On April 4, 2025, The Australian Monetary Overview reported on a set of credential abuse assaults concentrating on a number of Austrian superannuation funds. These assaults weren’t breaches of the infrastructure of these firms, however compromises of particular person buyer accounts by way of stolen credentials. How had been these buyer credentials stolen? The Cybersecurity Analysis workforce in contrast the variety of affected accounts to the variety of buyer identities in infostealer logs over the previous yr and located proof that this widespread technique of credential compromise might have contributed to the account breaches. Moreover, it means that efficient monitoring of darkish internet information might help stop such assaults from succeeding sooner or later.
A Coordinated Assault on Superannuation Funds
As reported by the AFR, “major industry funds Australian Retirement Trust, AustralianSuper, REST and Hostplus were all breached. Insignia, the owner of the 180-year-old MLC brand and the largest retail superannuation fund, also suffered a cyberattack.”
Not all firms have been affected equally. To this point solely AustralianSuper has confirmed clients shedding cash–round $100,000. The opposite funds have reported attackers concentrating on buyer accounts however no losses. As we are going to see, AustralianSuper can be the corporate with the best publicity of buyer passwords by way of infostealers.
Along with disclosing whether or not clients misplaced any cash, a number of funds additionally shared the variety of buyer accounts impacted within the assaults. The AFR reported 600 AustralianSuper accounts breached, 100 Insignia accounts, and as much as 8000 REST accounts. Realizing the approximate variety of accounts affected for every tremendous permits us to check that quantity to the variety of buyer passwords stolen by infostealer malware to find out whether or not that may be a believable vector on this assault.
The Rising Risk of Infostealer Malware
The variety of accounts breached within the coordinated assault on these Australian superannuation funds is strikingly much like the variety of customers for every service in stealer logs over the past yr.
Evaluating Affected Accounts to Compromised Customers
To start out, we queried stealer logs together with the login domains for every of the affected tremendous. Insignia is right here represented by their superannuation model mlc.com.au. The member login for REST is on the area aas.com.au.
Distribution of general variety of infostealer information for every superannuation fund Distribution of distinctive customers in infostealer information by firm
Distribution of distinctive customers in infostealer information by firm
AustralianSuper had a reported 600 clients affected within the assault; over the past yr, that they had about 1000 buyer credentials uncovered by way of stealer logs. Insignia (MLC) reported 100 clients affected with about 150 buyer credentials uncovered. These two units of numbers are proportionally very related, and once we issue within the assumption that a few of these credentials would have been modified within the final yr, absolutely the numbers are fairly shut as properly. Primarily based on the information from these incidents, the variety of clients in infostealer information is a helpful predictor of variety of buyer accounts impacted in an assault.
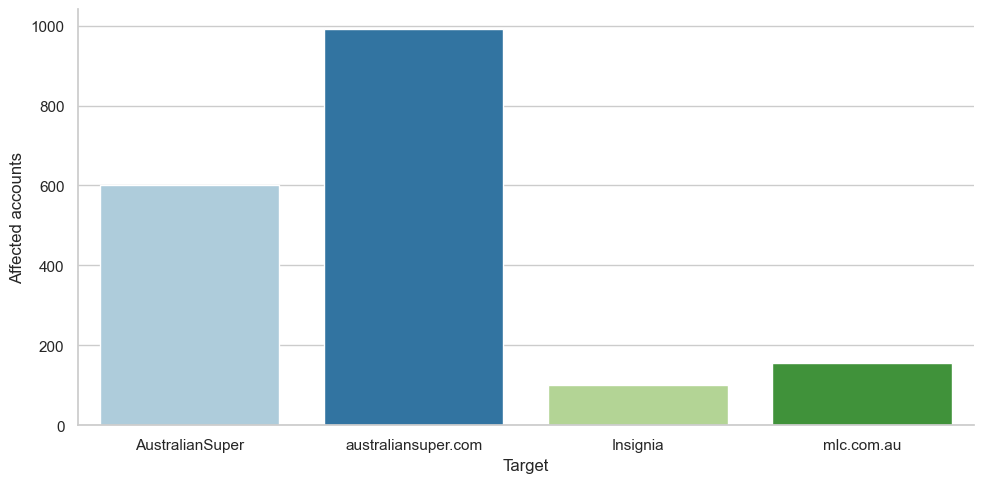 Comparability of accounts affected vs customers in stealer logs for AustralianSuper and Insignia Monetary
Comparability of accounts affected vs customers in stealer logs for AustralianSuper and Insignia Monetary
The variety of accounts reported by REST (aas.com.au), however, is way increased than the variety of buyer passwords in stealer logs and about ten instances the variety of accounts affected at AustralianSuper. REST reported 8000 accounts affected; we see nearer to 700 buyer passwords within the stealer logs. This discrepancy might point out that these accounts had been being focused with extra brute power assaults like password spraying, or that the opposite superannuation funds who reported a lot decrease numbers had been successfully capable of filter out these assaults and didn’t depend them within the variety of clients impacted.
What Firms Can Do
With out realizing the identities of the individuals affected, there is no such thing as a solution to verify whether or not the credentials in these stealer logs correspond to the people affected. Nevertheless, once we see two firms the place the variety of affected accounts is so near the variety of identities uncovered, it’s clear why monitoring for infostealer publicity has change into a must have functionality for menace intelligence groups. Buyer credentials are being traded for lots of of shoppers of those superannuation funds yearly. Firms can monitor for these exposures and cut back the probability of affect to their clients.
Moreover, multi-factor authentication is an important protection in opposition to account compromise. There are not any silver bullets, however MFA introduces a major barrier to abusing credentials. MFA ought to be a requirement for any software with entry to something of worth, whether or not that be delicate private data, company secrets and techniques, or financial institution funds. These assaults ought to serve as an example why each multifactor authentication and strong menace monitoring are worthwhile practices to keep up buyer belief.
Prepared to save lots of time and streamline your belief administration course of?

