For those who’re a Google Chrome consumer, you’ll have acquired the pop-up alert “Your password was exposed in a non-Google data breach” in your internet browser. The alert informs customers of any latest safety breaches which can have compromised their account passwords.
Step 1: Use Password Checkup to See which Password was Compromised
The very very first thing it is best to do is to examine the safety standing of all of your saved password in Google’s Password Supervisor. This function
Entry Password Checkup immediately right here.
In case you have any compromised passwords, you will note a message like this (it would additionally present the variety of passwords which were compromised):
Click on the drop-down to see all your comprised passwords. Click on the Examine Passwords button on the Password Checkup web page.Step 2: Instantly Replace all Compromised Passwords
Click on the Examine Passwords button on the Password Checkup web page.Step 2: Instantly Replace all Compromised Passwords
Click on ‘Change Password’ for all compromised passwords. If you click on this button, you can be directed to the web site related to that account.
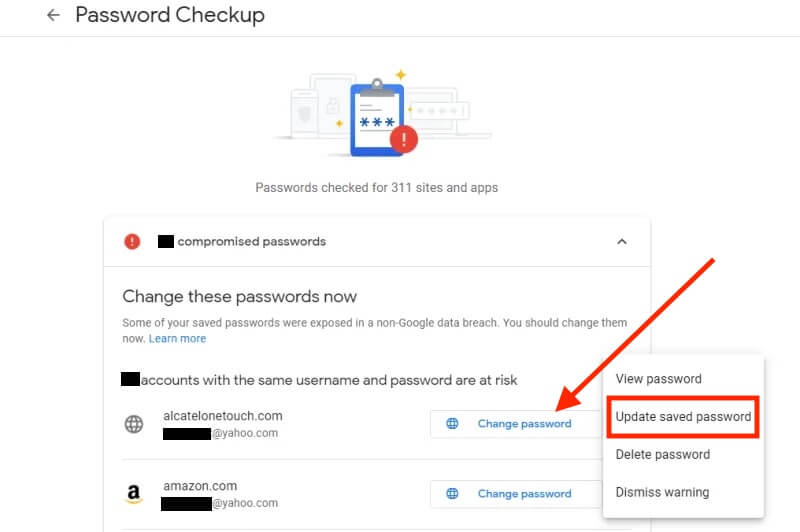
Log into the web site that masses and instantly change your password. Be sure you select a robust password to maximise cybersecurity.
As soon as up to date, click on the Examine Remaining Passwords button to return to your compromised passwords listing in Google’s password supervisor.
Proceed till all compromised passwords have been up to date.
Step 3: Replace all Weak and Reused Passwords
Weak and reused passwords put you at a really excessive danger of getting compromised in a knowledge breach. Even when a robust password is reused, if it was concerned in a earlier knowledge breach, cybercriminals might discover it on the darkish internet and compromise the entire accounts that use it.
Click on on the drop-down arrow.Click on on Change PasswordLog into the web site that masses and create a brand new password.Return to Google’s password checkup web page and work down the listing.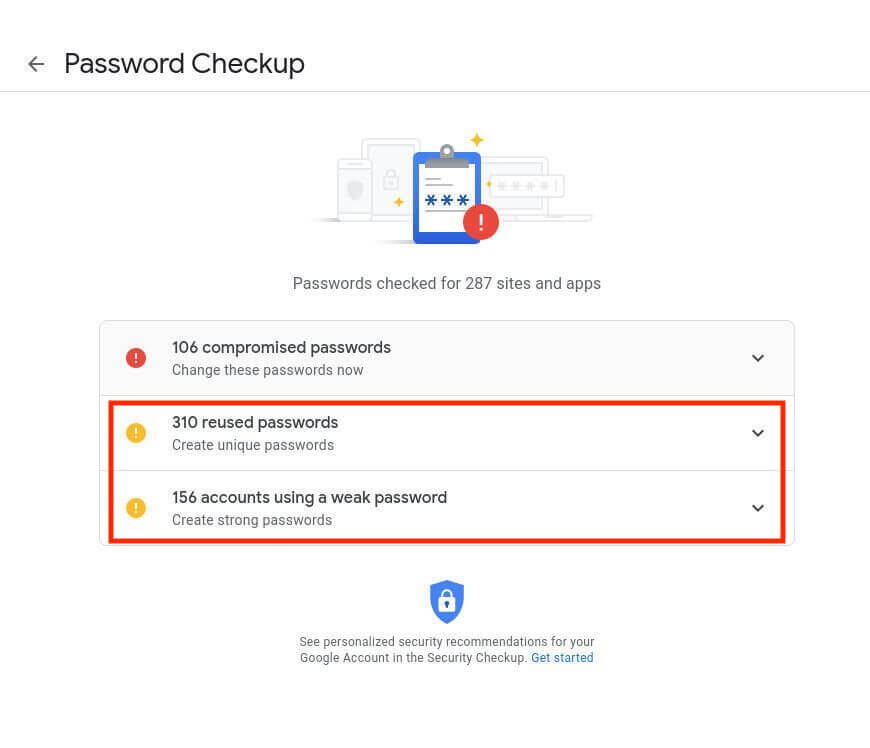 By no means reuse passwords. It’s good safety follow to all the time create distinctive robust passwords for all your accounts.
By no means reuse passwords. It’s good safety follow to all the time create distinctive robust passwords for all your accounts.
Get a free analysis of your group’s knowledge breach danger, click on right here to request your on the spot safety rating now.
Confirming Compromised Passwords on the Have I been Pwned Web site
You possibly can generally affirm {that a} password has been compromised by submitting it within the pwned passwords search engine.
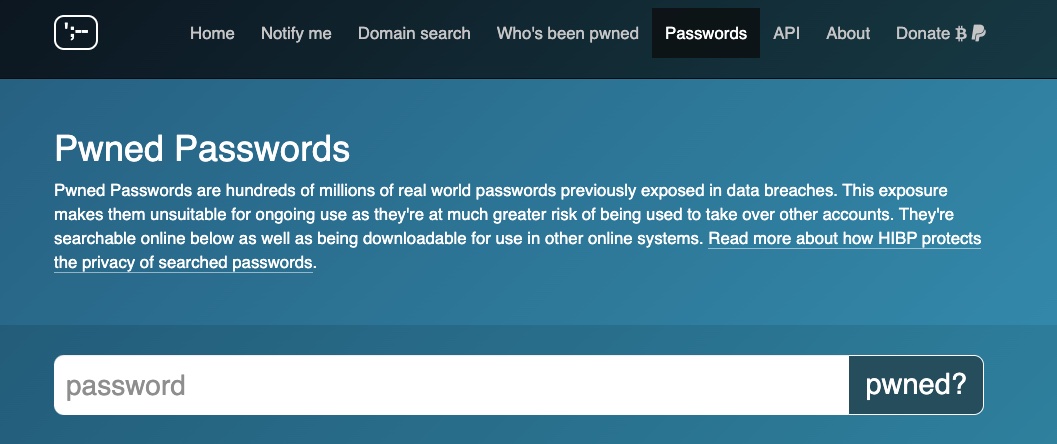
The Have I Been Pwned knowledge breach web site compares all search queries in opposition to a database of identified breaches. Nonetheless, If a breach related along with your compromised password could be very latest, you could not but be added to the Have I Been Pwned knowledge breach database. If this the case, examine once more in a number of days.
What’s Chrome’s Password Checkup Function?
First launched as a Chrome extension in February 2019, Chrome’s Password Checkup checks your username and password in opposition to over 4 billion credentials that Google has acknowledged as unsafe. Much like haveibeenpwned.com, Google identifies Gmail accounts affected by third-party knowledge breaches and accounts the place customers are re-using their Gmail passwords, to stop additional compromise.
Google launched this function as a part of its broader protection in depth technique that goals to stop, detect, and mitigate account hijacking brought on by third-party knowledge breaches.
You’ll have to entry Password Checkup to examine in case your login credentials are unsafe and take additional motion.
What Ought to I Do If My Password Has Been in a Information Breach?
In case your password has been uncovered in a knowledge breach, it is best to instantly change the password on all affected accounts. Information breaches usually happen as a way of acquiring delicate info to commit additional cybercrimes, corresponding to identification theft or fraud.
What’s a Information Breach?
An information breach is a high-risk safety incident the place delicate knowledge is compromised by an unauthorized particular person. The hacker might exploit this knowledge by accessing, copying, transmitting, viewing, or stealing it.
Information breaches generally contain the publicity of beneficial delicate info, together with:
Cybercriminals also can uncover and exploit present knowledge leaks and cloud leaks to trigger knowledge breaches.
Be taught in regards to the variations between knowledge breaches and knowledge leaks.
How Do Information Breaches Occur?
Information breaches can happen in plenty of alternative ways – both deliberately or unintentionally. There are 8 essential causes of a knowledge breach:
1. Exploiting System Vulnerabilities
2. SQL Injection (SQLI)
3. Adware
4. Phishing
5. Insecure Passwords
6. Damaged or Misconfigured Entry Controls
7. Bodily Theft
8. Third-Celebration Vendor Breaches
Find out how to Defend Your self From Information Breaches1. Safe Your Web Connection
Hackers can use specialised instruments and strategies to intercept web site visitors – that is particularly straightforward to do over public wi-fi networks. Securing your web connection gives an added layer of safety when sharing delicate info over the net, which helps stop knowledge breaches brought on by unintentionally uncovered knowledge.
2. Use Distinctive Passwords
Utilizing the identical password throughout a number of accounts has a domino impact in a knowledge breach. In case your username and password are compromised by way of one web site, they’re additionally compromised anyplace else that makes use of the identical credentials. Setting completely different passwords throughout all of your accounts ensures that any safety points will probably stay contained to the primary compromised account.
It’s tough (and unsafe) to manually monitor all your passwords to make sure they’re by no means recycled. Probably the most safe technique of protecting all your passwords robust and distinctive is with a password supervisor corresponding to 1Password.
Be taught extra about how one can create a safe password.
3. Activate Extra Authentication
Many on-line account companies now supply two-factor authentication (2FA) and multi-factor authentication (MFA). They provide further safety by requiring two or extra kinds of authentication earlier than permitting customers entry to their accounts.
Be taught extra about two-factor authentication.
4. Educate Your self
Be taught extra about how one can acknowledge phishing scams.
5. Implement Safety Controls
For those who personal a enterprise, you need to be very involved in regards to the damaging monetary impression of knowledge breaches. The next safety controls will make it easier to decrease the probability of knowledge breaches and, consequently, their related injury prices.
Get a free analysis of your group’s knowledge breach danger, click on right here to request your on the spot safety rating now.
Nicely-Identified Examples of Information Breaches Microsoft
Microsoft Linkedin
Linkedin
In April 2021, hackers carried out an unlawful knowledge scrape of LinkedIn’s consumer base, revealing the non-public particulars of over 700 million customers. This publicity enabled further cybercriminals to reap the benefits of the breached knowledge. One risk actor reportedly tried promoting a set of LinkedIn knowledge on a public discussion board for $7000 in Bitcoin.
 Yahoo
Yahoo
Between 2013 and 2016, Yahoo was hit by a number of cyber assaults. A group of Russian hackers exploited Yahoo’s database, stealing data containing private info from about 3 billion consumer accounts in complete. Yahoo’s delayed response to the assault and failure to reveal one of many safety incidents to its customers resulted in a $35 million nice and 41 class-action lawsuits.
 Equifax
Equifax
In September 2017, major credit score reporting company Equifax reported a major knowledge breach that compromised the publicly identifiable info (PII) of 148 million US residents. The breach uncovered its victims to financially-motivated crimes, together with identification theft and fraud. Equifax ultimately confronted penalties to the tune of $575 million to be paid to quite a few authorities, states and territories on account of their poor community safety.
See the entire listing of largest knowledge breaches.
Get a free analysis of your group’s knowledge breach danger, click on right here to request your on the spot safety rating now.
