platforms
On the core of many fashionable Safety Operations Facilities (SOCs) are two complementary platforms:
Safety Info and Occasion Administration (SIEM)Safety Orchestration, Automation, and Response (SOAR)
Collectively, they kind the muse for centralized detection and automatic motion.
Safety Info and Occasion Administration (SIEM) serves because the central nervous system for safety operations. It aggregates log information from throughout the whole IT surroundings — together with networks, cloud infrastructure, and endpoints — to detect anomalies and generate alerts.
A SOAR platform acts because the muscle, taking the alerts generated by the SIEM and robotically executing response actions by means of pre-defined “playbooks”. This will embody actions like isolating a compromised endpoint, blocking a malicious IP handle, or making a ticket for an analyst to research additional.
The first perform of a SIEAM-SOAR mixture is to speed up the incident response lifecycle, immediately shrinking the Imply Time to Detect (MTTD) and Imply Time to Reply (MTTR), which in flip minimizes the monetary and operational influence of a cyber assault.
The first perform of a SIEAM-SOAR mixture is to speed up the incident response lifecycle, immediately shrinking the Imply Time to Detect (MTTD) and Imply Time to Reply (MTTR), which in flip minimizes the monetary and operational influence of a cyber assault.
 Each SIEM and SOAR are recognized as the highest elements in lowering common information breach prices in 2025. Assault floor administration
Each SIEM and SOAR are recognized as the highest elements in lowering common information breach prices in 2025. Assault floor administration
Efficient cyber menace monitoring requires an entire and correct understanding of your group’s digital footprint from an attacker’s perspective. Assault Floor Administration (ASM) platforms present this important exterior view by constantly discovering, analyzing, and monitoring all of a corporation’s internet-facing property. These platforms are designed to search out exposures earlier than attackers can exploit them, robotically scanning for dangers like:
Unknown and untracked property, together with shadow IT and forgotten subdomains.Uncovered providers and open ports.Identified software program vulnerabilities and misconfigurations.Unsecured AI or LLM endpoints.
Fashionable safety methods acknowledge that a corporation’s threat just isn’t confined to its infrastructure; it extends to its complete provide chain. Due to this, siloed safety instruments can create harmful blind spots. A complete monitoring program requires a unified platform that mixes exterior ASM for a corporation’s personal property, and people of throughout their provide chain with Third-Social gathering Danger Administration.
Platforms like Cybersecurity present this steady, exterior visibility, permitting safety groups to find and prioritize dangers throughout their full digital footprint in addition to the assault surfaces of their distributors, all from a single location
Watch this video to find out how Cybersecurity approaches Assault Floor Administration:
Get a free trial of Cybersecurity >
Identification and entry administration options
A strong Identification and Entry Administration (IAM) framework is a cornerstone of recent menace monitoring. It’s designed to make sure that solely the correct folks and gadgets can entry the correct sources.
A essential part of IAM is implementing the precept of least privilege, which dictates that customers are granted solely the minimal entry rights essential to carry out their assigned features. This follow is essential for limiting the “blast radius” of a safety breach. When an attacker compromises an account, a least-privilege mannequin severely restricts their skill to maneuver laterally, escalate privileges, and entry delicate information, successfully containing the menace from the outset.
Past entry controls, fashionable IAM options are integral to a proactive monitoring technique. Since stolen credentials stay a prime preliminary an infection vector for attackers, implementing proactive safety measures is important.
This consists of:
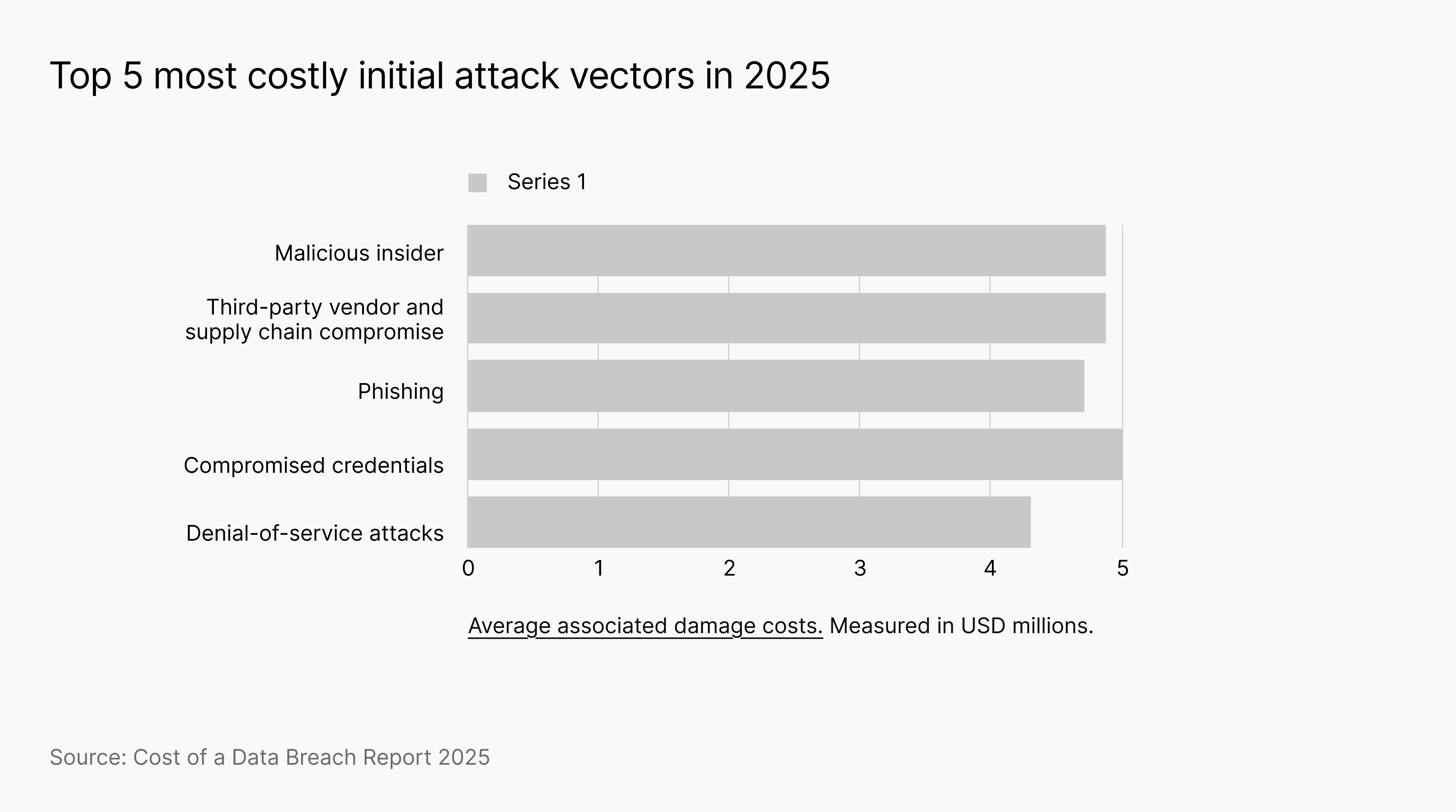
Implementing Phishing-Resistant Multi-Issue Authentication (MFA): Safety consultants strongly advocate shifting past easy MFA strategies to phishing-resistant choices like FIDO2 safety keys or certificate-based authentication. These strategies are designed to thwart social engineering and credential theft assaults that may bypass weaker MFA implementations.Steady Credential Monitoring: Fashionable safety platforms constantly monitor the darkish internet for leaked company credentials. This serves as an important early warning system, permitting safety groups to detect when an worker’s password has been uncovered in a third-party breach and pressure a reset earlier than it may be used maliciously. Compromised credential monitoring has develop into a staple function of cyber menace detection instruments. Prime 5 most expensive iniital assault vectors in 2025.AI-powered intelligence and triage
Prime 5 most expensive iniital assault vectors in 2025.AI-powered intelligence and triage
Maybe essentially the most important evolution in menace monitoring is utilizing synthetic intelligence to automate the labor-intensive strategy of menace triage. Fashionable AI, particularly Massive Language Fashions (LLMs), can now perform as a digital Tier-1 analyst, sifting by means of immense volumes of information to floor solely essentially the most essential, related threats with the context wanted for fast response.
An AI-driven triage system automates the end-to-end strategy of figuring out and making ready threats for remediation.
These platforms are designed to:
Constantly Scan and Gather Knowledge: They robotically monitor numerous sources, together with darkish internet boards, ransomware blogs, paste websites, credential dumps, and malware logs.Analyze and Prioritize Threats: Utilizing machine studying, the system analyzes findings and classifies them primarily based on confidence stage, relevance to the group, and potential influence.Suppress Noise and Cut back Alert Fatigue: A significant problem with menace monitoring is the sheer quantity of irrelevant chatter. AI-driven methods intelligently filter out duplicates, stale information, and low-confidence findings to current a curated stream of actionable intelligence, permitting safety groups to deal with what issues.Combine with Workflows: Findings are offered with context and built-in into remediation workflows the place analysts can assign possession, touch upon findings, and monitor progress, reworking uncooked information right into a structured incident response.
The strategic advantages of this method are substantial, together with sooner cyber menace detection, a major discount in noise, improved accuracy from ML fashions educated on huge datasets, and contextual intelligence that permits extra knowledgeable selections.
Automating knowledgeable analyst duties with LLMs
Fashionable LLMs can now carry out particular, advanced duties that have been as soon as the unique area of human cyber menace analysts. These capabilities are outlined in CTIBench, a benchmark designed to judge Massive Language Fashions (LLMs) in Cyber Risk Intelligence (CTI) purposes.
CTIBench includes 4 cyber menace analyst duties:
CTI-MCQ: A multiple-choice query dataset assessing LLMs’ understanding of CTI requirements, threats, detection methods, mitigation plans, and finest practices, primarily based on authoritative sources like NIST, MITRE, and GDPR.CTI-RCM: A activity requiring LLMs to map Frequent Vulnerabilities and Exposures (CVE) descriptions to Frequent Weak spot Enumeration (CWE) classes, evaluating their skill to categorise cyber threats.CTI-VSP: A activity involving calculating Frequent Vulnerability Scoring System (CVSS) v3 scores, testing LLMs’ skill to evaluate the severity of cyber vulnerabilities utilizing metrics like Assault Vector and Confidentiality Affect.CTI-TAA: A activity the place LLMs analyze menace reviews to attribute them to particular menace actors or malware households, assessing their skill to determine correlations primarily based on historic menace conduct.
Whereas efficiency varies, benchmark checks present that main fashions are already competent, with a transparent benefit for fashions which are both very giant or particularly educated on safety information.
LLM Mannequin
Efficiency Abstract
Particular Duties / Notes
ChatGPT-4
Prime Performer
Outperformed all different fashions on most duties, together with A number of Alternative Questions (CTI-MCQ), Root Trigger Mapping (CTI-RCM), and Assault Method Extraction (CTI-ATE). It additionally achieved the very best accuracy for appropriately figuring out menace actors (CTI-TAA).
Gemini-1.5
Robust on Particular Duties
The highest-performing mannequin for Vulnerability Severity Prediction (CTI-VSP), which entails predicting CVSS scores, was similar to LLAMA3-70B, though the latter outperformed it on three duties.
LLAMA3-70B
Excessive-Performing Open-Supply Mannequin
Carried out comparably to the industrial mannequin Gemini-1.5 and outperformed it on three of the 5 benchmark duties. It struggled with the Vulnerability Severity Prediction (CTI-VSP) activity.
ChatGPT-3.5
Mid-Tier Performer
Efficiency was higher than that of the smaller LLAMA3-8B mannequin, however the bigger fashions usually surpassed it throughout most benchmark duties.
LLAMA3-8B
Restricted on Complicated Duties
As a smaller mannequin, it couldn’t match the efficiency of bigger fashions on duties that required extra nuanced reasoning and understanding. Nevertheless, it nonetheless carried out decently on the CTI-MCQ activity.
All Fashions (Normal Discovering)
Susceptible to Related Errors and Overestimation
The bigger fashions (ChatGPT-4, Gemini-1.5, and LLAMA3-70B) typically made related errors when answering questions. All examined fashions incorrectly answered a shared set of 293 questions, significantly these about mitigation, instruments, and adversary strategies. Moreover, all fashions tended to overestimate the severity of threats within the CTI-VSP activity.
Greatest practices to strengthen cyber defenses
Safety leaders should combine these instruments right into a strategic monitoring program constructed on proactive discovery, documented response plans, and fixed validation to remain forward of a brand new age of sooner and extra environment friendly breach ways.
1. Leverage AI and LLMs to scale menace monitoring
The continuing cybersecurity abilities scarcity stays a serious problem, with over half of breached organizations reporting excessive ranges of staffing shortages..
AI and LLMs supply a strong resolution to this downside by appearing as a pressure multiplier for safety groups. Fashionable LLMs can now carry out many duties {that a} cyber menace analyst would sometimes deal with, reminiscent of gathering various menace intelligence, analyzing it for relevance, and correlating it with potential threats of their community surroundings.
This evaluation, which may take a human analyst hours, can typically be accomplished by an LLM in seconds. By leveraging these instruments to automate routine evaluation and intelligence gathering, safety groups can scale their monitoring capabilities, liberating human consultants to deal with extra advanced investigations and strategic protection.
2. Mapping the digital footprint
A core precept of cybersecurity is that you simply can not defend what you are unaware of. A foundational finest follow is the proactive and steady discovery of each asset throughout your group’s digital footprint.
This course of should transcend periodic scans to offer a real-time stock of all {hardware}, software program, cloud situations, domains, IP addresses, and SaaS purposes. Sustaining a present, robotically up to date asset stock is essential to making ready for incident response and serves as the muse for the whole safety program.
Be taught extra about a few of the prime cyber menace detection instruments available on the market.
This single supply of fact is important for precisely defining the scope of cyber menace monitoring, enabling efficient vulnerability administration, and permitting incident responders to grasp the potential influence of a breach rapidly.
3. Defining incident escalation paths
Advert hoc responses to cyber threats are a recipe for failure. A essential finest follow is establishing a proper, documented Incident Response Plan (IRP) that gives a transparent roadmap for motion when an incident happens.
Based on NIST steering, this plan ought to be primarily based on a proper coverage that defines roles, obligations, and authorities throughout the group, clarifying who could make essential selections like shutting down a system.
It must also set up clear tips for prioritizing incidents and outline the communication paths for notifying management, authorized groups, and different stakeholders.
To make the plan actionable, organizations ought to create technical “playbooks” with particular, step-by-step procedures for dealing with widespread threats like ransomware or phishing. This complete course of ought to be overseen by a formally designated Pc Safety Incident Response Staff (CSIRT), which ensures that response actions are constant, coordinated, and efficient
4. Validating resilience with assault simulations
An incident response plan is barely efficient if it has been examined. To make sure readiness and construct “muscle memory,” organizations should validate their defenses and response processes by means of constant, evidence-based assault simulations.
These managed workouts are designed to disclose gaps in visibility, toolsets, and procedures earlier than an actual attacker can exploit them.
There are a number of key strategies for validating resilience:
Crimson Teaming: That is an adversarial train the place a devoted workforce simulates a real-world attacker’s ways, strategies, and procedures (TTPs) to check a corporation’s defenses beneath reasonable situations.Tabletop Workout routines: These are discussion-based situations the place safety and enterprise leaders stroll by means of a simulated incident, reminiscent of a ransomware assault, to check the decision-making and communication workflows outlined within the Incident Response Plan.Purple Teaming: Not like conventional crimson vs. blue workforce adverserial workouts, it is a collaborative method the place the crimson workforce (attackers) and blue workforce (defenders) work collectively. The crimson workforce executes particular assault strategies, and the blue workforce works to detect and reply in real-time, offering instant suggestions to enhance safety controls and tune detection guidelines on the fly.How Cybersecurity might help
Cybersecurity gives a unified platform to assist safety groups grasp the challenges of recent menace monitoring. The platform combines proactive exterior assault floor administration with superior menace intelligence to offer a single, complete view of your group’s threat.
Cybersecurity’s AI-Pushed Triage can automate the detection and prioritization of exterior threats. This consists of monitoring for:
Leaked company and worker credentials on the darkish internet.Uncovered buyer or proprietary firm information.Mentions of your model on illicit boards and marketplaces.
Inside the platform, Cybersecurity’s AI Risk Analyst acts as a digital Tier-1 SOC analyst, streamlining your safety operations by:
Mechanically filtering and prioritizing threats throughout the darkish internet, ransomware leaks, credential dumps, and malware logs.Suppressing noise and false positives, surfacing solely high-confidence, actionable threats to cut back alert fatigue.Offering a collaborative investigation workspace with audit trails, proprietor assignments, and remediation monitoring to speed up triage and response.
By unifying exterior visibility with automated intelligence and a collaborative workflow, Cybersecurity empowers safety groups to maneuver from a reactive to a proactive protection, lowering threat and constructing a extra resilient safety posture.
